Hey there, folks! It’s Rocky here, and today we’re diving into the wild world of Active Directory. Now, you might be wondering, “What in the world is Active Directory anyway?” Well, buckle up because I’m about to give you the lowdown
So, picture this: you’ve got a big ol’ network with tons of computers, users, and all sorts of digital goodies. Keeping track of who’s who and what’s what can be a real headache, right? That’s where Active Directory swoops in to save the day.
At its core, Active Directory is like the mastermind behind the scenes, organizing everything in your network. It’s like the ultimate Rolodex, but instead of just phone numbers, it stores info on users, computers, printers, you name it. And the best part? It makes it super easy to find and manage all that stuff.
Think of Active Directory as the glue that holds your entire network together. It’s the go-to guy for authentication, letting users log in and access resources like files and printers. Plus, it keeps everything nice and secure, making sure only the right people can get their hands on sensitive stuff.
But wait, there’s more! Active Directory isn’t just about keeping things organized. It’s also a powerhouse for managing policies and permissions. Want to make sure everyone in accounting has access to the same files? No problem! Just set up a Group Policy and let Active Directory do the rest.
What is Active Directory
Active Directory is a centralized directory service developed by Microsoft, primarily used in Windows environments to manage and organize network resources. It acts as a repository for information about objects on a network, such as computers, users, groups, and printers.
At its core, Active Directory provides authentication and authorization services, allowing users to securely access network resources based on their permissions. It also facilitates resource management by enabling administrators to create, manage, and apply policies across the network.
In essence, Active Directory serves as a comprehensive tool for efficiently managing and securing a network’s infrastructure, ensuring seamless access to resources while maintaining security and compliance standards.
How does Active Directory Works

Active Directory works by serving as a central repository of information about objects on a network, such as users, computers, groups, and resources. It operates on a client-server model, where one or more servers, known as domain controllers, store and manage the Active Directory database.
Here’s a simplified breakdown of how Active Directory works:
- Domain Controllers: These are specialized servers responsible for hosting the Active Directory database and providing authentication and authorization services to network users and computers.
- Database Structure: Active Directory stores information in a hierarchical structure called a directory tree. At the top of the tree is the forest, which represents an entire collection of domains. Each domain within the forest contains objects such as users, groups, and computers.
- Objects: Objects are the fundamental units of Active Directory, representing entities such as users, groups, computers, and organizational units (OUs). Each object has attributes that define its properties and characteristics.
- Domains and Trust Relationships: Domains are units of organization within Active Directory, typically representing a group of users, computers, and resources with a common security boundary. Trust relationships between domains allow for secure communication and resource sharing across different parts of the network.
- Authentication and Authorization: Active Directory provides authentication services, verifying the identity of users and computers attempting to access network resources. Once authenticated, Active Directory checks the user’s permissions and authorizes access to the appropriate resources based on configured policies.
- Group Policy: Group Policy Objects (GPOs) are used to define and enforce settings and restrictions across the network. Administrators can configure GPOs to manage user and computer configurations, security settings, and other policies.
- Replication: Active Directory employs replication mechanisms to synchronize changes made to the directory database across multiple domain controllers within a domain or across different domains in a forest. This ensures that directory information remains consistent and up-to-date throughout the network.
Active Directory, introduced with Windows Server 2000, serves as a cornerstone in managing network resources, primarily focusing on user authentication and authorization. Let’s break down how it works using some examples.
Example 1: Authenticating Users
Jim, a new accountant at Active Directory Pro, receives a unique account created by the IT admin within Active Directory. Armed with a username and password, Jim logs into his laptop:
- Jim enters his credentials.
- The logon request travels to the Active Directory server for verification.
- Active Directory cross-references Jim’s account, confirming his credentials.
- Jim gains access to his laptop and becomes authenticated to the domain.
Example 2: Authorizing User Access
Jim, now logged in, seeks to access his email, a contract file, and the accounting database server:
- Network resources, like email and file servers, consult Active Directory to verify Jim’s access permissions.
