Imagine you are a digital detective, on a mission to uncover hidden vulnerabilities and expose weaknesses in web applications. Armed with only a computer and a set of tools, you scour the vast expanse of the internet, searching for clues and piecing together evidence to solve the case.
Welcome to the world of bug bounty hunting, a thrilling and rewarding pursuit that allows individuals to earn money by discovering vulnerabilities in web applications. In this exciting field, one of the most essential skills a bug bounty hunter can possess is JavaScript enumeration.
JavaScript enumeration is a technique that involves using JavaScript to gather information about a web application, identify vulnerabilities, and exploit them for financial rewards. It is a powerful and versatile technique that requires a combination of creativity, analytical thinking, and persistence.
In this article, we will explore the world of JavaScript enumeration and its importance in bug bounty hunting. We will delve into the different techniques used in JavaScript enumeration, the vulnerabilities that can be identified and exploited, and the benefits of mastering this essential skill.
So sit back, grab your magnifying glass, and get ready to explore the exciting and rewarding world of JavaScript enumeration in bug bounty hunting.
Why JavaScript enumeration matters?
JavaScript enumeration is an essential skill for any bug bounty hunter who wants to uncover vulnerabilities in web applications. Not only does it require a creative and inquisitive mindset, but it also provides an opportunity to discover unique and interesting attack vectors that can be used to exploit vulnerabilities and gain access to sensitive information.
Imagine yourself as a digital detective, searching for clues and piecing together evidence to solve a case. JavaScript enumeration is your magnifying glass, allowing you to examine the intricate details of a web application and discover vulnerabilities that may be hidden in plain sight. It allows you to see the application from a different perspective and uncover flaws that may have been overlooked by others.
JavaScript enumeration is like a treasure hunt, with each vulnerability you discover being a valuable prize. It requires a combination of intuition, knowledge, and persistence to find the right clues and put them together to uncover a vulnerability. Each successful discovery is a victory, providing a sense of satisfaction and accomplishment that only comes from solving a challenging puzzle.
In addition to the excitement and satisfaction of the hunt, JavaScript enumeration is also an important skill for improving web application security. By identifying vulnerabilities and reporting them to developers, bug bounty hunters play a critical role in preventing malicious attacks and protecting sensitive data.
Let’s first discover what you could find with JavaScript Enumeration.
Fingerprinting
Fingerprinting is the process of gathering information about a web application or server. It can help you identify the operating system, web server, and other technologies used by the target. This information can be useful in finding vulnerabilities that are specific to the target.
There are several JavaScript libraries that can be used for fingerprinting, including Fingerprintjs2 and ClientJS. These libraries gather information about the browser and the user’s system and can be used to identify unique identifiers such as the browser version, screen resolution, and operating system.
Directory Enumeration
Directory enumeration is the process of discovering hidden directories on a web server. These directories may contain sensitive information or files that are not meant to be publicly accessible. To perform directory enumeration in JavaScript, you can use tools like DirBusterJS or GobusterJS.
These tools will attempt to guess the names of hidden directories by using a list of common directory names. They can also be configured to brute-force directories by trying all possible combinations of letters and numbers.
Cross-Site Scripting (XSS) Enumeration
Cross-Site Scripting (XSS) is a common vulnerability in web applications that allows an attacker to execute malicious code on a user’s browser. To find XSS vulnerabilities, bug bounty hunters can use tools like XSStrike and XSS Hunter.
XSStrike is a tool that automates the process of finding XSS vulnerabilities by sending payloads to the target and analyzing the response. XSS Hunter is a web-based tool that allows you to create custom payloads and monitor the results in real-time.
File Inclusion Enumeration
File inclusion vulnerabilities allow an attacker to include a file from a remote server into the target application. This can be used to execute arbitrary code on the server or steal sensitive information.
To find file inclusion vulnerabilities, you can use tools like LFISuite or File Include Checker. These tools will attempt to include remote files by manipulating the application’s parameters and analyzing the response.
Authentication Enumeration
Authentication is an important part of web application security. Weak authentication mechanisms can lead to account takeover vulnerabilities and unauthorized access to sensitive information.
To find authentication vulnerabilities, you can use tools like Burp Suite or OWASP ZAP. These tools can be used to intercept and modify requests, bypass login screens, and test for weak passwords.
JavaScript enumeration simplified with tools
JavaScript enumeration can be intimidating, hard or time-consuming. If that’s the case for you, maybe you are doing it the wrong way! If you jump onto random JavaScript files and look for low hanging fruits only, you might get lucky once, but you won’t find great and consistent bugs. At least you won’t cover the entire attack surface. Instead, I suggest you first extract all JavaScript files, then browse through them, and then you can focus on specific parts which seem interesting.
You can use various tools that will assist you during this exercise. These are the ones I found helpful, but if you prefer other tools, feel free to suggest others in the comments.
Step 1 in JavaScript enumeration: Extract JavaScript files
Sometimes all you have is the login page, that’s fine. Once you finish browsing all the accessible features, your web proxy should have recorded all the JavaScript files. I like to use BurpSuite Professional to extract them all at once, but you can use other alternatives, such as manually downloading all the JavaScript files from BurpSuite Community Edition (The free version of BurpSuite).
