In an increasingly interconnected digital landscape, the threat of phishing attacks looms larger than ever before. These deceptive and malicious tactics continue to target individuals, businesses, and organizations with devastating consequences. As technology advances, so do the techniques employed by cybercriminals, making it crucial for individuals and enterprises to understand the intricacies of phishing attacks and take proactive measures to defend against them.
This comprehensive article aims to peel back the layers of phishing attacks, delving deep into their various forms, tactics, and consequences. By exploring the nuances of this pervasive threat, readers will gain a comprehensive understanding of the inner workings of phishing attacks and the strategies needed to protect themselves and their organizations.
The article begins by defining phishing attacks, establishing a foundation of knowledge for readers unfamiliar with the concept. It then highlights the importance of phishing awareness, emphasizing the need for individuals and businesses to stay informed and vigilant in the face of evolving cyber threats.
Delving further, the article explores the different attack vectors employed by phishers, including email phishing, spear phishing, smishing, vishing, and whaling attacks. Each section provides an in-depth analysis of the attack method, its objectives, and the techniques used to deceive victims.
The article also addresses the types of phishing attacks in greater detail, shedding light on the specific tactics employed within each category. It covers email phishing, spear phishing, smishing (SMS phishing), vishing (voice phishing), and whaling attacks, unraveling the strategies used by cybercriminals to exploit their victims.
Additionally, the article emphasizes the significance of user awareness and highlights best practices for individuals and organizations to mitigate the risks associated with phishing attacks. It delves into the importance of robust cybersecurity measures, employee training, and implementing technical safeguards to safeguard against these threats.
What is a phishing attack
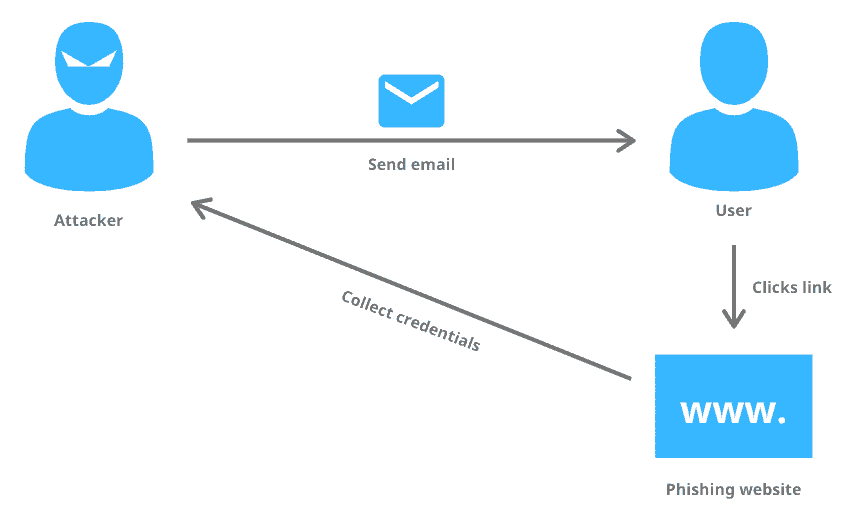
Phishing attacks are a form of cybercrime that involve fraudulent attempts to obtain sensitive information, such as login credentials, financial data, or personal details, by posing as a trustworthy entity or individual. The term “phishing” is derived from the word “fishing,” as attackers cast a wide net hoping to hook unsuspecting victims.
In a phishing attack, the attackers typically masquerade as a reputable organization, such as a bank, social media platform, or online service provider, to deceive individuals into divulging their confidential information. They employ various tactics to trick victims into believing that their requests or communications are legitimate and urgent.
Phishing attacks often rely on psychological manipulation and social engineering techniques to exploit human vulnerabilities. Attackers craft convincing messages, emails, or websites that imitate the appearance and branding of the legitimate organization, creating a false sense of trust and urgency in the recipient.
These fraudulent communications often contain links to spoofed websites or malicious attachments designed to collect sensitive information when accessed or opened. Once victims unwittingly provide their credentials or personal data, the attackers can exploit this information for financial gain, identity theft, or launching further targeted attacks.
Phishing attacks can target individuals or organizations, and they continue to evolve and become increasingly sophisticated. Attackers constantly adapt their tactics, leveraging current events, social trends, or personal information to make their messages appear more authentic and credible.
