Today I want to look at the methodology when attacking web login portals. I see many posts about different vulnerabilities in programs, but very little amount of people talks about this topic. Of course, there is some sense behind this, because without valid credentials, there is very little functionality to be exploited. For the same reason, these portals are often not well protected.
There are a few vulnerabilities/misconfigurations that will get you some good bug bounties or findings during an engagement, like:
- Default Credentials
- Username Enumeration
- Weak Lock Out mechanism
So, let’s deep dive into each one of them and see how this can earn you some money.
1. Default Credentials
Misconfigurations with default credentials can be seen everywhere & this is a vulnerability that is usually High or Critical, depending on the access that it gives you. The methodology behind this is very simple — first you need to find default credentials for the application that you are testing. Then find all the login portals, where you can use those credentials.
Because I already have a topic on this, I will not go into too much depth and will instead give you potential reads to show you that this really works:
- Critical Vulnerability Through OSINT only (by me): https://medium.com/@mares.viktor/critical-vulnerability-through-osint-only-56e56eb97516
- $350 DVR default username and password: https://hackerone.com/reports/398797
- Default Admin Username and Password: https://hackerone.com/reports/1195325
There are many other reports that have been disclosed on the topic, however I think those are enough to get you started. Let’s move on to the next one
2. Username Enumeration
The idea here is to verify if it is possible to collect a set of valid usernames by interacting with the authentication mechanism of the application
The methodology is to try logging in or resetting your password with an invalid email first and then try a possibly valid email (find emails via OSINT or register an account) and see the response from the website.
This is how a vulnerable page will look:
- Use an incorrect email (e.g. a@a.a) and check the response

2. Use a valid email and check the response

As you can see from the above example, the password reset allows us to enumerate users. If you are doubting whether this is impactful, please see some reports:
- $100 Email enumeration at SignUp page: https://hackerone.com/reports/666722
- User enumeration through forgot password: https://hackerone.com/reports/1166054
- Username Enumeration: https://hackerone.com/reports/667613
Now, let’s move on to a bit of a more interesting attack.
3. Weak Lock Out mechanism
What is it ?
Account lockout mechanisms are used to mitigate password spraying or brute force attacks. Accounts are typically locked after 3 to 5 unsuccessful login attempts and can only be unlocked after a predetermined period of time, via a self-service unlock mechanism, or intervention by an administrator.
How to test for it?
I have a really simple methodology, that goes as follows:
- Find valid usernames & passwords (through breach databases)
- Try enumerating existing usernames (if possible)
- Try a brute force attack
- Try a credential stuffing & password spraying attack
So, let’s start looking into each one of these and see how you can do all of this as well.
Finding Valid Usernames & Passwords
- [FREE] Use the Breach Parse to find plaintext credentials — https://github.com/hmaverickadams/breach-parse
- [BEST] Use Leak Peek, to find the latest plaintext credentials (for a subdomain) — https://leakpeek.com/
- Same as Leak Peek, but a bit more expensive — https://www.dehashed.com/
All of the above resources work in the same way. Let’s say that you are attacking example.com and you have a login portal at example.com/login. You can try enumerating all of the emails of the domain @example.com that have been breached in the past.

NB: Please, do make sure that you are only using the data that you gather for ethical hacking purposes & that your bug bounty program or penetration testing engagement does allow this attack vector
Also, know that you can search by username, email, password and more.
Enumerating Usernames
This has already been explained in point 2 (Username Enumeration) — the idea is to see if the emails/usernames that you have gathered are valid. This might not always be possible however and we might have to just go with the attack anyways.
Starting a Brute Force Attack
I would only do this, if I am sure that the web application allows this.
Below is an example, that shows the web application will disable our login if we try guessing the password more than 3 times.
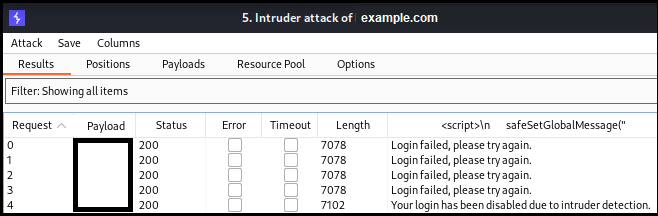
However, if I see that the password is not being disabled, I would usually attack each email/username with my own wordlist:

Of course, if you are unsure of the password requirements, then you can just use the normal rockyou.txt wordlist: https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
Credential Stuffing & Password Spraying
Finally, we get to the most successful attacks, which are the Credential Stuffing & Password Spraying attacks.
What is Credential Stuffing? Remember, how we could use breach parse or leak peek to get valid plaintext credentials (username & password) of our targets? Well, credential stuffing is the process of using all those credentials against a login portal.
What is Password Spraying? Well, password spraying is a bit different. The idea here is to use all those collected emails or usernames & attack all of them with the same password. Let’s say that we have collected 50 emails of a company. We then find a login portal & attack each of these emails with a known-bad password (like P@ssw0rd or Summer2022! and others).
Below is a really good video on this, by The Cyber Mentor (from TCM Academy) who basically explains & shows the whole concept of this attack.
Credential Stuffing & Password Spraying: https://youtu.be/sH4JCwjybGs?t=11222
And here are some reports that may help you in understanding these attacks more:
- $100 [dubsmash] Username and password bruteforce: https://hackerone.com/reports/1165225
- $420 Ability to bruteforce mopub account’s password due to lack of rate limitation protection using {ip rotation techniques}: https://hackerone.com/reports/819930
Hopefully, I was able to show you something interesting and useful for your future engagements in bug bounty programs & penetration tests.
