So, you’ve decided to delve into the world of reverse engineering? That’s super exciting, and we couldn’t be more thrilled to guide you on this thrilling journey. Whether you’re simply curious or looking to dive deep into the inner workings of software, hardware, or even firmware, you’re in the right place!
But first things first, what’s reverse engineering, right? At its simplest, reverse engineering is a process where we break down a system, device, or even software into its most basic parts to understand its structure, functions, and operations. Think of it like solving a puzzle but in reverse – instead of putting the pieces together, you’re actually pulling them apart to see the bigger picture.
Why is reverse engineering important, you ask? Well, it has tons of applications. It helps us understand and secure systems better, aids in product improvement, assists in discovering potential vulnerabilities, and even enables us to figure out how our favorite games or apps work. From cybersecurity to product design, the applications are practically limitless!
In this guide, we’re about to embark on an epic adventure – from understanding the basics of reverse engineering to mastering the advanced techniques, and even applying these in real-world scenarios. But don’t worry, we’ll walk you through each step of this roadmap, ensuring you understand the concepts, practices, and even the ethical implications involved in reverse engineering.
So, are you ready to become a reverse engineering pro? Great, let’s get started!
Understanding the Basics of Reverse Engineering

History and Evolution of Reverse Engineering
Alright, now that you’ve got a basic idea of what reverse engineering is, let’s travel back in time to explore its origins and evolution. Don’t worry, I promise I won’t bore you with an overly academic history lesson.
Believe it or not, the concept of reverse engineering has been around for quite a while, even way before computers! In fact, back in the days, craftsmen used to reverse engineer inventions to replicate them or to build something better. In essence, they were like the original hackers, dissecting tools, toys, and machinery to understand how things ticked!
Then along came World War II, a turning point in the history of reverse engineering. During this time, armies would capture enemy machinery like tanks, radios, and planes, and then reverse engineer them to gain an edge in battle. Can you imagine the thrill and challenge they faced while doing this?
Fast forward to the computer age, reverse engineering found its footing in software development. In the early days, it was primarily used to ensure compatibility. The developers would reverse engineer competitor software to create programs that could work with them.
Now, in our current digital era, reverse engineering is an integral part of everything, from debugging and testing software to enhancing cybersecurity. Malware analysts, for instance, rely on reverse engineering to understand how malware operates so they can develop effective countermeasures. Cool, isn’t it?
One thing you need to keep in mind, though, is that as much as reverse engineering has evolved, it has always remained a skill that thrives on curiosity, patience, and a knack for problem-solving. Remember, every gadget or software you reverse engineer is a puzzle waiting to be solved.
Fundamental Concepts
Okay, so now that we’re all clued up on where reverse engineering comes from, let’s get into some of the nitty-gritty that underpins this fascinating field. Trust me, it’s not as scary as it might sound. Ready? Alright, let’s dive in!
- Disassembly/Decompiling: This is like your starting point, the first step into the rabbit hole. Disassembling is all about breaking down a program into assembly language code, the lowest level human-readable code. Decompiling, on the other hand, converts machine code or byte code back into a high-level language. Imagine it’s like reading the secret recipe of your favorite snack, only in code language!
- Static and Dynamic Analysis: Here’s where detective work comes in. Static analysis is all about inspecting the system without running it, like scrutinizing a car without turning on the engine. Dynamic analysis, in contrast, is about testing and observing the system while it’s running. It’s like watching the car in action to see how it performs on the road.
- Debugging: This is like your handy tool for spotting and fixing those pesky bugs that make a program act funny. You’ll use a debugger to run the program under controlled conditions and track what’s going wrong.
- Code Reversing: Now, this is the heart of reverse engineering. It’s all about understanding the code and recreating it, even when you don’t have access to the source code. It’s a bit like learning a new language from scratch – it’s challenging but super rewarding.