The consequences of falling victim to a phishing attack can be severe, leading to financial losses, reputational damage, and compromised personal or corporate security. Therefore, understanding how phishing attacks work and adopting proactive measures to identify and prevent them is crucial in safeguarding against this pervasive form of cybercrime.
Importance of Phishing Awareness
Imagine receiving an email that appears to be from your bank, urgently requesting you to update your account information. It seems legitimate, and the sense of urgency makes you want to act quickly. But hold on! What if this is a phishing attack?
Phishing attacks have become one of the most prevalent and damaging forms of cybercrime, targeting individuals and organizations alike. The importance of phishing awareness cannot be overstated, as it empowers individuals to recognize and resist these deceitful tactics. Here’s why phishing awareness matters, presented in an engaging and interesting way:
- Protecting Your Personal and Financial Information: Phishing attacks aim to trick you into sharing sensitive data like passwords, credit card details, or social security numbers. By being aware of phishing techniques, you become the gatekeeper of your own information, preventing it from falling into the wrong hands.
- Safeguarding Against Identity Theft: Phishers often use stolen information for identity theft, which can have devastating consequences. By understanding phishing strategies, you can better detect suspicious requests for personal data and avoid becoming a victim of this invasive crime.
- Defending Against Malware and Ransomware: Phishing emails frequently contain malicious links or attachments that can infect your devices with malware or ransomware. With phishing awareness, you’ll learn to spot these red flags and avoid unintentionally compromising your computer or network security.
- Preserving Your Online Reputation: Falling prey to a phishing attack can result in compromised social media accounts, unauthorized posts, or messages sent to your contacts. By staying vigilant and educating yourself about phishing tactics, you can prevent reputational damage and maintain control over your online presence.
- Shielding Your Organization from Data Breaches: Businesses are prime targets for phishing attacks, with attackers aiming to gain access to corporate networks, customer databases, or financial systems. By promoting phishing awareness among employees, organizations can strengthen their cybersecurity defenses and reduce the risk of costly data breaches.
- Enhancing Cybersecurity Culture: Phishing awareness goes beyond individual protection—it fosters a culture of cybersecurity. When everyone is educated and vigilant, the collective defense against phishing attacks becomes stronger, benefiting both individuals and the broader online community.
- Empowering Critical Thinking and Skepticism: Phishing awareness encourages a healthy dose of skepticism when confronted with unexpected requests or suspicious emails. It cultivates critical thinking skills, enabling you to question the authenticity of messages and make informed decisions to protect yourself and your assets.
In a world where technology pervades every aspect of our lives, phishing attacks have become an unfortunate reality. By embracing phishing awareness, you become an active participant in safeguarding your personal information, defending against cyber threats, and promoting a more secure digital landscape for everyone. So, stay informed, stay vigilant, and outsmart those phishers!
How Phishing Attacks Work
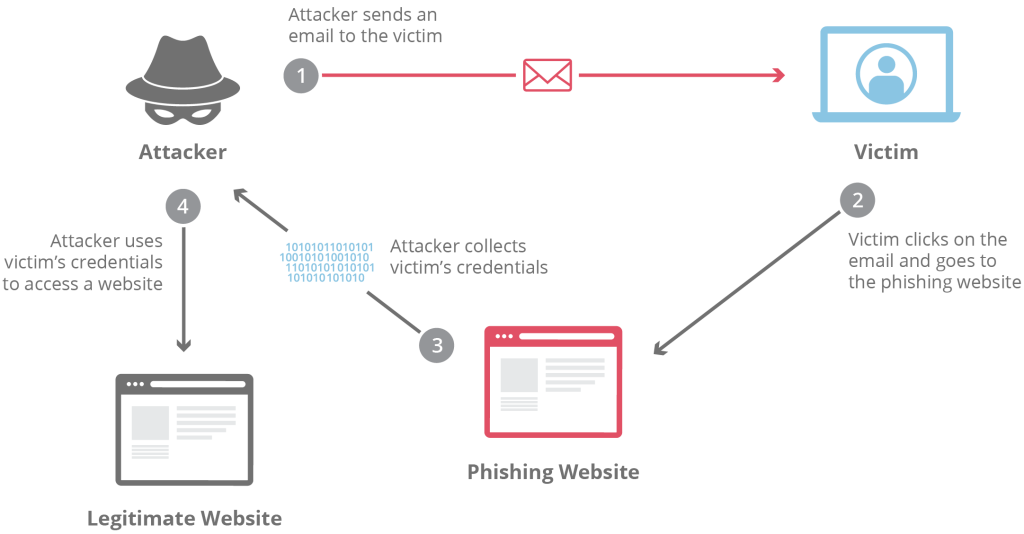
Once upon a time in the vast ocean of the internet, there was a mischievous cybercriminal named Phisher Pete. Pete was a cunning character who loved to play tricks on unsuspecting users. His favorite game was “Phishing for Secrets,” and he had mastered the art of casting his deceptive net.
