Hi there! I’m Rocky, you already know who i am as you are here in codelivly. Today, I’m going to guide you through the thrilling world of Android penetration testing. Now, you might wonder what this term means and why it’s so important. Trust me, whether you’re a cybersecurity enthusiast, an aspiring ethical hacker, or simply an Android user who wants to understand more about the security of your device, you’re in the right place.
Android penetration testing, at its core, is all about probing Android systems and identifying potential vulnerabilities. Imagine it like a routine health check-up for your Android system – just like how doctors diagnose patients and suggest a course of treatment, we ethical hackers dive deep into these systems, uncover any weaknesses, and recommend appropriate remediation. The ultimate aim? To make Android systems healthier and safer.
But why is Android penetration testing so critical? Well, as of my last check, Android holds over 70% of the global mobile operating system market share. That’s millions of devices and, consequently, millions of potential targets for attackers. By carrying out Android penetration testing, we can identify and fix vulnerabilities before malicious hackers have a chance to exploit them.
Now, let’s imagine you’re at a bustling airport. There are security checks at every corner, ensuring the safety of all passengers. In the realm of Android systems, these security checks resemble the various stages of penetration testing – probing, analyzing, and securing.
For instance, suppose we have an Android app, let’s call it ‘FlySafe.’ FlySafe is an app that securely stores all your travel documents. Now, wouldn’t you want to make sure that it’s truly secure? That’s where Android penetration testing comes into play. We would conduct rigorous tests, attempting to bypass security measures, mimic potential attacks, and understand how the app reacts to them. All this to ensure that when you use FlySafe, your data is as safe as it can possibly be.
Throughout this guide, we’ll explore different aspects of Android penetration testing, understand its nuances, and walk through the process step-by-step. I’ll share with you some tools of the trade, give you an overview of the Android architecture, and show you how to set up a testing environment right on your computer.
I’ve designed this guide to be beginner-friendly, so don’t worry if you’re just stepping into the world of cybersecurity. We’re all here to learn, and Codelivly is just the platform to facilitate that. Remember, no question is too silly, and every little learning takes us one step closer to a safer digital world.
Understanding Android Architecture

So, now that we’ve understood what Android penetration testing is all about, it’s time to delve deeper. Just as we wouldn’t go for a hike without understanding the lay of the land, we won’t start our penetration testing journey without understanding the structure of Android. Yes, I’m talking about Android architecture.
Imagine Android architecture as a multilayered cake, each layer having its own flavor and purpose, coming together to make the complete cake – that’s Android OS for you. This multi-layered structure is vital to the functioning of your device and, more importantly, to our Android penetration testing exploration.
Let’s walk through these layers one by one:
- Linux Kernel: This is the base layer, the bedrock of our Android architecture cake. It acts like the heart of Android OS, controlling everything from hardware drivers to power management. When you touch your screen, type on the keyboard, or even play music, the kernel is at work. For Android penetration testers, understanding how the kernel works helps in identifying hardware-based vulnerabilities.
- Hardware Abstraction Layer (HAL): Think of HAL as a translator. It standardizes hardware access for the higher-level Java API framework. It’s like having a friend who knows both your local dialect and the international language and can bridge the communication gap between the two. This layer can provide insight into potential hardware-software miscommunication vulnerabilities during Android penetration testing.
- Android Runtime (ART) and Native C/C++ Libraries: These two layers work hand in hand. ART is there to ensure your apps run smoothly using ahead-of-time (AOT) and just-in-time (JIT) compilation. On the other hand, the native libraries, written in C/C++, support various system functions like graphics rendering and database management. When conducting Android penetration testing, understanding these libraries can aid in spotting memory management and data leakage issues.
- Java API Framework: It’s the interface that developers interact with when writing Android apps. It provides high-level services such as Activity Manager, Content Providers, and Telephony Manager. Vulnerabilities here could expose sensitive functionalities of Android applications, making it a crucial layer for Android penetration testing.
- System Apps: These are your everyday apps like Contacts, Phone, and Browser that come pre-installed with the OS. Remember, these apps have the same capabilities as any third-party apps you install later on. Hence, a keen eye on these during Android penetration testing could prevent security loopholes right at the system level.
