In the world of cybersecurity, brute force attacks are one of the most common and dangerous types of attacks. These attacks are often used by hackers to gain unauthorized access to a system or network by attempting to guess a user’s login credentials. Blue Team Bootcamp Series (P1): How to Detect Brute Force Attacks provides a comprehensive guide for detecting brute force attacks and protecting against them.
What is a Brute Force Attack?
A brute force attack is a type of attack in which an attacker tries to guess a user’s login credentials by systematically trying every possible combination of usernames and passwords until the correct one is found. Brute force attacks can be extremely time-consuming and resource-intensive, but they can also be highly effective if the attacker is able to guess the correct credentials.
What are brute force attacks and why are they so dangerous?
Brute force attacks are a type of cyber attack where an attacker tries to gain access to a system or account by repeatedly guessing a password or encryption key until they succeed. This type of attack is called “brute force” because it relies on the attacker’s ability to try every possible password combination until they find the correct one.
Brute force attacks are dangerous because they can be highly effective, especially against weak passwords. If an attacker gains access to a system or account, they may be able to steal sensitive information, install malware or ransomware, or carry out other malicious activities.
One of the reasons why brute force attacks are so dangerous is because they can be automated, which means that attackers can use software to carry out the attack quickly and efficiently. This makes it possible for attackers to try a large number of password combinations in a short amount of time, increasing the chances of success.
Another reason why brute force attacks are dangerous is because they can be difficult to detect. If an attacker is using a slow and steady approach, it may be difficult to tell if they are even attempting a brute force attack. This is why it is important to have robust security measures in place to prevent and detect these types of attacks.
Types of Brute Force Attacks
- Simple brute force attack—uses a systematic approach to ‘guess’ that doesn’t rely on outside logic.
- Hybrid brute force attacks—starts from external logic to determine which password variation may be most likely to succeed, and then continues with the simple approach to try many possible variations.
- Dictionary attacks—guesses usernames or passwords using a dictionary of possible strings or phrases.
- Rainbow table attacks—a rainbow table is a precomputed table for reversing cryptographic hash functions. It can be used to guess a function up to a certain length consisting of a limited set of characters.
- Reverse brute force attack—uses a common password or collection of passwords against many possible usernames. Targets a network of users for which the attackers have previously obtained data.
- Credential stuffing—uses previously-known password-username pairs, trying them against multiple websites. Exploits the fact that many users have the same username and password across different systems.
How Brute Force Attacks Work
Let’s see how brute force attack works now. Attackers have a handful of readily and freely available tools (such as Metasploit, John the Ripper, Hydra, etc.).
Most of the time, attackers use automated tools or scripts with a list of usernames and passwords. The tool will automatically send the combination of these usernames and passwords to the targeted system, such as a web application server. The tool will check if the authentication is successful or not.
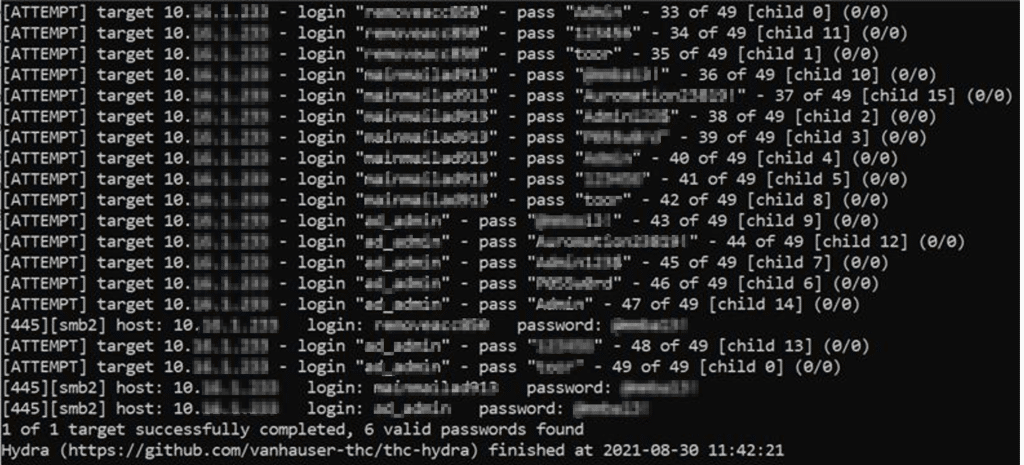
Here is a screenshot of the Hydra tool launching a brute force attack and the valid passwords found against the targets.
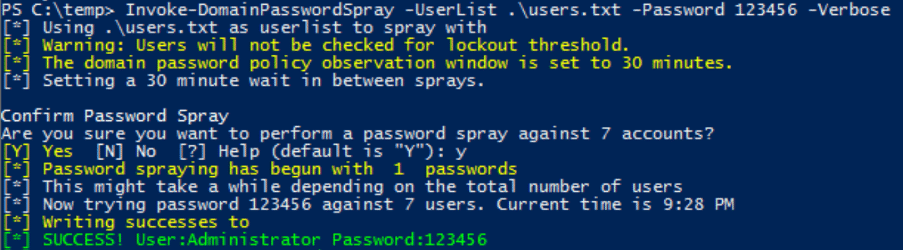
Here is another screenshot of the “DomainPasswordSpray” tool.