One day, Pete stumbled upon a treasure trove of personal information—email addresses, names, and even a few credit card numbers. He couldn’t resist the temptation to exploit this valuable resource. Pete knew that the key to his success lay in his ability to deceive and manipulate his victims, so he hatched a plan.
Pete decided to start with a classic phishing technique: email phishing. He crafted an email that appeared to be from a popular online shopping site. The subject line read, “Exclusive 50% Off Sale for Our Loyal Customers!” Who could resist such an enticing offer?
With a mischievous grin, Pete sent his email to thousands of unsuspecting users, hoping to lure them into his trap. The email claimed that due to a system update, users needed to update their account information urgently to continue enjoying the discounts. Of course, the email contained a link that led to a perfectly designed fake website.
As users received Pete’s email, curiosity got the better of them. They clicked on the link and were directed to the imposter website, which looked remarkably similar to the legitimate online shopping site. Pete had gone to great lengths to replicate the branding, layout, and even the security logos on the site. It was a trap waiting to be sprung.
Once on the fake website, users were prompted to enter their usernames and passwords, just as they would on the real site. Little did they know that Pete was capturing every keystroke they made. He could practically hear their gasps of shock and horror as their sensitive information fell right into his virtual hands.
Pete’s plan didn’t end there. He knew that some users might be skeptical, so he added a sense of urgency to his game. He sent follow-up emails to those who hadn’t fallen for his initial trick, pretending to be the site’s customer support team. The emails warned of suspicious activity on their accounts and instructed them to call a provided phone number immediately.
Unbeknownst to the victims, the phone number led to Pete’s partner in crime, who posed as a helpful customer service representative. This partner, using a technique called vishing (voice phishing), skillfully extracted additional personal details under the guise of resolving the alleged security issues.
As Pete reveled in his ill-gotten gains, the victims found themselves entangled in a web of deceit. Their personal and financial information was compromised, and they became vulnerable to identity theft, unauthorized purchases, and a whole array of cyber threats.
But little did Pete know that a team of cybersecurity experts was hot on his trail. They were dedicated to combating cybercrime and protecting innocent users from falling prey to phishing attacks. Armed with knowledge and advanced technologies, they worked tirelessly to raise awareness and develop countermeasures to thwart Pete and his fellow phishers.
And so, the battle between Phisher Pete and the cybersecurity defenders raged on, with users caught in the middle. The outcome of this ongoing saga depended on the choices individuals made—to remain vigilant, educate themselves about phishing techniques, and never take the bait.
Remember, dear reader, in this digital world filled with crafty phishers, you hold the power to outsmart them. Stay alert, question suspicious emails and websites, and protect your personal information like the valuable treasure it is.
Common Phishing Techniques
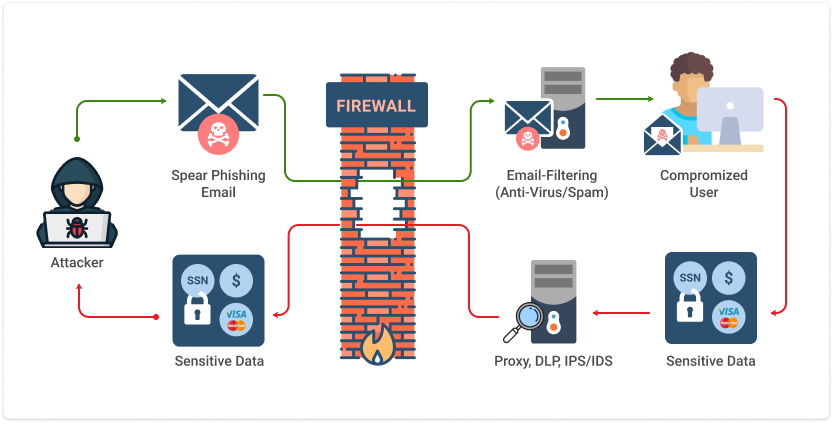
Phishing attacks employ a range of techniques to deceive individuals and trick them into divulging sensitive information. Here, we explore some of the most common phishing techniques in depth:
Deceptive Email Spoofing
Attackers often spoof email addresses to make their messages appear as if they originate from a trusted source. By altering the “From” field, they mimic the identity of a reputable organization, such as a bank or a well-known company. This technique aims to deceive recipients into believing the email is legitimate, increasing the chances of them falling for the scam.