To do that, you right-click on your target root entry in the Sitemap, then choose the Find scripts option under the Engagement tools in the contextual menu.

From there, you click on Export scripts and choose a file to store them. I like to store them because I will be using the next tools to look for specific things, like endpoints, secrets, etc.
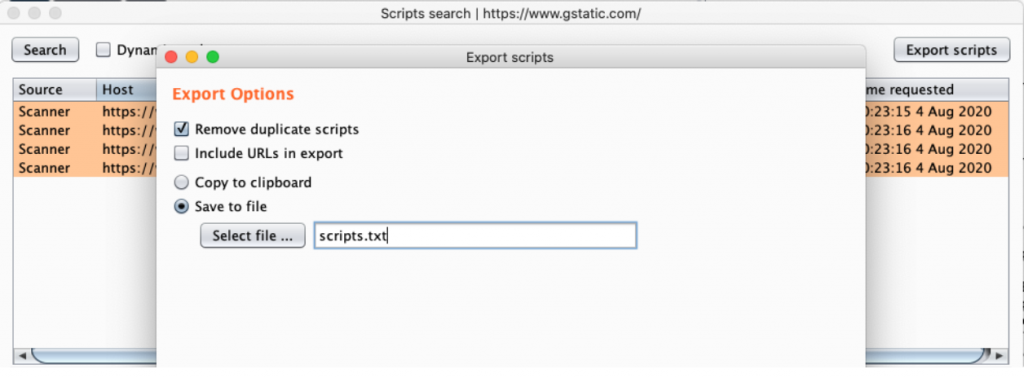
Extract JavaScript using free tools
If you have been following this blog, you know that the bug bounty community has published many awesome tools which you can combine to get the content of JavaScript files. I like to use waybackurls and the built-in bash commands xargs, curl and tee. Here is a one-liner that will do the job:
waybackurls target.com | grep "\\.js" | xargs -n1 -I@ curl -k @ | tee -a content.txt
The above one-liner will collect all publicly available JavaScript files using waybackurls. Then, it filters only JavaScript files. From there, it grabs the content of each file using curl. Finally, it stores the result in one file.
Step 2: Beautify the JavaScript code
From my experience, most of the JavaScript files get obfuscated and packed into one single line. Therefore, it’s hard to deal with them as they are. Luckily, there are tools which help at least structure them into readable JavaScript code. The one I use is Jsbeautifier, a command-line tool that accepts a file as input and beautifies its content, unpacks it or deobfuscates it into a resulting file.
First, you install it using pip: pip install jsbeautifier. Then, you run it with js-beautify -o outfile.txt scripts.txt. This will output the file outfile.txt which you can easily browse through.
It’s time for the next step: finding the juicy data we are all looking for!
Step 3: JavaScript enumeration with Grep and the family
Now that we have a readable version of all the JavaScript code in one place, I like to start with Grep to get a feel of what I am expecting. The general command is grep --color -i term outfile.txt. You just change the word term with what you’re looking for. For example, try words like secret, admin, password or token to find hardcoded secrets. Alternatively, you can use a path prefix to look for endpoints. Say you noticed that all API endpoints start with /api/v1. In this case, you can substitute the word term in the grep command with /api/v1 to collect all the API endpoints.
Once you grab some endpoints, and hopefully some secrets, you can focus on areas of interest within the JavaScript files.
Javascript enumeration using Chrome Dev Tools
If you don’t have BurpSuite Pro or you don’t want to parse the entire JavaScript files, you can use your built-in Web Browser Developer tools. I like to use the Chrome Browser.
Look for keywords across the entire website
In Chrome, you can open the Developer Tools using the shortcut Command + option + I on Mac, and Ctrl + Shift + I on Windows. From there, choose the Sources Tab. Once inside, you will see the different files in a tree on the left. Hit Command + option + F on Mac, or Ctrl + Shift + F on Windows and a search menu will appear in the bottom. Type the keywords you found from the previous steps to locate where exactly they appear in the client-side source code.
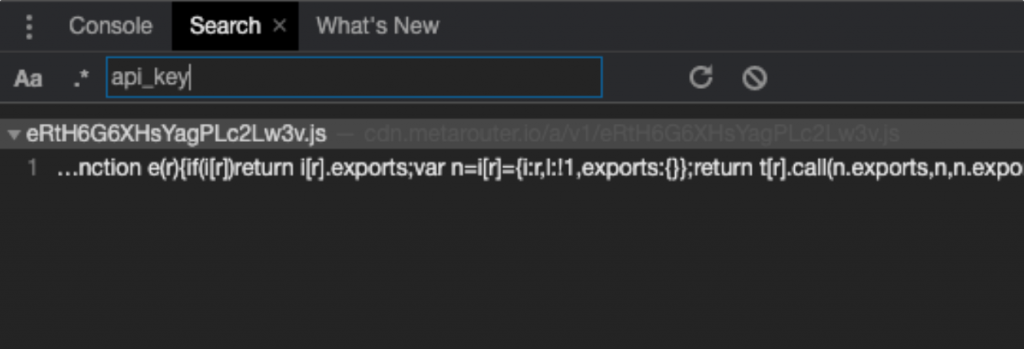
From there, click on the one on the right of the results, which will load the JavaScript file in the main screen.
