We are living in the era of Cyber Security Threats, where the Internet is available at our fingertips, we even don’t care about who is tracking us, who are selling our data, who has an eye on our Bank Accounts, Credit Cards, even without our absence we are just enjoying the technology,
But remember everyone is being tracked, Search Engines also knows who is located at where and who is Buying what
In a day there may be hundreds of cyber-attacks across the globe, including data leaks, malware threats and harassment,
Even Big Companies are not able to protect their user data, that’s a big issue in this era,
Among that Doxing is different..!
You might hear of Doxing in the News articles, or somewhere but don’t have clarity about Doxing then don’t worry this post will be a good guide for you,
In this post am going to tell you what is Doxing, how Hackers dox someone and tell you the process of Doxing.
What is Doxing
so imagine you’re on the internet, right? And you know how people have their usernames, maybe a profile picture, and they share things about themselves? Well, doxing is when someone tries to find out a whole bunch more about a person than what they’ve shared willingly. It’s like they’re trying to dig up private info like their real name, address, phone number, and stuff like that.
Now, why would someone do this? Well, sometimes it’s not for good reasons. Some people might do it to harass or threaten someone, which is totally not cool. Other times, it might be to expose someone’s personal info to harm them or mess with their life.
Doxing is kind of like invading someone’s privacy, and it can be used in pretty harmful ways. That’s why it’s important to always be careful about what you share online and who you interact with. And if you see someone getting doxed or if you think someone is trying to dox you, it’s a good idea to report it and get help to stay safe.
Doxing is the process of investigating and posting personal information about an individual or organization on the internet.
The data includes sensitive information such as a person’s real name, date of birth, parents’ names, phone numbers, email addresses, websites, locations, IP addresses, and so on.
Hope you got a clear understanding of what does it mean to dox someone
What Does Dox Mean
So, you know how we all have our personal stuff, like our name, where we live, and our phone number, right? Well, when someone says “dox,” they’re talking about digging up all that private info about someone and making it public without their permission. It’s like sharing someone’s secrets with the whole world, and that’s definitely not cool.
I gotta say, doxing is a big invasion of privacy and it can cause a lot of trouble. People might do it to mess with someone, or to cause harm in some way. And you know what? It’s not something I’d recommend or support. Online safety is important, so it’s best to keep your personal stuff private and respect others’ privacy too.
Is doxing illegal?
Yeah, you’re right on the money. Doxing can actually be illegal in many places. See, when someone digs up and shares private info about someone without their consent, it’s not only a huge invasion of privacy but it can also lead to some serious consequences.
Laws vary from place to place, but in a lot of countries and regions, doxing can be considered a form of harassment or even stalking. Those are big no-nos when it comes to the law. So, if you’re thinking about doxing someone or if someone’s done it to you, it’s definitely a good idea to know your rights and get legal advice if needed.
Remember, online behavior has real-world consequences, so it’s smart to play it safe and treat others how you’d want to be treated.
Let’s see the real-life examples
Back in 2011, Anonymous and Lulzsec Started Doxing the FBI employees
In 2015 Anonymous published hundred of ISIS Twitter Accounts by Doxing,
you may ask me “is it illegal to dox someone”
Doxing is Not Legal at all, but it depends on the situations
Suppose Doxing is useful at hunting terrorists but it’s bad if you’re Doxing someone for harming their personal life
Who can Dox?
Doxing isn’t limited to a specific group of people—it can technically be done by anyone with access to the internet and some investigative skills. It doesn’t take a specialized background or knowledge to gather information about someone if they’ve left a digital trail online. However, the intentions behind doxing can vary widely.
Some individuals who might engage in doxing include:
- Online Trolls: People who want to harass or humiliate others might resort to doxing to publicly shame or threaten them.
- Hackers: Individuals with advanced computer skills might dig up personal information through hacking or exploiting security vulnerabilities.
- Vindictive Individuals: People with a grudge or personal vendetta might try to hurt someone by exposing their private details.
- Activists: In some cases, activists might use doxing as a form of protest or to hold individuals accountable for actions they disagree with.
- Privacy Advocates: Surprisingly, some individuals who care about privacy might expose information to show how easy it is to find someone’s personal details online, aiming to encourage better online security practices.
It’s important to note that doxing is generally considered unethical and can have serious legal, social, and personal consequences. Respecting privacy and treating others with kindness and empathy online is crucial for maintaining a healthy and respectful digital environment.
Why they Dox?
There is no particular reason to dox, they do because they need your personal information,
Let’s take an example
You meet someone on a forum or Facebook group and wanted to buy any service from him, after taking your payment he flies away and never be back,
Then what usually one does
- Tells others he was scammed by the guy
- Tells others not to deal with that guy
- If the scam was big enough then he goes to Cyber cell
But Hackers does the same, along with that they did something different that is Doxing..!