- Active Directory confirms Jim’s authorization for these resources.
- Jim gains access to his desired resources, such as email and file servers, granted by Active Directory’s authorization.
Example 3: Mixed Access for Users
Pam, another user, logs in and attempts to access the same resources as Jim:
- Network resources again consult Active Directory to verify Pam’s access permissions.
- Active Directory authenticates Pam and checks her access rights.
- While Pam can access email and files, she’s denied entry to the accounting database server, as per Active Directory’s authorization settings.
In essence, Active Directory’s core function remains consistent across these examples: authenticating users’ credentials and authorizing their access to network resources. Whether granting or denying permissions, Active Directory acts as the gatekeeper, ensuring secure and controlled access throughout the network.
Major features in Active Directory Domain Services
Active Directory Domain Services (AD DS) boasts several major features that form the backbone of its functionality:
- Domains, Trees, and Forests Structure: AD DS employs a hierarchical layout comprising domains, trees, and forests to organize networked elements.
- Domains: These are the smallest organizational units and consist of objects like users and devices that share the same database.
- Trees: A collection of one or more domains grouped together, forming a logical hierarchy with hierarchical trust relationships.
- Forests: Groups of multiple trees, each forest encompasses shared catalogs, directory schemas, application information, and domain configurations. Forests provide security boundaries within AD DS.
- Domain Name System (DNS): Domains within AD DS utilize DNS to map domain names to IP addresses and facilitate network communication.
- Organizational Units (OUs): OUs are containers used to organize users, groups, and devices within domains. Each domain can have its own OUs, enabling granular management and delegation of administrative tasks. However, OUs cannot have separate namespaces, ensuring uniqueness of user and object identifiers within a domain.
- Schema: The schema defines the structure of objects within the forest, including their classes and attributes. It plays a crucial role in ensuring consistency and interoperability across the entire AD DS environment.
- Global Catalog Servers: Global catalog servers maintain a comprehensive listing of all objects within a forest, providing efficient and distributed access to directory information.
- Trust Relationships: Trust relationships establish secure connections between domains, enabling seamless authentication and resource access across different parts of the directory infrastructure.
- Group Policy Objects (GPOs): GPOs are used to enforce and manage security settings, configurations, and policies across domains and OUs. While OUs can have GPOs linked to them, containers, which are similar to OUs, do not support GPO application or linking.
These features collectively empower AD DS to efficiently manage and secure network resources, streamline administrative tasks, and facilitate seamless collaboration and communication within organizations.
Active Directory Domain Services (AD DS)
Active Directory Domain Services (AD DS) serves as the central component of Active Directory, providing essential functions vital for network management and security. Let’s break down its core functions:
- Directory Service: AD DS acts as a directory service, offering a structured method for storing and organizing data essential for network administration and access control. Within Active Directory, information pertaining to users, computers, groups, and other network resources is stored in a hierarchical and easily accessible format.
- Authentication Service: One of the primary functions of AD DS is to authenticate network users. When users attempt to access network resources, AD DS verifies their identity by validating their credentials, such as usernames and passwords, against the stored directory information.
- Authorization Service: AD DS also functions as an authorization service, determining the level of access granted to authenticated users. Based on predefined permissions and access control lists (ACLs), AD DS either allows or denies users access to specific network resources, ensuring security and data integrity.