- Network Traffic Analysis: This is where you’ll monitor and analyse network traffic. It’s crucial in understanding how a program communicates with others over a network. Think of it like being a traffic cop, managing and understanding every bit of data coming and going.
Remember, the whole point of reverse engineering is understanding how a system works, finding potential weaknesses, and then either improving the system or developing countermeasures to those weaknesses.
And that’s the lowdown on the fundamental concepts of reverse engineering! Keep these in mind as we delve deeper into the topic, and you’ll be decoding systems like a pro in no time!
Purpose and Application Areas
Now that we’ve got the basics down, you might be wondering, “Why should I even bother learning reverse engineering? Where am I going to use it?” Well, you’d be surprised at just how versatile this skill is! Let’s dive into why it’s worth your time and some of the cool areas where you can put your skills to use.
Understanding and Improving Products: Ever looked at an awesome gadget and wondered, “How’d they do that?” Well, with reverse engineering, you can find out! You can dissect a product to figure out what makes it tick and use that knowledge to design an even better one. It’s like discovering a magician’s trick and then putting your own spin on it!
Cybersecurity and Malware Analysis: This is the big one. Cybersecurity pros use reverse engineering to dissect malicious software, figure out how it infects systems, and develop defenses to stop it. So, you could be on the front lines of the digital world, defending against cyber-attacks. Sounds like a superhero job, doesn’t it?
Compatibility and Interoperability: Ever wished you could make different tech work better together? With reverse engineering, you can! By understanding how different software or hardware operates, you can create bridges between them, improving their compatibility and making life easier for users.
Intellectual Property Verification: This is an interesting one. Companies sometimes use reverse engineering to check if others are infringing on their patents or copyrights. Kind of like a detective job!
Legacy Systems: This is especially handy in companies where they use old (we call them “legacy”) systems. Since these systems are often poorly documented, reverse engineering can help understand how they work, so they can be updated or replaced.
Learning and Education: If you’re like me and love to learn how things work just for the sake of it, then reverse engineering is your golden ticket. It gives you the tools to satisfy your curiosity and deepen your understanding of technology.
And that’s just the tip of the iceberg. With a skill like reverse engineering in your toolkit, the possibilities are virtually endless. Excited yet? I know I am!
Getting Started with Reverse Engineering
Required Skillset
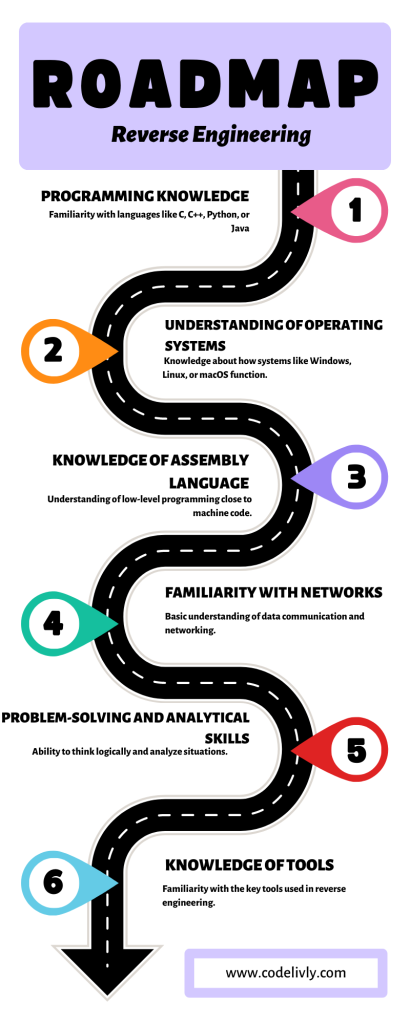
Okay, before we dive any deeper, let’s talk about the skills you’ll need on this reverse engineering adventure. It’s like packing your backpack before a big hike. Having the right skills in your kit can make your journey a lot smoother. Ready? Here we go:
Programming knowledge: You guessed it! Being familiar with programming languages like C, C++, Python, or Java is going to be a big help. It’s like understanding the language of the territory you’re exploring. Don’t sweat it if you’re not a pro yet, though. You’ll learn a lot on the way!