There are many reasons to dox anyone Maybe they need the email or phone number to bypass a login, or they need your info for making a fake identity
(That information can be used in many wrong ways, we aren’t going deep)
How to dox someone?
Before Doxing someone there are a few more questions left to be answered:
How easy is it to dox someone?
Doxing is not easy at all, it depends on your hard work and intelligence also on the target person
How long does it take to dox someone?
It depends on the person who you’re about to dox, also depends on your intelligence and hard work
Sometimes it may take a day, or some weeks, and several months
Before you try to dox someone you must have any one of the following info
- Full name
- Phone number
- Email address
- IP address
(The list is not limited but these are the basic clues that we use to dox someone) ‘
How to dox someone with their name and last name
If you have the target person’s Name then you can use that info for doxing,
Note:
There are a lot of tools out three on the internet, but first I recommend you to do some manual hunting
In my personal Doxing journey, Search Engines and a Blank Doc Sheet are my #1 Tools
So you have their name, just use google, bing & yahoo and search with their name
Make use of google dorks, that is worth our time
Now closely observe the Search Results, and go through the Social Media Accounts with that usernames, if any of the accounts are suspicious to you then, make a note of that profile URL, also if any other info is attached to the profile then note them also
Note:
Social Media Is Not Limited to Facebook and Twitter, it also includes various online forums, while using search engines, don’t just look for social media usernames also see the other publicly available information
To make our research easier, we have to make use of some tools but remember tools are always not free, still, you can make free ones
How to dox someone with IP adresses
Case ONE: Get the IP address of the target through tracking links
- Get the IP address of a target. To get the IP address of a target, a free online service can be used. Go to https://iplogger.org and select the option “Invisible image” (see Figure 1).
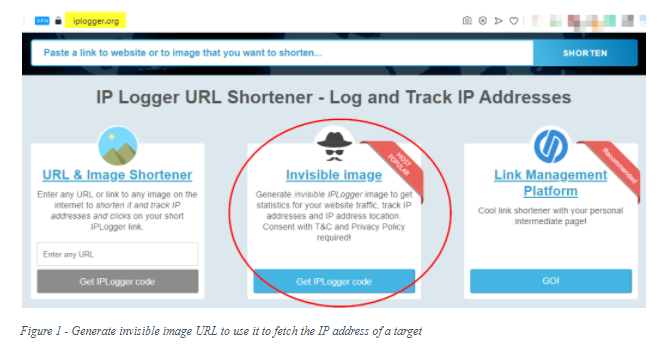
- The tracking dashboard, where one can customize a tracking link and observe the URL used to display the tracking results, is shown by IPLogger in the following screen (see Figure 2).
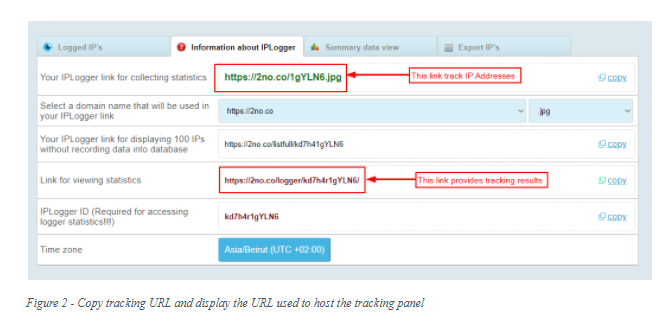
- Send the tracking link to the target. Deceive the target by inserting the tracking link inside an email message or send it via a social media message (e.g., Facebook chat).
- Once the recipient clicks the tracking URL, go back to the IP logger website and access the URL used for viewing statistics. The target IP address should appear here (see Figure 3).
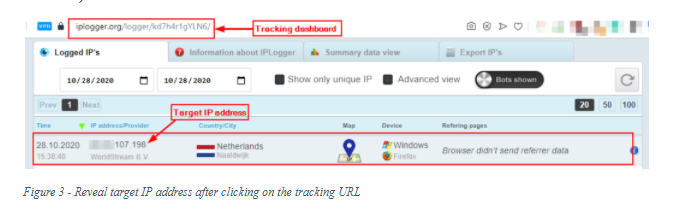
Case TWO: Get the IP address of the target by investigating email message header (If there is a previous email communication with the target)
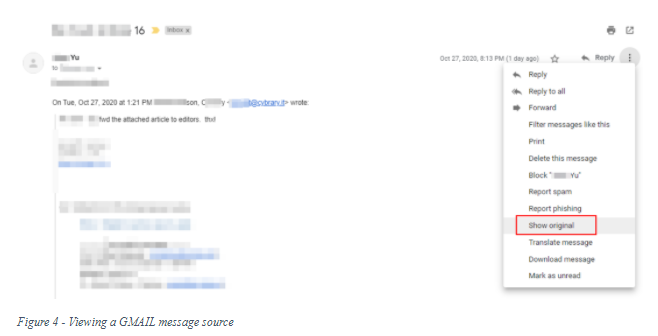
If your target has messaged you, you can get the IP from checking the email source. To do so for Gmail accounts, follow these steps:
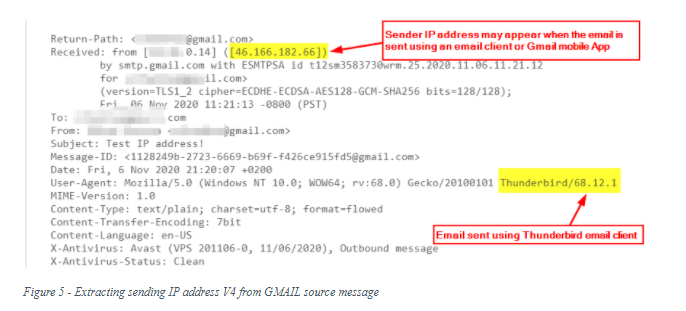
- Open the sender’s message in Gmail and click on “Show Original.” Now search for ‘Received’ within the code (see Figure 4 & 5) and copy the IPV4 address of the sender’s device. Make sure to start reading the email source from bottom to top.