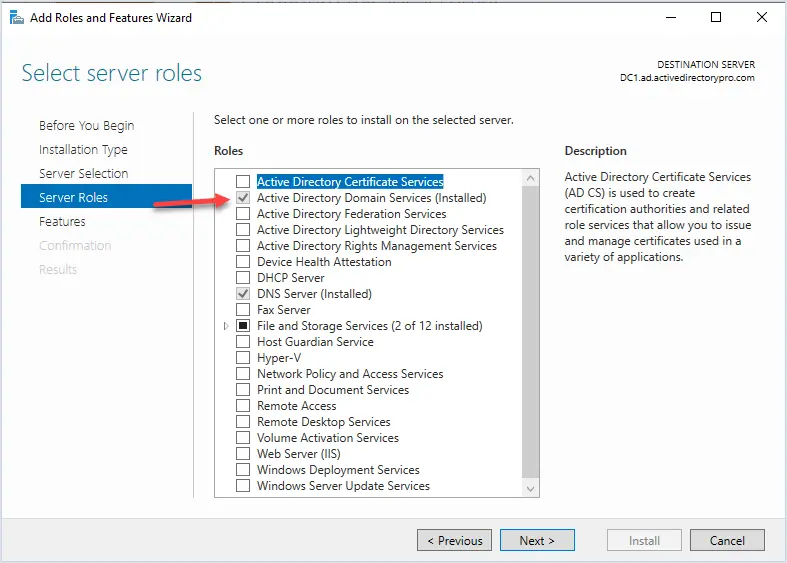
It’s important to clarify some terminology associated with Active Directory:
- AD: This is simply an abbreviation for Active Directory, referring to the overall directory service provided by Microsoft.
- AD DS: This term specifically denotes a server running the Active Directory Domain Services Role, responsible for hosting and managing the Active Directory database.
- Domain Controller (DC): Another term for a server running the Active Directory Domain Services Role. Essentially, a Domain Controller and a server running AD DS are synonymous.
When setting up Active Directory, administrators install the AD DS Role on a Windows server, effectively transforming it into a Domain Controller responsible for managing directory services within the network.
Active Directory Core Components
Active Directory is indeed a multifaceted system, consisting of various core components essential for its operation. Let’s delve into these components:
- Active Directory Domains, Trees, and Forests:
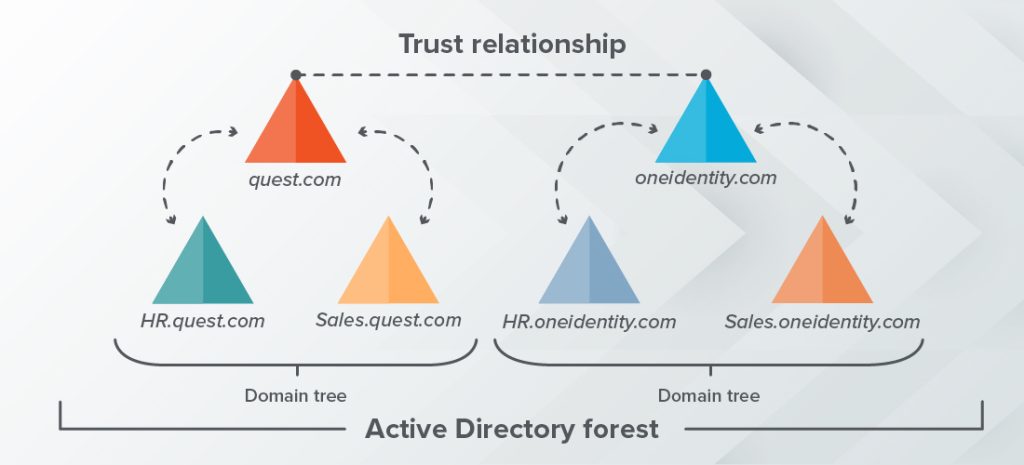
- Domains: These are the fundamental organizational units within Active Directory, containing a collection of objects like users, groups, and computers. Domains share a common directory schema, configuration, and global catalog.
- Trees: A set of one or more domains interconnected in a hierarchical structure. When domains are added as child domains to a parent domain, they form a domain tree.
- Forests: The highest level of organization in Active Directory, a forest comprises multiple domain trees sharing a common schema, configuration, and global catalog.
- Schema: A set of rules defining the structure, classes, and attributes of objects stored in the Active Directory database.