The beauty of Android’s open-source nature is that it allows us to understand, poke, and prod these layers in depth. This aids in our quest for secure systems, giving us a unique advantage during Android penetration testing.
Throughout this guide, we’ll refer back to this architecture and explore how different layers come into play during testing. As we understand the architecture better, we’ll start to see why certain vulnerabilities exist and how we can fix them.
Android Penetration Testing Environment Setup
Alright, we’re making good progress here! Now that we’ve got a handle on the Android architecture, it’s time to get our hands dirty. The next logical step in our Android penetration testing journey is to set up our testing environment. Think of this as the garage where we tinker and tweak, trying to understand the inner workings of Android systems.
Setting up a robust Android penetration testing environment is just as crucial as understanding the testing process itself. Having the right tools in your toolbox can make the difference between finding a potential security hole and letting it slip through the cracks. So let’s dive in and start setting up our playground.
- Hardware and Software Requirements: First and foremost, you need a computer with a stable internet connection. While most modern computers should work, remember that some tools we’ll use might require a hefty amount of resources. Ideally, you’ll want a machine with a decent processor, ample storage, and at least 8GB RAM.
- Virtual Machine: Next up, we need to set up a virtual machine (VM). Think of a VM as a computer within your computer, a safe sandbox where we can experiment without messing up our actual systems. There are various VM software options available, but VirtualBox and VMWare are popular choices.
- Operating System: For Android penetration testing, we will need an operating system designed for ethical hacking. Kali Linux is a crowd favorite in the cybersecurity community because of its pre-installed penetration testing tools. Once we have Kali Linux installed on our VM, we’re ready to dive deeper.
- Android SDK: The Android Software Development Kit (SDK) is a set of development tools used to develop applications for Android OS. The SDK includes an emulator where we can run and test our Android applications.
- Mobile Device: While it’s possible to do a lot of testing on the emulator, having an actual Android device can come in handy for more advanced testing scenarios. It’s recommended to use a device that you don’t mind wiping clean, as some tests could potentially interfere with your personal data.
- Penetration Testing Tools: Finally, we’ll need to install some specific tools designed for penetration testing. These include APKTool for reverse engineering Android apps, Drozer for security assessments, and Burp Suite for analyzing web traffic, among others.
Remember, setting up an Android penetration testing environment is like laying the foundation for a house. A solid foundation will ensure that the house (or in our case, the testing process) is secure and effective.
Don’t worry if some of these concepts sound intimidating. I assure you that as we delve deeper into Android penetration testing, they’ll become as familiar as your morning coffee routine. The world of cybersecurity might seem vast and complex, but that’s what makes it exciting!
Android Application Analysis

Well done, mate! We’ve got our Android penetration testing lab up and running. It’s like we’ve donned our detective hats, and now it’s time to start investigating. In this section, we’ll dive into Android application analysis.
Application analysis is like peering under the hood of an app, trying to understand its inner workings. We’ll break it down into three types: Static Analysis, Dynamic Analysis, and Reverse Engineering. Sounds cool, right? Let’s dive deeper.
- Static Analysis: Think of static analysis as studying an app when it’s not running. It’s like examining a car parked in a garage. We inspect the application’s code, resources, and assets to understand what it might do when executed. Tools like APKTool and jadx are invaluable for static analysis. They help us decode the APK file and dig into the code. By analyzing the code, we can identify weak spots, insecure coding practices, and even potential backdoors. In the world of Android penetration testing, static analysis is our first line of investigation.
- Dynamic Analysis: Now, imagine that car we were studying is revved up and speeding down the highway. Dynamic analysis is similar, where we monitor an application as it runs in real time. We observe how it interacts with the system, network, and data. This helps us identify how actual data flows through the app, potential leakages, or unintended interactions with the system. Tools like Drozer, Frida, and Burp Suite are instrumental for dynamic analysis in Android penetration testing.
- Reverse Engineering: This is where things get really interesting. Reverse engineering is the process of deconstructing an application to understand its functionality. It’s like dismantling that car piece by piece to see how everything fits together. In Android penetration testing, we use reverse engineering to peek into an app’s logic, flow, and structure, identifying potential vulnerabilities that may not be visible on the surface. Tools like JADX and Ghidra are our companions in this journey.
