If you’ve ever dived into the world of computer security, you know that it’s an ever-changing landscape filled with twists and turns. In our last exciting exploration, we talked all about “Ports and Protocols: An In-Depth Exploration for Ethical Hacking in Networking.” It was quite the ride, wasn’t it?
Well, strap in, because this time we’re taking on something that sounds like it could be straight out of a spy movie: Zero-Day Vulnerabilities. That’s right, those elusive, unpredictable, and sometimes downright scary security flaws that hackers can exploit before anyone even knows they exist.
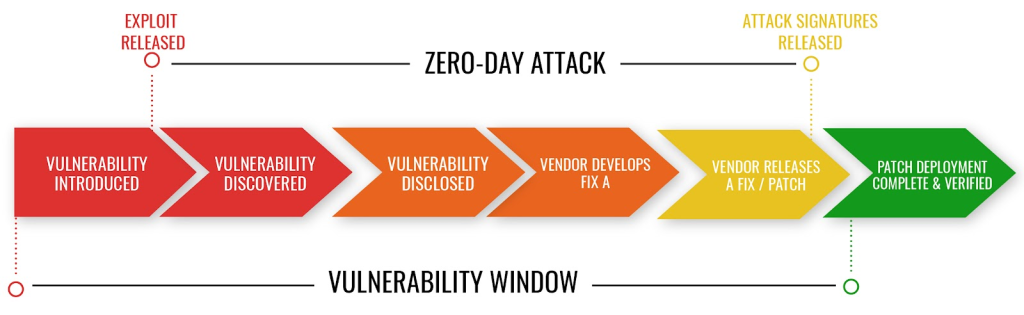
What’s a zero-day vulnerability, you ask? It’s like a secret backdoor left unlocked, just waiting for someone to find it. Only in this case, there’s no time to fix the lock. Once discovered, it can be used immediately, leaving no time to patch things up. That’s why it’s called a “zero-day.”
But don’t worry, we’ll cover all the bases, from what it is to how you can protect yourself and everything in between. And if you’re feeling a bit lost, you might want to check out our previous article to get up to speed on some essential background knowledge.
So grab a cup of coffee, get comfortable, and let’s dive into the intriguing world of zero-day vulnerabilities. Trust me; it’s going to be an adventure!
History and Notable Cases
Alright, history time! But don’t worry, this isn’t your run-of-the-mill, snooze-fest history lesson. We’re talking about the wild world of zero-day vulnerabilities, and trust me, it’s anything but boring.
So, what’s the deal with these hidden flaws, and why do they even exist? Well, back in the early days of computing, software was kind of like the Wild West. Things were new, exciting, and a little bit chaotic. Programmers were making groundbreaking stuff, but sometimes they left a few loose ends.
These loose ends, or vulnerabilities, were just waiting to be discovered. And when they were? Boom! A zero-day exploit was born.
Remember the Morris Worm in 1988? That was one of the first instances where a vulnerability was exploited, and it caused quite a stir, shutting down a big chunk of the internet.
And who could forget Stuxnet? This worm, discovered in 2010, targeted Iranian nuclear facilities and was like something out of a spy novel. It exploited not one, but four zero-day vulnerabilities. Talk about sophistication!
But it’s not all cloak-and-dagger stuff. Even everyday software like your web browser can have zero-day vulnerabilities. Remember that time in 2018 when a Google Chrome flaw was exploited? Yeah, it sent shockwaves through the tech community.
What’s the takeaway from all this? Zero-day vulnerabilities have been around for a while, and they’ve played a starring role in some of the most notorious cyber events in history. It’s like a never-ending game of cat and mouse between the good guys and the bad guys.
Cool stuff, right? Now, let’s move on and see how these hidden flaws are found and what can be done about them. It’s going to be a wild ride!
How Zero-Day Vulnerabilities are Discovered
Imagine software as a huge maze. Some paths are well-trodden and super safe, while others, well… they’re a bit sketchy. Finding a Zero-Day Vulnerability is like discovering a hidden tunnel in that maze, a shortcut that nobody even knew was there.