Clone Phishing
Clone phishing involves creating a replica of a legitimate email that the recipient has previously received. Attackers duplicate an existing email, including its content and attachments, but make subtle modifications to deceive the recipient. These modifications might involve replacing legitimate links or attachments with malicious ones, leading the victim to a fake website or triggering the installation of malware.
Link Manipulation
Phishers frequently use link manipulation to trick victims into visiting fraudulent websites. They disguise malicious URLs by using URL shorteners or embedding them within hyperlinked text. The displayed link may appear legitimate, but the underlying URL points to a malicious site designed to capture sensitive information or deliver malware. Hovering over the link without clicking can reveal the true destination, providing a clue to its authenticity.
Credential Harvesting
Credential harvesting aims to extract login credentials from unsuspecting victims. Phishers often create fake login pages that closely resemble legitimate websites, such as banking portals, email providers, or social media platforms. When users enter their login credentials on these fake pages, the information is captured by the attackers. These stolen credentials can then be used to gain unauthorized access to the victim’s accounts.
Malware Distribution
Phishing attacks frequently involve the distribution of malware. Attackers may send malicious attachments disguised as harmless files, such as invoices, resumes, or shipping notifications. Once opened, these attachments can infect the victim’s device with malware, allowing the attacker to monitor their activities, steal sensitive data, or gain unauthorized access to their system.
Social Engineering
Social engineering techniques play a crucial role in phishing attacks. Attackers exploit human psychology to manipulate victims into taking action or revealing sensitive information. They may create a sense of urgency, fear, or curiosity to increase the chances of success. By impersonating authority figures, adopting urgent tones, or presenting alarming scenarios, attackers try to override the victim’s logical thinking and compel them to act hastily.
It’s important to stay vigilant and skeptical when encountering suspicious emails, messages, or websites. By understanding these common phishing techniques, individuals can become more adept at recognizing and avoiding phishing attempts. Implementing security best practices, such as verifying email senders, scrutinizing URLs, and being cautious when sharing personal information, can significantly reduce the risk of falling victim to phishing attacks.
Phishing Attack Vectors
Phishing attacks employ various tactics and channels to trick individuals into revealing sensitive information or performing malicious actions. Let’s dive in-depth into some of the most common phishing attack vectors:
Email-based Phishing Attacks
Email phishing is perhaps the most well-known and widely used method. Attackers send deceptive emails pretending to be from legitimate sources, such as banks, social media platforms, or government agencies. These emails often employ social engineering techniques to evoke a sense of urgency or fear, urging recipients to take immediate action. They may include links to spoofed websites or malicious attachments that, when clicked or opened, lead to the capture of sensitive data or the installation of malware.
Malware-based Phishing Attacks
Malware-based phishing attacks involve the distribution of malicious software (malware) through various channels. Attackers often use email attachments, infected files shared via peer-to-peer networks, or compromised websites to deliver malware. Once the malware infects a user’s system, it can capture sensitive information, monitor online activities, or even grant unauthorized remote access to the attacker. Common types of malware used in phishing attacks include keyloggers, ransomware, and remote access trojans (RATs).
Fake Websites and Domain Spoofing
In this phishing vector, attackers create counterfeit websites that closely resemble legitimate ones. They often register domain names that mimic the original site’s URL or use subdomains to deceive users. These fake websites are designed to trick users into providing their login credentials or personal information. Victims may be directed to these websites via email links, search engine results, or malicious advertisements. It’s important to carefully scrutinize URLs, look for HTTPS encryption, and verify the website’s legitimacy before entering any sensitive information.