- With a target IP address on hand, go to https://www.ipaddress.com/ and enter it to gain insights into records, such as WHOIS information. (see Figure 6). This resource provides information, such as the area, postal division, state, nation, ISP, and working framework. Take note of these details and continue onward.
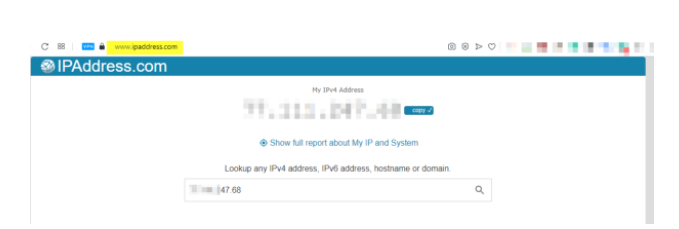
Figure 6 – Find IP address information using https://www.ipaddress.com
Important note when looking for the sender IP address on Gmail header
When using the Gmail web interface to send an email, Gmail omits the sender’s IP address (via web browsers). However, if the sender uses an email client to send the message, such as Microsoft Outlook or Mozilla Thunderbird, or when using the Gmail mobile application installed on an iPhone or an Android device to send that email, Gmail may include the sender’s IP address.
- Now, to find target public posts on Twitter, use the @ operator. Here’s an example: @someone (this will retrieve all tweets that reference the ‘someone‘ account).
- One can search for all instances where this username is used by knowing one of the target social media profile usernames. The following two services can be used for this purpose.
a. https://checkusernames.com b. https://namechk.com
- To search within social media sites, use the symbol @ followed by a social media name; then enter a colon in the search query. For example, enter @facebook:Someone Name to search for the term “Someone Name” within Facebook).
- To locate the target email address (if their name is known), enclose the target name with quotation marks. For example, enter “FirstName Lastname.”
- A reverse image search can be performed on a personal photograph. Go to Google Reverse Image Search and either upload the image there or paste the image’s URL into the search box (see Figure 7).

- Similar to standard search engines are people search engines. In order to provide information on demand, they index web content with an emphasis on personal information and store the findings in sizable databases. Use one of the following persons search engines to look up a target using his or her complete name, email address, or mailing address:
a. https://www.truthfinder.com b. https://www.411.com c. https://pipl.com
- Search for additional information using public records. Public records consist of information that has been—mostly—produced by government entities and is meant to be non-confidential. There are many public records repositories, such as:
a. https://www.genealogybank.com/explore/newspapers/all
b. https://www.familysearch.org/search/collection/1202535
c. http://www.melissadata.com/lookups/deathcheck.asp
d. http://www.obitsarchive.com
Doxing is the process of looking through publicly accessible sites for details (particularly personally identifying details) about a particular target. Such information can be located via open-source intelligence tools and tactics by searching through public databases, social media sites, and other places where data is available.
Doxing Through Hacked Databases
This is one of my favourite methods, in this methods, we have to search and investigate the victim’s email, Username or any clue to check whether his data might be leaked anywhere
Sometimes Hackers Hacks into different websites and dump their database then makes it public,
In this method, we will check whether his data is leaked online and collect the information
There are some tools to do a job, there is a Command-line tool, I recommend you to give a try,
Here is the tool: https://github.com/Ekultek/WhatBreach/blob/master/README.md
(Try Other tools too, but most of them will be Paid)
Dox Someone with his Photo
This method is extremely helpful when you’re about to check if the person is fake or original profile
Not only that it also good for reverse engineering,
In this method, we are basically checking whether the same photo is shared anywhere over the internet
I personally recommend you to the tool Google Image Search
Just Put The Photo and observe the search results
Conclusion
I hope you learnt, how to dox people, In this post, I tried my best to give you there comprehensive guide to doxing, and I think the tools are enough to dox but don’t limit them.