Another post-exploitation tool called CrackMapExec (CME) targets Active Directory user accounts to conduct lateral movement. The CME can also brute force passwords for a specified user on a single target system or across an entire network. The following examples show how attackers use CME to brute force credential authentication by using a supplied list of usernames and a single password.
Examples:
<code>crackmapexec 10.0.100.0/24 -u ‘admin’ -p ‘P@s$w0Rd’</code>
<code>crackmapexec <protocol> <target(s)> -u username1 username2 -p password1</code>
<code>crackmapexec <protocol> <target(s)> -u ~/file_usernames -p ~/file_passwords</code>
The remote desktop protocol (RDP) brute force attack is one of the most common methods attackers use to gain access to Windows workstations or servers. This method is so successful that ransomware groups have used open RDP ports to deliver malware payloads.
How to Detect Brute Force Attacks
There are several ways to detect brute force attacks. Here are some of the most effective methods:
Log Analysis
Log analysis is an essential method to detect brute force attacks. When reviewing logs, look for repeated login attempts from the same IP address or the same user account. If you see multiple failed login attempts from the same IP address or user account within a short period of time, it could be a sign of a brute force attack.
It is important to keep track of all system logs and analyze them regularly. Logs are generated by various system components, including servers, firewalls, intrusion detection systems, and antivirus software. By analyzing logs from all of these sources, you can gain a comprehensive view of your system’s security and quickly detect any malicious activity.
Traffic Analysis
Traffic analysis is another way to detect brute force attacks. Look for large amounts of traffic coming from a single IP address or a group of IP addresses. If you see a large number of login attempts from a single IP address or group of IP addresses, it could be a sign of a brute force attack.
It is important to monitor network traffic on a regular basis to detect any unusual activity. There are various tools available for monitoring network traffic, such as Wireshark and tcpdump. By analyzing network traffic, you can quickly detect any malicious activity and take steps to prevent further attacks.
Intrusion Detection Systems (IDS)
An Intrusion Detection System (IDS) can also be used to detect brute force attacks. IDS systems can be set up to look for specific patterns of traffic that are indicative of a brute force attack. If the IDS system detects a pattern of traffic that matches the criteria, it can alert the system administrator.
There are two types of IDS: host-based IDS and network-based IDS. Host-based IDS runs on individual systems and monitors system logs and events for signs of intrusion. Network-based IDS monitors network traffic and can detect attacks that may have bypassed host-based IDS. By using both types of IDS, you can get a comprehensive view of your system’s security and detect any suspicious activity.
Rate Limiting
Rate limiting is another effective method for detecting and preventing brute force attacks. Rate limiting involves limiting the number of login attempts that can be made within a certain time period. For example, you might limit the number of login attempts to five per minute. If someone tries to exceed this limit, their IP address can be blocked or their account can be temporarily locked.
Rate limiting is an effective way to prevent brute force attacks because it slows down the attacker’s progress and makes the attack much more time-consuming. It also helps to prevent the attacker from overwhelming your system with login attempts, which can cause your system to crash or become unresponsive.
Strong Password Policies
One of the most effective ways to prevent brute force attacks is to enforce strong password policies. Passwords should be long, complex, and include a mix of uppercase and lowercase letters, numbers, and special characters. Passwords should also be changed regularly.
It is also important to educate users on how to create strong passwords and to encourage them to use unique passwords for each account. By enforcing strong password policies, you can significantly reduce your risk of being targeted by brute force attacks.
Two-Factor Authentication
Two-factor authentication is another effective way to prevent brute force attacks. With two-factor authentication, users are required to enter a second form of identification, such as a code sent to their phone or email, in addition to their username and password.
Two-factor authentication provides an extra layer of security and makes it much more difficult for attackers to gain unauthorized access to your system. Even if an attacker manages to obtain a user’s username and password, they will still need the second form of identification to gain access. Two-factor authentication can be implemented using various tools and services, such as Google Authenticator or Duo Security.
IP Blocking
IP blocking is another effective method for preventing brute force attacks. If you notice repeated login attempts from a specific IP address, you can block that IP address from accessing your system. This can be done using various tools, such as firewalls or security software.
Blocking an IP address can be an effective way to prevent a brute force attack, but it is important to be careful when using this method. If you block legitimate IP addresses, it can cause problems for your users and potentially damage your reputation. It is important to carefully analyze your logs and traffic before blocking any IP addresses.
CAPTCHA
Finally, CAPTCHA can be used to prevent brute force attacks. CAPTCHA is a security measure that requires users to complete a task that is easy for humans but difficult for automated scripts. For example, users may be asked to identify a series of images or to type in a set of distorted letters and numbers.