Remember, each app is a world in itself, unique in its way. That’s what makes Android penetration testing a fascinating task. It’s like solving a new puzzle each time, with its own set of challenges and rewards. With each application we analyze, we learn something new, further refining our testing skills.
Android package (APK) file structure explained
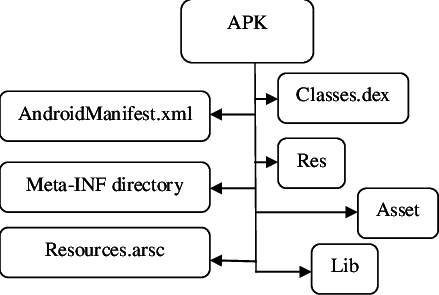
You know how a magician’s hat holds all those surprising tricks? That’s how I like to think of APK files – like little magic boxes containing everything an Android app needs to work its wonders. When you download an app from the Play Store, what you get is an APK file.
So, what’s inside this magical package? Let’s find out:
- AndroidManifest.xml: This is like the blueprint of the app. It contains crucial information about the app, such as its package name, permissions it requires, activities, services, and receivers it uses, and much more. It’s like the mastermind behind the scenes.
- classes.dex: Ah, the heart of the app! This file holds all the compiled code written in Java or Kotlin, ready to be executed by the Android Runtime. It’s like the engine that powers the app’s functionality.
- resources.arsc: This little guy is the treasure chest of resources – images, strings, layouts, and more. It helps the app present itself in all its glory to the user.
- lib folder: Inside this folder, you’ll find native libraries compiled for different architectures like ARM, x86, etc. It’s like a multilingual crew working together to make the app run smoothly on various devices.
- assets folder: Here’s where the app keeps additional data, like audio files or databases. It’s like the secret storage room, holding extra goodies the app might need.
- META-INF folder: This folder houses the signatures and certificates that ensure the APK’s integrity. It’s like the app’s personal bodyguard, ensuring no unauthorized changes sneak in.
So, you see, an APK is a treasure trove of essential files that come together to create the magic of your favorite Android apps.
Now, why is understanding the APK structure important for Android penetration testing? Well, just like a detective needs to know how a magic trick works, we ethical hackers need to understand the app’s inner workings to identify potential vulnerabilities. By dissecting the APK file, we can uncover secrets and weaknesses that might be lurking inside.
Start with the OWASP Mobile Top Ten to find vulnerabilities
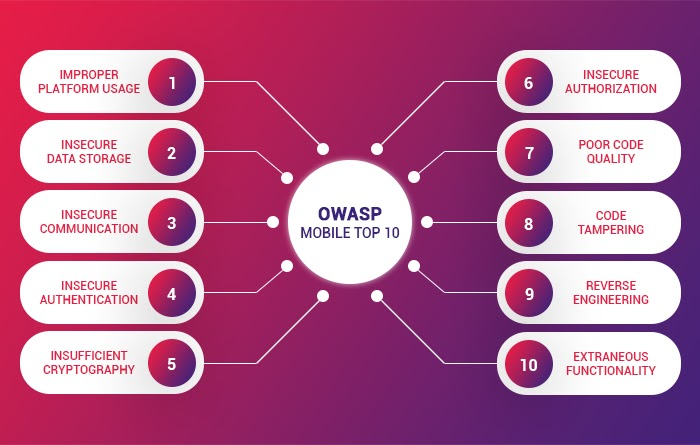
Alright, fellow Android penetration testers, here’s a valuable tip to get you started on your quest for finding vulnerabilities – the OWASP Mobile Top Ten. It’s like having a treasure map that points you straight to potential security risks in mobile apps.
Now, you might be wondering, “What’s OWASP?” Well, it’s a group of cybersecurity experts who have compiled a list of the top ten most critical mobile app security risks. Think of it as a guidebook to navigate the treacherous waters of mobile application vulnerabilities.
So, let’s dive into this treasure trove and see what it holds:
- Improper Platform Usage: This risk points out mistakes in using Android or iOS features that could lead to vulnerabilities. It’s like not using the right tools for the job, and it might open doors for malicious hackers.