Social Engineering Techniques
Phishing attacks heavily rely on social engineering, exploiting psychological and emotional factors to manipulate victims. Some common social engineering techniques include:
a) Pretexting: Attackers create a fictional scenario or pretext to gain the victim’s trust. For example, they might pose as a company representative conducting a survey or verifying account information.
b) Baiting: Attackers offer an enticing incentive, such as a free gift or exclusive content, to entice users into clicking on malicious links or downloading infected files.
c) Spear Phishing: This targeted approach involves customizing phishing messages to specific individuals or groups, using personalized information gathered from various sources, such as social media profiles or public databases. By leveraging personal details, attackers increase the likelihood of successful deception.
d) Whaling Attacks: Whaling attacks specifically target high-ranking individuals, such as executives or CEOs. Attackers carefully research their targets and craft sophisticated emails that appear to be from trusted sources, aiming to gain access to valuable corporate data or financial accounts.
Understanding these phishing attack vectors helps individuals and organizations enhance their defenses against such threats. By staying informed, adopting proactive security measures, and cultivating a healthy skepticism, users can better protect themselves against the ever-evolving techniques employed by phishing attackers.
Types of Phishing Attacks
Phishing attacks come in various forms, each tailored to exploit different vulnerabilities and achieve specific objectives. Let’s delve into the depths of the most prevalent types of phishing attacks:
Email Phishing:
Email phishing, also known as “generic phishing,” is the most prevalent and widely recognized type of phishing attack. In an email phishing attack, cybercriminals send out large volumes of deceptive emails to a wide audience, hoping that some recipients will fall for their tricks.
The success of email phishing attacks relies on social engineering techniques and the ability to create a sense of urgency, curiosity, or fear in the recipient. Here’s an in-depth look at the different aspects of email phishing:
- Email Spoofing: Attackers often manipulate the “From” field in the email header to make it appear as if the message is coming from a trusted source. They forge email addresses to imitate well-known organizations, making it difficult for recipients to discern the email’s true origin.
- Deceptive Content: Phishing emails are designed to appear legitimate and urgent. They may use official logos, professional language, and mimic the email formatting of reputable organizations. The content may include urgent requests for personal information updates, claims of account security breaches, or notifications of prize winnings—all intended to entice recipients to take immediate action.
- Malicious Links: Phishing emails frequently contain hyperlinks that lead to fraudulent websites or infected web pages. These links are disguised using techniques like URL obfuscation or URL shortening services to make them appear genuine. Clicking on such links can redirect victims to fake login pages or websites that download malware onto their devices.
- Attachments: Phishing emails often include attachments, such as infected documents or compressed files. These attachments may contain malware that, once downloaded and opened, can compromise the victim’s system and enable the attacker to gain unauthorized access or collect sensitive information.
- Urgency and Emotional Manipulation: Attackers create a sense of urgency or fear in the recipient to provoke quick action. They may claim that an account will be suspended, a payment is overdue, or a security breach has occurred. By evoking emotions and a desire to resolve the situation, attackers hope to override the recipient’s critical thinking and prompt them to disclose sensitive information or click on malicious links.
- Pretexting and Personalization: Phishers often use pretexting techniques to increase the authenticity of their emails. They may include personal information obtained from data breaches or publicly available sources to gain the recipient’s trust. By customizing emails with the recipient’s name or referencing their recent activities, attackers create an illusion of familiarity, making it more likely for victims to fall for the scam.
Email phishing attacks continue to evolve, with attackers employing sophisticated techniques to deceive recipients and bypass security measures. To protect against email phishing, individuals and organizations should exercise caution when interacting with emails, scrutinize email senders, avoid clicking on suspicious links or attachments, and regularly update their security software. Additionally, education and awareness programs play a vital role in empowering users to identify and report phishing attempts, ultimately strengthening the collective defense against this pervasive threat.
Spear Phishing:
Spear phishing is a highly targeted form of phishing attack that focuses on specific individuals or groups. Unlike generic phishing, which casts a wide net, spear phishing attackers invest time and effort into researching their targets to craft personalized and convincing messages. Here’s an in-depth look at spear phishing:
- Targeted Selection: Spear phishing attackers carefully select their targets based on specific criteria. They may target employees within a particular organization, individuals with access to valuable data or financial resources, or high-profile individuals such as executives or government officials. The goal is to increase the likelihood of success by exploiting the target’s role, authority, or access to sensitive information.
- Reconnaissance: Attackers conduct thorough reconnaissance to gather information about their targets. They scour social media profiles, professional networking sites, company websites, and public databases to collect personal details, job titles, relationships, or recent activities. This information provides the foundation for customizing the phishing attack.