CAPTCHA can be used to prevent brute force attacks by slowing down attackers and making it more difficult for them to automate login attempts. By requiring users to complete a CAPTCHA, you can significantly reduce the risk of brute force attacks.
Hydra and Other Popular Brute Force Attack Tools
Hydra is one of the most popular brute force attack tools available today. It is a command-line tool that is used for attacking remote systems, networks, and web applications. Hydra is open-source software, and it supports a wide range of protocols, including HTTP, FTP, SMTP, SSH, and Telnet.

Hydra works by attempting to login using a list of possible usernames and passwords. It can also be used to try different combinations of usernames and passwords, making it a powerful tool for attackers. Hydra has a number of different options and features, making it highly customizable and adaptable to different attack scenarios.
Another popular brute force attack tool is Medusa. Medusa is similar to Hydra in that it is a command-line tool that can be used to attack remote systems and networks. It supports a wide range of protocols, including HTTP, FTP, SMB, and Telnet.
Medusa works by using a list of possible usernames and passwords to attempt to login to a system or network. It can also be used to try different combinations of usernames and passwords, and it supports a range of different authentication methods.
Other popular brute force attack tools include Ncrack, THC Hydra, and Brutus. These tools all work in a similar way to Hydra and Medusa, and they are used to attack a wide range of systems and networks.
It is important to note that these tools are not inherently malicious, and they can be used for legitimate purposes, such as penetration testing and network security auditing. However, they can also be used by attackers to carry out malicious activities, such as stealing sensitive information, installing malware or ransomware, or carrying out other types of cyber attacks.
Other top brute force tools are:
- Aircrack-ng—can be used on Windows, Linux, iOS, and Android. It uses a dictionary of widely used passwords to breach wireless networks.
- John the Ripper—runs on 15 different platforms including Unix, Windows, and OpenVMS. Tries all possible combinations using a dictionary of possible passwords.
- L0phtCrack—a tool for cracking Windows passwords. It uses rainbow tables, dictionaries, and multiprocessor algorithms.
- Hashcat—works on Windows, Linux, and Mac OS. Can perform simple brute force, rule-based, and hybrid attacks.
- DaveGrohl—an open-source tool for cracking Mac OS. Can be distributed across multiple computers.
- Ncrack—a tool for cracking network authentication. It can be used on Windows, Linux, and BSD.
Weak Passwords that Enable Brute Force Attacks
Today, individuals possess many accounts and have many passwords. People tend to repeatedly use a few simple passwords, which leaves them exposed to brute force attacks. Also, repeated use of the same password can grant attackers access to many accounts.
Email accounts protected by weak passwords may be connected to additional accounts, and can also be used to restore passwords. This makes them particularly valuable to hackers. Also, if users don’t modify their default router password, their local network is vulnerable to attacks. Attackers can try a few simple default passwords and gain access to an entire network.
Some of the most commonly found passwords in brute force lists include: date of birth, children’s names, qwerty, 123456, abcdef123, a123456, abc123, password, asdf, hello, welcome, zxcvbn, Qazwsx, 654321, 123321, 000000, 111111, 987654321, 1q2w3e, 123qwe, qwertyuiop, gfhjkm.
Strong passwords provide better protection against identity theft, loss of data, unauthorized access to accounts etc.
How to Prevent Brute Force Password Hacking
To protect your organization from brute force password hacking, enforce the use of strong passwords. Passwords should:
- Never use information that can be found online (like names of family members).
- Have as many characters as possible.
- Combine letters, numbers, and symbols.
- Be different for each user account.
- Avoid common patterns.
As an administrator, there are methods you can implement to protect users from brute force password cracking:
- Lockout policy—you can lock accounts after several failed login attempts and then unlock it as the administrator.
- Progressive delays—you can lock out accounts for a limited amount of time after failed login attempts. Each attempt makes the delay longer.
- Captcha—tools like reCAPTCHA require users to complete simple tasks to log into a system. Users can easily complete these tasks while brute force tools cannot.
- Requiring strong passwords—you can force users to define long and complex passwords. You should also enforce periodical password changes.
- Two-factor authentication—you can use multiple factors to authenticate identity and grant access to accounts.
Conclusion
Brute force attacks are a common type of attack that can be devastating to your system’s security. However, with the right tools and techniques, you can effectively detect and prevent these attacks. By using log analysis, traffic analysis, IDS, rate limiting, strong password policies, two-factor authentication, IP blocking, and CAPTCHA, you can significantly reduce your risk of being targeted by brute force attacks.
It is important to remember that security is an ongoing process. You should regularly review your system’s logs and traffic to ensure that you are detecting any suspicious activity. You should also keep up to date with the latest security threats and trends and adjust your security measures accordingly.
By following these best practices, you can ensure that your system remains secure and protected against brute force attacks and other types of security threats.