- Global Catalog (GC): A repository containing information about every object in the Active Directory forest, facilitating searches and queries across domains.
- Replication: The process of synchronizing changes made to the Active Directory database across multiple domain controllers to ensure data consistency and availability.
- Sites and Services: Logical containers representing physical locations where domain controllers are deployed. Sites optimize network traffic and replication by grouping domain controllers based on their physical proximity.
- Kerberos Authentication: The authentication protocol used by Active Directory to verify the identity of users and hosts accessing network resources.
- Flexible Single Master Operation (FSMO) Roles:
- Schema Master: Manages the read-write copy of the schema.
- Domain Naming Master: Ensures uniqueness of domain names within the forest.
- RID Master: Allocates unique security identifiers (SIDs) to objects within a domain.
- PDC Emulator: Handles authentication requests, password changes, and group policy updates.
- Infrastructure Master: Manages object references between domains.
- User Accounts: Represent individuals within the organization and provide access to network resources. User accounts contain various attributes such as name, contact details, and group memberships.
- Security Groups: Collections of users or computers used to simplify permission management by granting access rights to a group rather than individual accounts.
- Computer Objects: Represent computers joined to the Active Directory domain, serving as trusted entities for network access.
- Organizational Units (OUs): Containers used to organize and manage Active Directory objects, allowing for delegation of administrative tasks and application of policies.
These core components collectively form the foundation of Active Directory, enabling centralized management, authentication, and authorization of network resources within organizations.
Components of Active Directory
Active Directory, Microsoft’s directory service, comprises several components, each serving distinct functions within the Active Directory ecosystem. Let’s explore the key components:
- Active Directory Domain Services (AD DS):
- AD DS is the core component of Active Directory, providing centralized authentication and authorization services for users, groups, computers, and other network resources.
- It manages the directory database, which stores information about objects within the network, including user accounts, group memberships, organizational units, and domain trust relationships.
- AD DS enables administrators to define and enforce security policies, manage access permissions, and streamline resource management across the network.
- Active Directory Certificate Services (AD CS):
- AD CS facilitates the deployment and management of digital certificates within the Active Directory environment.
- It supports various certificate-based security solutions, including secure email communication, SSL/TLS encryption for web servers, smart card authentication, and virtual private networks (VPNs).
- AD CS allows organizations to issue, renew, revoke, and manage certificates, ensuring secure communication and authentication between network entities.
- Active Directory Federation Services (AD FS):
- AD FS enables single sign-on (SSO) and identity federation across multiple trusted domains, forests, or external identity providers.
- It establishes trust relationships between different security realms, allowing users to access resources seamlessly without requiring separate authentication credentials.
- AD FS supports federated authentication protocols such as Security Assertion Markup Language (SAML) and OAuth, facilitating interoperability and integration with cloud-based services and applications.
- Active Directory Lightweight Directory Services (AD LDS):
- AD LDS provides a lightweight directory access protocol (LDAP) directory service that is independent of the Active Directory domain structure.
- It allows organizations to deploy directory services for specific applications or scenarios without the need for a full-fledged domain infrastructure.
- AD LDS is often used to store application-specific data, user profiles, or directory information for non-Windows platforms or legacy applications.
- Active Directory Rights Management Services (AD RMS):
- AD RMS enhances data security by enabling organizations to protect sensitive information through encryption, access controls, and rights management policies.
- It allows users to apply restrictions to documents and emails, such as preventing unauthorized access, copying, printing, or forwarding of sensitive content.
- AD RMS integrates with Active Directory to enforce access policies based on user permissions, group memberships, or organizational policies.
These components collectively contribute to the functionality, security, and scalability of Active Directory, making it a comprehensive directory services solution for managing identity, access, and information within enterprise environments.
Benefits of Using Active Directory
One significant benefit of using Active Directory is its centralized management of network resources, which streamlines administration, enhances security, and improves efficiency.