- Personalized Messages: Using the information gathered during reconnaissance, spear phishers craft highly personalized emails that appear to come from a trusted source. They often impersonate colleagues, supervisors, or business partners, using familiar language and referencing specific events or projects to make the email appear legitimate.
- Social Engineering Techniques: Spear phishing attacks leverage social engineering techniques to manipulate the target’s emotions and trust. Attackers may exploit the target’s sense of duty, curiosity, or fear, creating scenarios that require immediate action or offering enticing opportunities. By tailoring the message to the target’s interests, responsibilities, or relationships, attackers increase the chances of success.
- Spoofed Domains: To make their emails seem authentic, spear phishers may use email addresses or domains that closely resemble those of trusted individuals or organizations. They may manipulate the display name, reply-to address, or use similar-looking domain names to deceive recipients into believing the email is legitimate.
- Credential Theft or Malware Deployment: The ultimate objective of spear phishing attacks can vary. Attackers may aim to steal login credentials by directing targets to fake login pages or use malicious attachments to install malware on the target’s device. Once compromised, attackers can gain unauthorized access to sensitive systems, exfiltrate data, or conduct further malicious activities.
Smishing (SMS Phishing):
Smishing, a portmanteau of “SMS” and “phishing,” refers to phishing attacks conducted through text messages or SMS (Short Message Service). In smishing attacks, cybercriminals exploit the widespread use of mobile devices to deceive individuals and trick them into divulging sensitive information or performing malicious actions. Here’s an in-depth look at smishing:
- Text Message Deception: Smishing attacks typically involve the sending of deceptive text messages to mobile phone users. These messages may appear to be from reputable organizations, such as banks, e-commerce platforms, or government agencies. The messages often contain urgent requests, enticing offers, or alarming alerts to grab the recipient’s attention and provoke immediate action.
- Social Engineering Techniques: Smishers rely on social engineering tactics to manipulate recipients’ emotions and induce a sense of urgency, curiosity, or fear. They may claim that the recipient’s account has been compromised, a payment is overdue, or a prize has been won. By exploiting psychological triggers, smishers aim to override the recipient’s critical thinking and prompt them to respond or click on malicious links.
- Fake URLs and Shortened Links: Smishing messages may contain links that appear genuine but actually redirect recipients to fraudulent websites or landing pages. Attackers often use URL shortening services or employ other techniques to mask the actual destination of the link. Clicking on these links can lead to the capture of personal information, installation of malware, or other malicious activities.
- Request for Personal Information: Smishing attacks may request recipients to provide sensitive information, such as account credentials, social security numbers, or credit card details, either by replying to the text message or by following a link to a fake login page. Attackers use this information for identity theft, financial fraud, or further targeted attacks.
- Call-to-Action and Urgency: Smishing messages often include a call-to-action that urges recipients to act quickly. This could be requesting an immediate response, clicking on a link to resolve an issue, or contacting a specified phone number. By creating a sense of urgency and importance, attackers aim to prevent recipients from questioning the legitimacy of the message.
- Caller ID Spoofing: In some smishing attacks, the attacker may spoof the caller ID to make the text message appear to come from a trusted source. This manipulation increases the chances of the recipient falling for the scam and believing the message to be genuine.
Vishing (Voice Phishing):
Vishing, short for “voice phishing,” is a type of phishing attack that occurs over the phone. In vishing attacks, cybercriminals use social engineering techniques to manipulate and deceive individuals into divulging sensitive information or performing actions that benefit the attacker. Here’s an in-depth look at vishing:
- Phone Call Impersonation: Vishing attacks involve attackers making phone calls, pretending to be someone they are not. They may pose as representatives from banks, government agencies, IT support teams, or trusted service providers. By using spoofing techniques or manipulating caller ID displays, vishers make it appear as though the call is originating from a legitimate source.
- Social Engineering Tactics: Vishing relies heavily on social engineering to exploit human vulnerabilities and manipulate the target’s trust and emotions. Attackers may use various tactics, such as building rapport, creating a sense of urgency, or instilling fear to manipulate the target into revealing sensitive information or performing specific actions.
- Urgent Requests and Threats: Vishers often create a sense of urgency or exploit fears to pressure the target into compliance. They may claim there is a problem with the target’s account, that personal information has been compromised, or that legal consequences will arise if immediate action is not taken. By leveraging these urgent requests and threats, vishers aim to override the target’s critical thinking and elicit the desired response.