Understanding of Operating Systems: Get cozy with how operating systems like Windows, Linux, or macOS work. It’ll help you understand how software interacts with the system, which is super useful when you’re trying to figure out what a piece of software does.
Knowledge of Assembly Language: I won’t sugarcoat it; this one can be a bit of a brain teaser. Assembly language is the lowest level of coding, right above machine language. But don’t let that scare you off! It’s a superpower in the world of reverse engineering.
Familiarity with Networks: The digital world is all about communication, and that’s where networks come in. Having a basic understanding of how data moves around can help you figure out what a piece of software is talking to and why.
Patience and Perseverance: Alright, this isn’t exactly a technical skill, but it’s just as important. Reverse engineering can be a complex process, kind of like solving a jigsaw puzzle without the picture on the box. So, patience, determination, and a healthy dose of curiosity will be your best friends.
Problem-Solving and Analytical Skills: Just like Sherlock Holmes, you’ll be solving mysteries – only in code! Being able to think logically and analyze situations will make you a great reverse engineer.
Knowledge of Tools: Just like a carpenter has a toolbox, you’ll also have a set of tools for reverse engineering. Don’t worry, we’ll cover these later in our guide.
And there you have it, the basic skillset you’ll need to start your journey into reverse engineering. Sure, it seems like a lot, but remember, every expert was once a beginner. You’ve got this!
Essential Tools and Resources
So, we’ve got our skillset sorted. But skills alone won’t get us where we need to go. Just like a painter needs a brush or a chef needs a good knife, we’re going to need some tools to get the job done right. So, let’s gear up and check out the must-have tools and resources for our reverse engineering expedition:
Disassemblers and Decompilers: Remember when we talked about disassembly and decompiling? This is where these tools come in. Tools like IDA Pro, Ghidra, or Radare2 are your go-to’s here. They break down binary code into something we humans can read and understand.
Debuggers: Time to put on our detective hats! Debuggers like OllyDbg, WinDbg, or GDB help us to execute programs step-by-step, inspect the system’s state at any point, and track down those sneaky bugs.
Hex Editors: Tools like HxD or Hex Fiend let you view and edit the raw bytes of any file – handy when you want to look at something in its most basic form.
Network Analyzers: Tools like Wireshark or TCPDump are your allies for peeking into network communications. They’ll help you understand how a program is chatting with the rest of the digital world.
Virtual Environments: Think of these as your personal digital sandbox. Tools like VirtualBox or VMware let you run systems in a controlled, isolated environment – perfect for experimenting without worrying about messing up your actual system.
Online Resources: Trust me, you’re not alone in this journey! Online platforms like StackOverflow, GitHub, or Reverse Engineering Reddit (r/ReverseEngineering) are bustling with fellow explorers ready to share their knowledge and experiences.
And there you have it! With these tools in your belt, you’re all set to take on the exciting challenges of reverse engineering. Remember, mastering these tools will take time and practice, but hey, every great adventure has its learning curve, right?
Setting up the Environment
Okay, so now that we’ve got our toolkit ready, it’s time to roll up our sleeves and set up our workspace. Think of it like setting up your very own lab, except it’s all digital. Cool, huh? Let’s jump in:
Choosing Your Operating System: The first thing we need to decide is which operating system to use. Windows is great for reversing Windows malware and software, while Linux is a gem for its powerful command line and wide array of tools. You could also use a Mac, but for beginners, I’d recommend starting with either Windows or Linux.
Setting Up a Virtual Machine: Remember when we talked about virtual environments? Here’s where they come in. Install a Virtual Machine (VM) like VirtualBox or VMware on your system. This way, you can run another operating system inside your main one, safely isolated from your main system. It’s like having a digital playground to mess around in without the fear of breaking anything important.