- Insecure Data Storage: Ah, the secret chamber where sensitive data might be hidden. This risk is about not protecting data properly, leaving it exposed to prying eyes.
- Insecure Communication: Watch out for those unencrypted data highways! This risk warns us about transmitting data without proper security, making it an easy target for eavesdroppers.
- Insecure Authentication: This is like having a weak lock on your treasure chest. It’s about flawed authentication processes that could let unauthorized users sneak in.
- Insufficient Cryptography: It’s all about the strength of our encryption techniques. Weak encryption could be an open invitation for attackers to crack the code.
- Insecure Authorization: This risk is like having a guard who can be easily fooled. It’s about flaws in how apps decide who gets access to what.
- Client Code Quality: This warns us about weak coding practices that could lead to security holes. It’s like having holes in your ship that might sink it in rough waters.
- Code Tampering: Beware of those who try to change the rules of the game! This risk is about attackers modifying the app’s code to suit their evil plans.
- Reverse Engineering: It’s like having spies trying to figure out your app’s secrets. This risk is about attackers deconstructing the app to understand and exploit its weaknesses.
- Extraneous Functionality: Last but not least, beware of unused and unnecessary features. They could be potential entry points for cunning hackers.
So, there you have it – the OWASP Mobile Top Ten, your trusty guide in the world of Android penetration testing. As we embark on this adventure, remember to keep an eye out for these risks. Armed with this knowledge and the resources at Codelivly, there’s no vulnerability we can’t uncover and conquer. Happy hunting, fellow hackers!
Network-level Penetration Testing for Android Applications
Imagine the internet as an intricate network of roads, with data as cars zipping across them. These cars are moving from your device to servers and back again. Network-level penetration testing involves scrutinizing these roads and the cars on them. More specifically, we examine how data moves from an Android application to the server and vice versa.
Why is this important? Picture this: You’ve just entered your credit card details into an app. That information is sent to the server for processing. In an ideal world, it would be a safe and smooth journey. But what if there were hijackers (read: hackers) lurking around? You wouldn’t want your sensitive data to fall into the wrong hands, right? That’s where network-level penetration testing for Android applications comes in. We identify potential weak spots in the data’s journey and fortify them against malicious attempts.
Here’s how we go about it:
- Traffic Analysis: Our first task is to analyze the data traffic between the application and the server. We look for any unprotected data that might be visible to anyone snooping around. For this, we use tools like Wireshark or Burp Suite to capture and inspect this data traffic. This practice is like watching the cars on the road and checking if they have proper locks.
- Man-in-the-Middle Attack (MITM) Testing: Next, we simulate a Man-in-the-Middle attack. It’s like pretending to be a rogue cop trying to intercept the cars. We want to see if the application’s data can be intercepted and tampered with while in transit. MITM attacks are a common threat in the digital world, and we want to ensure our app is resilient against such attempts. Tools like Burp Suite or MITM Proxy can help us perform this test.
- Server-side Testing: Finally, we examine the server side of things. We try to understand how the server responds to our app’s requests and how it processes the data. Here, we’re looking for any vulnerabilities that might expose sensitive data or grant unauthorized access.
Remember, in the world of Android penetration testing, network-level testing is our lookout tower. It gives us a bird’s eye view of potential vulnerabilities that could jeopardize data security. And as always, it’s not just about identifying vulnerabilities but also about devising strategies to fortify them.
Client-side Penetration Testing
Remember when we talked about the network-level testing? Think of it as checking the roads for any threats. Client-side penetration testing, on the other hand, is like scrutinizing the car itself (i.e., the application). We’re looking for any vulnerabilities that a user might inadvertently trigger or a hacker might exploit.
Here’s how we approach client-side penetration testing:
- Input Validation Testing: This is the first thing we check. We’re testing how the application handles user input. What happens if we enter something unexpected? Does the app crash, or does it behave oddly? These anomalies can potentially be exploited by a savvy hacker. We use fuzzing tools, like AFL or Radamsa, to throw a wide range of inputs at the application and see how it reacts.
- Storage Testing: Next, we look at how the application stores data. Is sensitive information being stored securely? Is it properly encrypted? If the data is stored insecurely, it could be a gold mine for a malicious actor. Android provides several storage options, each with its own set of security considerations. We analyze these to ensure data is securely handled.