- Request for Personal Information: During vishing calls, attackers may directly ask for personal information such as social security numbers, credit card details, or account credentials. They may pose as representatives conducting security verifications, account updates, or offering assistance with a supposed issue. By gaining access to this information, attackers can commit identity theft, financial fraud, or engage in other malicious activities.
- Manipulation of Trust and Authority: Vishers often exploit the target’s trust in authority figures or well-known organizations. By impersonating employees of reputable institutions or using official-sounding titles, they attempt to create an illusion of legitimacy. This manipulation of trust and authority increases the likelihood of the target complying with the attacker’s requests.
- Call Recording and Voice Manipulation: In some vishing attacks, attackers may record the call without the target’s knowledge. This allows them to capture sensitive information or obtain voice samples for potential future use. Attackers can manipulate these recordings to deceive other individuals or bypass voice recognition systems.
Whaling Attacks:
Whaling attacks, also known as “CEO fraud” or “business email compromise (BEC),” are a type of targeted phishing attack that focuses on high-profile individuals within an organization, such as executives, business leaders, or individuals with significant authority or access to sensitive information. Whaling attacks aim to deceive these individuals into taking specific actions that benefit the attacker. Here’s an in-depth look at whaling attacks:
- Targeting High-Profile Individuals: Whaling attacks specifically target individuals who hold key positions within an organization. This includes CEOs, CFOs, senior executives, or other high-ranking employees who have access to valuable resources, financial accounts, or decision-making authority. By focusing on these individuals, attackers hope to gain access to sensitive information or manipulate them into performing actions that can have significant consequences.
- Research and Social Engineering: Whaling attacks involve thorough research on the targeted individual and their organization. Attackers gather information from various sources, including public profiles, social media, company websites, and news articles. This information is then used to craft highly personalized and convincing messages that appear to come from a trusted source or a known business partner.
- Impersonation and Spoofing: Attackers impersonate a high-ranking executive or a trusted contact to establish credibility and gain the target’s trust. They may manipulate email addresses, display names, or use domain spoofing techniques to make the email appear as if it is originating from a legitimate source. By mimicking the writing style and tone of the impersonated individual, attackers create an illusion of authenticity.
- Urgent Requests and Critical Situations: Whaling attacks often leverage urgency and critical situations to pressure the targeted individual into immediate action. Attackers may claim urgent business matters, time-sensitive financial transactions, or the need for confidential information. By exploiting the target’s sense of responsibility or fear of negative consequences, attackers aim to override their normal security protocols and critical thinking.
- Wire Transfer and Financial Fraud: Whaling attacks frequently involve requests for wire transfers or financial transactions. Attackers may request the transfer of funds to an account under their control, posing as a business partner, supplier, or requesting payment for a fictional invoice. In some cases, attackers may compromise legitimate email accounts to intercept ongoing financial transactions and modify the recipient’s banking information.
- Confidential Information and Data Theft: Whaling attacks may also target sensitive information, such as customer data, intellectual property, or trade secrets. Attackers may pose as internal employees or authorized personnel requesting access to confidential databases or sensitive files. By exploiting the target’s authority or their desire to comply with internal protocols, attackers seek to gain unauthorized access to valuable information.
How to prevent phishing
Phishing attack protection requires steps be taken by both users and enterprises.
For users, vigilance is key. A spoofed message often contains subtle mistakes that expose its true identity. These can include spelling mistakes or changes to domain names, as seen in the earlier URL example. Users should also stop and think about why they’re even receiving such an email.
For enterprises, a number of steps can be taken to mitigate both phishing and spear phishing attacks:
- Two-factor authentication (2FA) is the most effective method for countering phishing attacks, as it adds an extra verification layer when logging in to sensitive applications. 2FA relies on users having two things: something they know, such as a password and username, and something they have, such as their smartphones. Even when employees are compromised, 2FA prevents the use of their compromised credentials, since these alone are insufficient to gain entry.
- In addition to using 2FA, organizations should enforce strict password management policies. For example, employees should be required to frequently change their passwords and to not be allowed to reuse a password for multiple applications.
- Educational campaigns can also help diminish the threat of phishing attacks by enforcing secure practices, such as not clicking on external email links.