Installing Tools: Now, let’s get those tools we talked about earlier installed. For decompiling and disassembling, grab Ghidra or IDA Pro. Snag OllyDbg or WinDbg for debugging, and don’t forget HxD or Hex Fiend for editing hex. For sniffing network traffic, Wireshark is your best friend.
Setting Up Protections: When dealing with potentially harmful software (like malware), you want to make sure you’re protected. So, it’s a good idea to install an antivirus on your main system. Just remember to disable it in your VM (you don’t want it deleting the malware you’re trying to analyze!).
Keeping It Organized: Make sure to keep your workspace neat and tidy. Organize your files and document your findings. It’ll make your life easier, I promise!
And voila! You’ve got your very own reverse engineering lab set up and ready to go. Now, the real fun begins. Are you excited? Because I sure am!
Basic Reverse Engineering Techniques
Alright, now that our lab is ready, it’s time to roll up our sleeves and get our hands dirty. So, let’s take a look at some basic reverse engineering techniques. Don’t worry if they seem a bit intimidating at first; remember, every expert was once a beginner.
Static Analysis: This is like looking under the hood of a car without starting it. You’ll use a disassembler or decompiler here to translate binary code into human-readable code. Then you’ll examine the code, checking out how it’s structured and what the different parts do. It’s all about understanding the program without actually running it.
Dynamic Analysis: Now we’re turning the car on and taking it for a spin. You’ll run the program in a controlled environment (like that virtual machine we set up) and observe what it does. This is where debuggers come in handy. They allow you to execute the program step-by-step and see what happens at each step.
Functionality Reduction: Think of this as decluttering the program. Sometimes, a program will have a lot of parts that don’t really concern us. With functionality reduction, we remove or bypass those parts so we can focus on what’s important.
Data Analysis: Here, we’re looking at the data used by the program. What information is it using? Where is it stored? How is it being manipulated? This is all about understanding how the program handles data.
Network Traffic Analysis: This is like eavesdropping on the program’s conversations. You’ll use a network analyzer to observe the data that the program sends and receives over the network. This can give you clues about what the program is doing and who it’s talking to.
And there you have it! With these basic techniques, you’re all set to start exploring the wonderful world of reverse engineering. Remember, it’s all about understanding how a program works.
Intermediate Reverse Engineering Techniques
So, you’ve got the basic techniques down, and you’re itching to take your reverse engineering skills to the next level? Great! Let’s get into some intermediate techniques that’ll add some powerful tools to your arsenal. Remember, the road might get a bit tougher from here on out, but hang in there. You’ve got this!
Binary Obfuscation Analysis: Sometimes, software developers try to make their code hard to read on purpose. This is called obfuscation. Dealing with obfuscated code can be like trying to read a book with the letters all jumbled up. But don’t worry, there are techniques and tools out there that can help you unravel the mess and make sense of it.
Code Injection: This is where we get a little sneaky. Code injection involves adding our own code into a running program. Why would we do that? Well, it lets us modify the program’s behavior and observe how it reacts. Pretty cool, right?
Hooking: This technique involves intercepting the calls a program makes to libraries and rerouting them. This lets us see what the program is asking the system to do and even change those requests. It’s kind of like listening in on a phone call and being able to change what the person on the other end hears.
Fuzzing: This technique involves throwing a bunch of random or unexpected data at a program to see how it handles it. It’s like testing a car’s safety by crashing it into a wall (only much less expensive!). It’s a great way to find vulnerabilities or bugs in a program.
Kernel Debugging: This is like the boss level of debugging. The kernel is the heart of an operating system, and kernel debugging allows us to inspect and control it as it runs. This gives us a deep understanding of what’s happening at the core of the system.
And there you have it! With these intermediate techniques in your toolkit, you’re well on your way to becoming a reverse engineering pro. Remember, practice makes perfect, so don’t be afraid to try these techniques out and learn as you go.