Centralized Management: Active Directory provides a single, unified platform for managing user accounts, computers, groups, and other network resources. This centralized approach simplifies administrative tasks such as user provisioning, group policy management, and access control, reducing the overhead associated with managing disparate systems.
Enhanced Security: Active Directory offers robust security features such as authentication, authorization, and encryption to protect sensitive data and resources. By enforcing security policies and access controls centrally, administrators can ensure that only authorized users have access to critical information, reducing the risk of unauthorized access or data breaches.
Efficient Resource Allocation: With Active Directory, administrators can assign permissions, deploy software, and configure settings across multiple devices and users simultaneously, saving time and effort. Group policies enable administrators to enforce consistent configurations and security settings across the network, reducing the risk of configuration errors or inconsistencies.
Improved User Experience: Active Directory’s single sign-on (SSO) capability allows users to access multiple applications and services with a single set of credentials, improving productivity and user experience. Users can seamlessly access resources within the network without the need to remember multiple passwords or log in multiple times.
Scalability and Flexibility: Active Directory is designed to scale with the growth of an organization, supporting thousands of users, devices, and resources within a single domain or across multiple domains in a forest. Its flexible architecture allows organizations to adapt to changing business needs and IT environments, making it suitable for small businesses as well as large enterprises.
Management Tools
On the server running Active Directory, you can access these management tools under the “Windows Administrative Tools” folder. You can also install these tools on another computer by installing the RSAT tools.
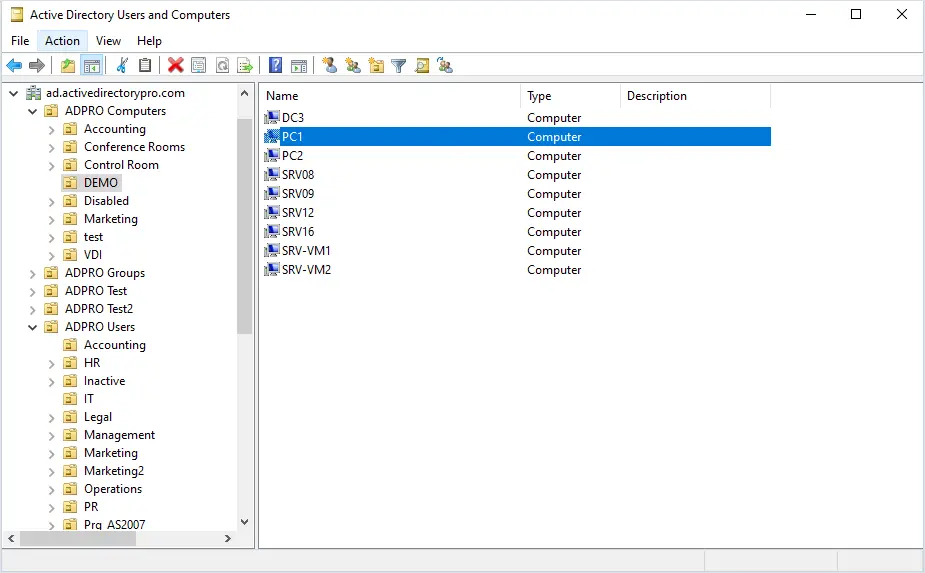
Active Directory Users and Computers (ADUC)
This is the console that is used to create and manage user accounts, computers, and groups. For example, to create a new user account you would open the ADUC console to create the new account, set the password, and add the user to groups. It is also used to create OUs and organize your objects.
Active Directory Administrator Center (ADAC)
The ADAC tool was included with server 2008 R2 and higher. It performs many of the same tasks as ADUC and a few additional ones. I’m not sure if Microsoft meant for this to replace ADAC but it is not widely used. Most administrators still use the ADUC tool.