JavaScript enumeration within a file in Chrome Dev Tools
Once you choose a JavaScript file, it may appear obfuscated or minified. Don’t worry, Chrome can make it readable. You just have to click on the Prety-print button. Alternatively, there is a button named {} on the bottom of the screen, which you can click as well.
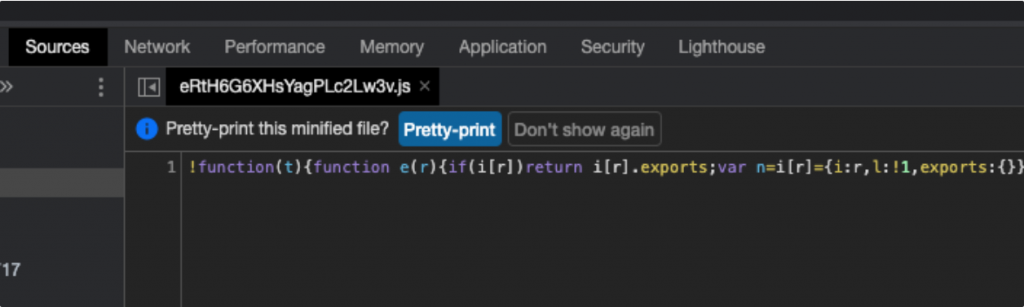
From there, hit Command + F on Mac or Ctrl + F on Windows and look for your keyword, such as api_key.

JavaScript Enumeration using breakpoints
Once you focus on a particular snippet within a JavaScript file which brings your attention, you might find it hard to understand what the code does. This can be due to random variable or function names, or simply because you can’t understand what the code does. In this case, you can set a break-point on one or multiple lines, then refresh the page.
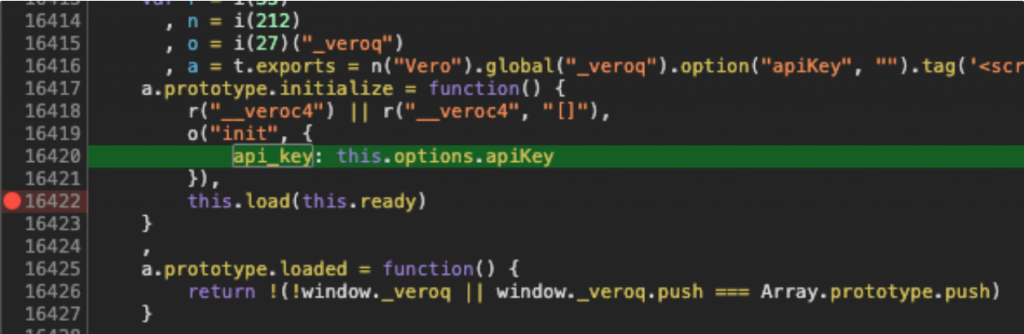
Once the client-side code hits your break-point, you can debug it like you would do in any Code Editor using the controls you have on the menu in the right.

JavaScript enumeration examples
After mapping the application, collecting all JavaScript files, looking for interesting areas and debugging the JavaScript code, it really depends on your experience and creativity to find interesting bugs. However, without the prior steps, you wouldn’t be able to focus on the areas that matter. The following are examples which illustrate what hackers have found using JavaScript enumeration.
PostMessage DOM XSS vulnerabilities
In this great article, Mathias explains how he performed JavaScript Enumeration using the very steps you discovered earlier to find and exploit a DOM XSS vulnerability due to a misconfiguration in the PostMessage event handling.
Exploit a token leak to disclose your Paypal password
This blog post explains how Alex, a Security Researcher and bug bounty hunter, could exfiltrate your Paypal password through a token leak. He started with JavaScript enumeration and found an interesting endpoint that he was able to understand and exploit.
Conclusion
In conclusion, JavaScript enumeration is a crucial skill for any bug bounty hunter looking to uncover vulnerabilities in web applications. It requires a creative and analytical mindset, as well as persistence and dedication, to identify and exploit vulnerabilities that may be hidden deep within the code.
Just like a detective in a mystery novel, a bug bounty hunter must be willing to explore every nook and cranny of the web application, looking for clues and piecing together the evidence to uncover the vulnerabilities. JavaScript enumeration provides a unique and valuable perspective on the application, allowing the bug bounty hunter to see the application from a different angle and identify vulnerabilities that may have gone unnoticed.
But bug bounty hunting is not just about finding vulnerabilities and earning rewards. It is also about making the internet a safer place for everyone. By identifying and reporting vulnerabilities to developers, bug bounty hunters play a critical role in improving web application security and preventing malicious attacks.
So whether you are a seasoned bug bounty hunter or just starting out, mastering the art of JavaScript enumeration is an essential skill that will help you uncover vulnerabilities, earn rewards, and make a positive impact on the security of the internet. Keep exploring, keep learning, and keep pushing the boundaries of what is possible with JavaScript enumeration!