Advanced Reverse Engineering Techniques
Ready to level up? Great! You’ve mastered the basic and intermediate techniques and now you’re ready to dive into the deep end. Don’t worry, it’s gonna be a wild ride, but I believe in you! So, buckle up and let’s get into some advanced reverse engineering techniques:
Anti-Debugging/Anti-Disassembly Techniques: Sometimes, software will use techniques to try and stop you from debugging or disassembling it. It’s kind of like a lock trying to pick the locksmith. But fear not, for every lock, there’s a key. By understanding these techniques, you can find ways around them and continue your analysis.
Packers and Unpacking: Packers are tools that compress or encrypt a program’s code to make it harder to analyze. Unpacking is the process of reversing this to get the original code. It’s like opening a series of Russian dolls until you find the smallest one.
Malware Analysis: This is like being a digital detective, tracking down cyber-criminals. You’ll analyze malicious software to understand how it works, how to stop it, and maybe even who created it. It’s challenging work, but also incredibly important.
Reverse Engineering Hardware: Yep, reverse engineering isn’t just for software. Sometimes, you’ll want to understand how a piece of hardware works, whether it’s a computer chip, a game console, or even a car. This involves techniques like firmware analysis and micro-soldering.
Cryptanalysis: This is all about cracking codes. You’ll be dealing with cryptographic algorithms used to secure data. It’s like trying to crack a safe, but the safe is a computer program, and instead of cash, it’s full of ones and zeroes.
Phew! That’s some heavy stuff, right? But don’t get discouraged. Remember, every step you take in this journey makes you a better reverse engineer.
Building a Career in Reverse Engineering
Dreaming about turning your love for reverse engineering into a career? That’s a great idea! And guess what, I’m here to guide you through it. Let’s talk about how you can take your passion and turn it into a full-fledged profession:
Identify Your Niche: The field of reverse engineering is wide, and there’s a lot of room to specialize. Are you into cybersecurity? Or maybe you’re more excited by the idea of reverse engineering video games to figure out how they work. Pick a niche that resonifies with you, and start building your expertise there.
Keep Learning and Practicing: Remember those techniques we talked about? Keep practicing them. Dive deeper, learn more. The field is always evolving, and the best professionals are the ones who keep up with the changes.
Get Certified: There are certifications like the Certified Reverse Engineering Analyst (CREA) or the Certified Ethical Hacker (CEH) that can demonstrate your skills and knowledge to potential employers. They’re not necessary for everyone, but they can give you an edge in some cases.
Network: Connect with other professionals in the field. Attend conferences, join online communities, participate in competitions like Capture The Flag (CTF). Not only will you learn a lot, but you’ll also make connections that can help your career.
Start Building a Portfolio: Nothing says “I know what I’m doing” like a portfolio of successful projects. It could be malware you’ve analyzed, exploits you’ve discovered, or applications you’ve reverse engineered. Just remember to only include work you’re legally allowed to share!
Look for Job Opportunities: There are a lot of industries that need skilled reverse engineers. Cybersecurity, software development, electronics, even automotive industries have opportunities. Positions could be titled as Reverse Engineer, Malware Analyst, Vulnerability Researcher, and more.
Freelancing and Consultancy: If a traditional job isn’t your style, consider freelancing or consultancy. Companies often need experts for specific projects and are willing to pay for high-quality work.
Remember, building a career takes time and persistence. There will be challenges, but with passion and determination, you can overcome them. So keep going, and never stop learning.
Guidelines and Best Practices for Reverse Engineering
Alright, you’re well on your way to becoming a reverse engineering pro, but even the best of us need some guidance now and then. Let’s look at some guidelines and best practices that will keep you on the right path:
Stay Legal: Let’s get this one out of the way first. Reverse engineering can be a legal gray area. Different countries have different laws, and you need to understand them. Always get permission if you’re unsure, and remember, just because you can do something doesn’t mean you should.