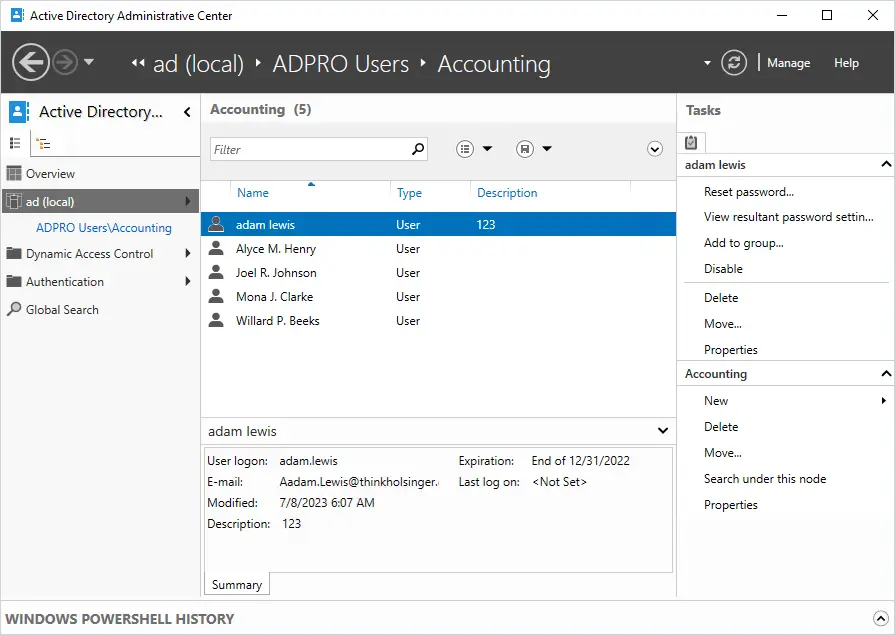
Active Directory Domains and Trusts
This console is used to raise the domain mode or functional level of a domain or forest. It is also used to manage trust relationships. This console is one you will not use very often.
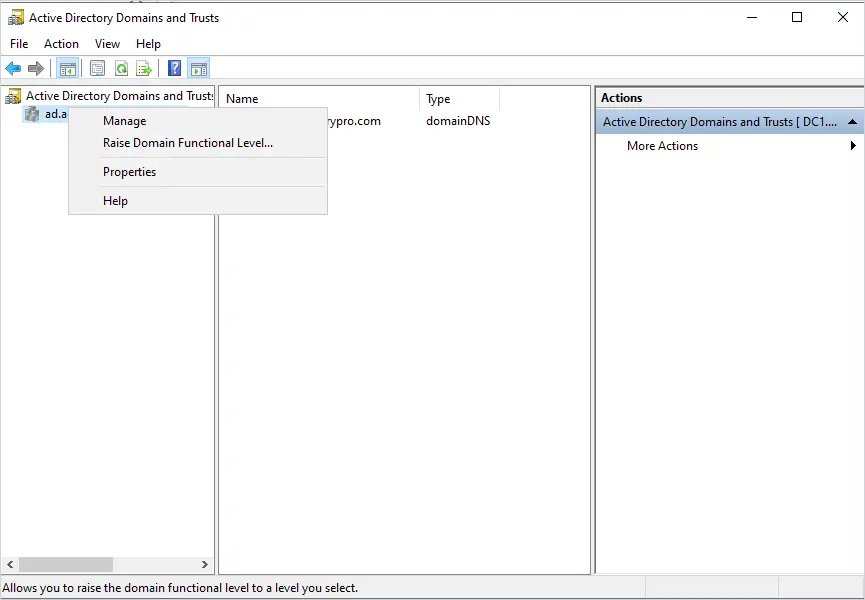
Active Directory Sites and Services
This console is used to manage your sites and subnets. If you only have a single site then you wont need to use this console. If you deploy Active Directory in multiple geographic regions you may need to use this console to manage your subnets, sites, and replication.