- Permissions Testing: Here we scrutinize the permissions the app requests. Is the application asking for more permissions than it needs? Overly broad permissions could be a red flag, signaling potential privacy issues.
- Session Handling Testing: Finally, we inspect how the application handles sessions. Does it time out appropriately? Is the session data stored securely? Poor session management can leave the door open for attacks like session hijacking.
In Android penetration testing, client-side testing helps us identify potential vulnerabilities on the user’s device. It’s like running a health check on the car to ensure it’s in top shape and secure for all its occupants.
Server-side Penetration Testing
Our journey in Android penetration testing has been nothing short of exciting, and I’m thrilled to have you aboard. We’ve looked at the network, the client, and now, it’s time to shift our gaze towards the server. In this segment, we’ll explore Server-side Penetration Testing.
Picture this: our car (the client-side app) has traveled the roads (the network), and now we’re inspecting the destination – the garage, or in our case, the server. Just like ensuring the roads are safe and the car is secure, we need to make sure the server – where much of the application’s heavy lifting occurs – is rock solid against potential attacks.
Here’s a peek into the server-side penetration testing process:
- Security Misconfigurations: We start by looking for any security misconfigurations on the server. These are like unlocked or poorly guarded doors that could let a hacker waltz right in. We check for unnecessary open ports, default credentials still in use, improperly set permissions, and other such security oversights.
- Data Validation and Injection Attacks: Next up is testing how the server handles data. We need to make sure it properly validates input data before processing it. If not, it could be vulnerable to injection attacks such as SQL, OS, or LDAP injection, where a hacker could ‘inject’ malicious commands via the input data.
- Authentication and Session Management: We also examine how the server handles authentication and session management. Are user credentials stored and transmitted securely? Does the server properly manage user sessions, timing them out when necessary? Poor practices here could lead to unauthorized access.
- Sensitive Data Exposure: Finally, we check if the server is inadvertently exposing sensitive data. This could happen due to inadequate encryption or mishandling of data. For example, credit card details or personal user information should be properly encrypted both in transit and at rest.
In the world of Android penetration testing, server-side testing is crucial. It’s like ensuring the garage where we park our car is secure. After all, a robust app and a secure network would be futile if the server – the heart of operations – is vulnerable.
Advanced Android Penetration Techniques
Advanced penetration testing techniques are like secret weapons in our cybersecurity arsenal. They allow us to uncover deeper, more hidden vulnerabilities that might escape a basic test. Ready to get started? Let’s go!
- Bypassing Root Detection: Some Android apps have root detection mechanisms, which can prevent them from running on rooted devices. However, we often need root access for deep-level testing. So, how do we get around this? Using tools like Xposed Framework and modules like RootCloak, we can hide our root status and bypass these detections. It’s like having an invisibility cloak in the world of Android penetration testing!
- Reverse Engineering and Code Injection: Earlier, we touched on reverse engineering. But let’s take it a step further. Tools like Frida and Xposed not only let us peek inside the app’s code, but they also allow us to modify it. We can inject our own code snippets to test how the application reacts. This is a potent technique for uncovering hidden vulnerabilities.
- Binary Patching: This involves directly modifying the application’s binary code. It’s like reprogramming the app’s DNA. This advanced technique lets us change the app’s behavior, bypass security checks, or unveil hidden functionalities. Tools like IDA Pro or Radare2 are often used for binary patching.
- Automating Penetration Testing: As we dig deeper into Android penetration testing, the complexity of tests increases. Automation can be a real lifesaver here. Tools like MobSF (Mobile Security Framework) can automate many of the tasks, making our job much easier.
These advanced techniques can help us uncover significant vulnerabilities, but they should be used ethically and responsibly. And as always, the goal is not just to find vulnerabilities but also to find ways to patch them and enhance the application’s security.
Mobile Malware and Rootkit Analysis
When we talk about mobile malware and rootkits, we’re diving into the tactics that malicious actors use to exploit vulnerabilities. Think of malware and rootkits as the tricks up a hacker’s sleeve. By understanding these tricks, we can better defend against them. So, let’s dig in.