Be Ethical: Reverse engineering is a tool, and like any tool, it can be used for good or bad. Always use your skills to help, not harm. It’s not just about staying out of trouble; it’s about being a responsible member of the community.
Document Your Work: Keep a record of what you’re doing and what you’ve found. It helps you keep track of your progress, and it’s crucial if you’re working as part of a team. Plus, it’s easy to forget what you did a few weeks (or even days) ago, and good documentation can save you a lot of headaches.
Stay Organized: Keep your workspace tidy, both physically and digitally. Organize your files, label your work, and clean up after you’re done. It might seem like extra work, but it makes things much easier in the long run.
Be Patient: Reverse engineering can be a slow process. It’s like solving a big, complex puzzle. Don’t rush it. Take your time, think things through, and remember, every step forward, no matter how small, is progress.
Keep Learning: The field of reverse engineering is always changing. New tools are being developed, new techniques are being discovered, and you need to stay on top of it. Never stop learning, because the moment you do, you start falling behind.
Practice, Practice, Practice: And finally, practice as much as you can. Theory is important, but there’s no substitute for hands-on experience. The more you practice, the better you’ll get.
And that’s it! Follow these guidelines and best practices, and you’ll be well on your way to mastering the art of reverse engineering. Remember, it’s a journey, not a race. So enjoy the process and keep pushing forward.
Practical Course: Applying Your Reverse Engineering Skills
So, we’ve talked a lot about reverse engineering, but talking and doing are two different things, right? Let’s look at how you can apply your shiny new reverse engineering skills in a practical way.
Choose a Project: Start with something simple, like a basic open-source program. You’re not trying to find hidden secrets; you’re just trying to understand how it works. As you get more comfortable, you can tackle more complex projects.
Use Your Tools: Remember those tools we talked about? This is where they come in. Disassemblers, debuggers, network analyzers – they’re all going to be your best friends. Get familiar with them and use them to dissect the program.
Document Your Findings: Keep track of what you find. It might not seem important now, but it might become crucial later on. A well-documented process can also help others learn from your work.
Try to Break It: Yup, you read that right. Try to find vulnerabilities or ways the program could be exploited. This is a great way to learn about software security and how to make software more robust.
Tinker and Modify: Don’t be afraid to get your hands dirty. Change some code, see what happens. It’s all part of the learning process.
Share Your Work: Once you’re done, share your findings with the community. It’s a great way to get feedback and learn from others. Plus, it contributes to the overall knowledge of the community.
Repeat: And finally, keep doing it. The more you practice, the better you’ll get. With every project, you’ll learn something new, face new challenges, and become a better reverse engineer.
So there you have it! A practical guide to applying your reverse engineering skills. It might seem challenging, but remember, every expert was once a beginner. So, start where you are, use what you have, do what you can, and most importantly, enjoy the process.
Conclusion
Well, here we are at the end of our deep dive into the wonderful world of reverse engineering. It’s been quite a journey, hasn’t it? From the basics to advanced techniques, from getting started to building a career, we’ve covered a lot. But remember, this is just the beginning of your journey.
The field of reverse engineering is vast and constantly evolving. There’s always something new to learn, a fresh challenge to tackle. But don’t let that intimidate you. Instead, let it inspire you. Remember, every expert was once a beginner. Every pro was once a novice. And every journey begins with a single step.
So, what’s your next step? Are you going to dive into a new project? Are you going to tackle a new challenge? Or maybe you’re going to share your newfound knowledge with others. Whatever you choose, know that you’ve got a solid foundation to build on, and a fascinating journey ahead of you.
Reverse engineering isn’t just about breaking things apart. It’s about understanding how things work. It’s about learning, growing, and solving problems. It’s about being a lifelong learner, and most importantly, it’s about enjoying the process.
So, go forth and reverse engineer. Break things, make things, learn things. But most importantly, have fun doing it. After all, the best part of learning is the journey, not the destination.