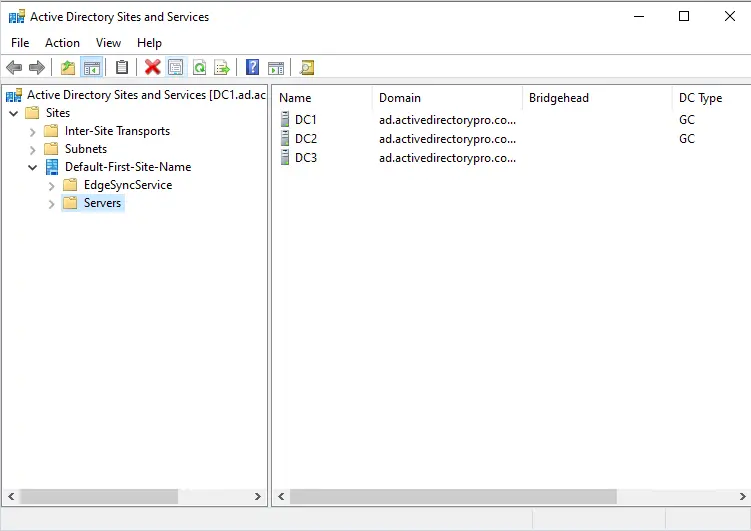
Group Policy Management Console
Group policy provides centralized management and policy settings for users and computers in an Active Directory environment. For example, to make sure all users change their password every 90 days you would use group policy and configure a password policy. Understanding how to use group policy is a critical function as a System Administrator.
DNS
The DNS console is used to manage and create DNS zones and resource records. Active Directory will not work without DNS, it is included when you install AD. It is important that you know the basics of DNS if working with Active Directory.
DHCP
The DNS console is used to create and manage the DHCP address pools in your network. This is one tool that actually has nothing to do with Active Directory. You don’t need DHCP for Active Directory but it is typically used to simplify assigning IP addresses to client devices.
PowerShell
PowerShell is a command line tool that helps you to automate many routine tasks such as creating, updating, and reporting on objects in Active Directory.
Why Hackers Should Learn Active Directory
Hackers should learn Active Directory because it presents a lucrative target for potential exploitation due to its widespread usage and often overlooked vulnerabilities. Here’s why:
Active Directory Vulnerability: LLMNR Poisoning
- LLMNR (Link-Local Multicast Name Resolution) is a protocol used for local network name resolution in the absence of a DNS server.
- It lacks authentication mechanisms, allowing anyone to respond to LLMNR requests, making it vulnerable to LLMNR poisoning attacks.
- Attackers can intercept LLMNR requests and redirect traffic to their own malicious IP addresses, leading to potential credential theft and relay attacks.
- Exploiting LLMNR poisoning can provide attackers with access to password hashes, facilitating unauthorized access to the network.
Active Directory Vulnerability: SMB Relay Attacks
- SMB (Server Message Block) protocol, commonly used for network file sharing, is vulnerable to relay attacks, particularly when paired with NTLM authentication.
- Attackers can manipulate SMB authentication attempts, relaying them to different servers to impersonate users and gain unauthorized access to network resources.
- The lack of SMB signing validation allows attackers to exploit this vulnerability without needing strong user passwords, bypassing traditional security measures.
- Successful SMB relay attacks can grant attackers elevated privileges and unrestricted access to sensitive data within the network.
By learning about Active Directory vulnerabilities like LLMNR poisoning and SMB relay attacks, hackers can exploit these weaknesses to infiltrate networks, steal sensitive information, and carry out malicious activities. Understanding these vulnerabilities allows hackers to bypass traditional security measures and exploit network weaknesses effectively.
It’s important for organizations to proactively defend against these threats by implementing security measures such as disabling LLMNR and NBT-NS, enabling SMB signing, requiring strong user passwords, and implementing network access controls. Failure to address these vulnerabilities can leave organizations susceptible to exploitation and compromise of their Active Directory infrastructure.
📢 Enjoyed this article? Connect with us On Telegram Channel and Community for more insights, updates, and discussions on Your Topic.