- Mobile Malware Analysis: Mobile malware is malicious software designed to target mobile devices. These can include viruses, Trojans, ransomware, and spyware, each with its own way of wreaking havoc. Our job? To dissect these pieces of malware, understand how they work, and identify signatures that can help us detect their presence. We’ll use tools like JADX or APKTool for reverse engineering and VirusTotal for malware detection.
- Static and Dynamic Analysis: We analyze malware in two ways. Static analysis involves studying the malware’s code without actually executing it. It’s like examining a locked box from the outside. On the other hand, dynamic analysis requires us to run the malware in a controlled environment and observe its behavior. It’s akin to unlocking the box and watching the mechanisms at work. Both these techniques give us valuable insights into the malware’s functionalities and potential damage.
- Rootkit Analysis: Rootkits are a type of stealthy malware that hide their presence or the presence of other software. They usually operate at a deep system level, making detection quite challenging. Analyzing rootkits involves similar techniques as malware analysis, but with an extra layer of stealth to cut through. Tools like GMER or Radare2 can be useful in our rootkit analysis.
- Mitigation Strategies: Understanding malware and rootkits is just half the battle. We also need to devise strategies to protect against these threats. This involves patching identified vulnerabilities, setting up robust detection systems, and maintaining up-to-date security practices.
In the realm of Android penetration testing, exploring mobile malware and rootkits equips us with valuable knowledge. It’s like learning the opponent’s moves in a chess game. This insight helps us fortify our defenses and anticipate potential attacks.
Conclusion
Well, my fellow digital explorers, we’ve navigated the vast landscape of Android penetration testing together. From understanding the basics of Android architecture to advanced penetration techniques and diving deep into the world of mobile malware and rootkits, we’ve covered some serious ground.
In the end, our goal is not just to uncover vulnerabilities but also to find ways to patch them, making our apps safer and more reliable. Remember, Android penetration testing isn’t about breaking things for the sake of it. It’s about building stronger, more secure systems that can withstand the myriad of cyber threats that lurk in the shadows of the digital realm.
But our journey doesn’t end here. In the field of cybersecurity, the learning never stops. New challenges arise, technology evolves, and we must continually adapt and upgrade our skills to keep pace. Thankfully, we’re not alone. With platforms like Codelivly offering resources and training, we can continue to learn, grow, and stay at the forefront of the cybersecurity world.
I hope this guide has been a valuable resource in your Android penetration testing journey. May it serve as a launchpad for you to delve even deeper into the fascinating world of cybersecurity. Remember, with every vulnerability you discover and every security loophole you fix, you’re making the digital world a safer place for everyone.
Frequently Asked Questions (FAQs)
1. What is Android Penetration Testing?
Android penetration testing is the process of analyzing and testing an Android application’s security setup to identify any vulnerabilities or weaknesses that could be exploited by a hacker. The ultimate goal is to patch these vulnerabilities and enhance the app’s security.
2. Do I need to know how to code for Android Penetration Testing?
While you don’t need to be a master coder, a basic understanding of coding concepts and languages, such as Java and Kotlin (used in Android development), can be highly beneficial. Knowing how to code will help you understand the app’s structure better and make it easier to identify potential security flaws.
3. Is Android Penetration Testing legal?
Yes, Android penetration testing is legal as long as it’s done ethically and with permission. It’s performed by ethical hackers or security professionals to enhance the app’s security. Unauthorized hacking, however, is illegal and can lead to serious consequences.
4. What tools are used in Android Penetration Testing?
Various tools like Metasploit, Burp Suite, Wireshark, ADB, JADX, APKTool, and others are commonly used in Android penetration testing. Each tool serves a specific purpose, from network analysis to reverse engineering and malware analysis.
5. Where can I learn more about Android Penetration Testing?
There are numerous online platforms to learn about Android penetration testing. Codelivly, for instance, offers comprehensive resources and training in the field of cybersecurity. Other platforms include Coursera, Udemy, and EdX. Additionally, there are many books, blogs, and forums dedicated to cybersecurity.
Found this article interesting? Follow us on Twitter and Telegram to read more exclusive content we post.
1 Comment
Thank you for your well detailed article on android penetration testing. I look forward to reading more of your articles and would be pleased to join a team and likewise be a contributor to this ever growing field of Cyber security.