Now, a bunch of smart folks dedicate their lives to exploring these mazes. They’re like digital explorers. Some are “white hat hackers” – the good guys who look for vulnerabilities to help patch them up. They use various tools, techniques, and a lot of coffee to scour software for any weak points. When they find a Zero-Day Vulnerability, they usually report it to the software’s creators, often through what’s called a “bug bounty program.” It’s like a treasure hunt where the prize is cash and, of course, bragging rights.
But there’s also another side to this. Automated software scanning tools can tirelessly check vast amounts of code, highlighting potential vulnerabilities. Think of these tools as robots that tirelessly wander the maze, always searching.
However, not everyone has noble intentions. Some discover these vulnerabilities to exploit them for malicious purposes. The digital realm has its share of treasure hunters and pirates, after all.
Who are the targets for zero-day exploits?
Ah, great question! Zero-Day exploits are like digital weapons, and just like any weapon, they’re wielded against specific targets for various reasons. Let’s break down who’s often in the crosshairs:
- Large Corporations and Businesses: Big companies are often lucrative targets. Why? Well, they’ve got a lot to lose. Cyber attackers can exploit vulnerabilities to steal sensitive data, intellectual property, or even cause disruptions that can result in financial losses.
- Governments and Military Organizations: Espionage isn’t just for James Bond movies! Nation-states might use Zero-Day exploits for cyber espionage, targeting another country’s government or military systems. The aim could be intelligence gathering, disruption, or even sabotage.
- Utility and Infrastructure Providers: Think electricity grids, water utilities, and transportation networks. These are crucial services, and disrupting them can have major real-world consequences.
- Individuals with High Net Worth or Political Influence: Prominent individuals, like celebrities or politicians, might be targeted for personal, financial, or even politically motivated reasons.
- Financial Institutions: Banks and other financial entities are obvious targets, given the potential monetary gains from a successful exploit.
- Research Institutions and Universities: Sometimes, it’s not about money but knowledge. Research institutions often have valuable data, studies, and breakthrough information.
- Healthcare Institutions: Besides having valuable patient data (which can be used for identity theft), healthcare institutions might be targeted for other reasons, like ransomware attacks, given the critical nature of their services.
- General Public: Sometimes, it’s just about casting a wide net. Malware that exploits Zero-Day vulnerabilities can spread rapidly and indiscriminately, affecting everyday users.
The value of a Zero-Day exploit often lies in its secrecy. Once it’s used widely and detected, its days are numbered as developers race to patch the vulnerability. So attackers choose their targets wisely, aiming for maximum impact or gain.
Exploitation of Zero-Day Vulnerabilities
Okay, so we’ve chatted about how these sneaky Zero-Day Vulnerabilities are discovered, right? Now, let’s venture into the more dramatic side of things – the exploitation! Picture this: our digital world as a bustling city, and hidden alleys (or vulnerabilities) are being discovered all the time. Not everyone stumbling onto these alleys has the best intentions.
When someone figures out how to use a Zero-Day Vulnerability to their advantage, it’s kind of like they’ve found a secret entrance into a bank vault without the bank even knowing it exists. Sounds thrilling? Well, it’s not so great for the rest of us!
There’s this underground market, almost like a digital black market, where these vulnerabilities are sold to the highest bidder. That’s right, there are folks out there willing to pay big bucks to get their hands on a freshly discovered Zero-Day Vulnerability. Sometimes, these buyers are individual hackers, other times, they’re organized crime rings, or even, dare I say, nation-states looking for a cyber edge.
Ever heard of cyber espionage? Think James Bond, but with more keyboards and fewer martinis. Some governments allegedly hoard these vulnerabilities to use against their adversaries. It’s a world of digital spy games, and Zero-Day Vulnerabilities are some of the most prized assets.
But not all exploits are about global politics. Some hackers just want to make a quick buck. By leveraging a Zero-Day Vulnerability, they can steal personal data, credit card info, or even hold systems for ransom.
Impacts of Zero-Day Attacks
So, we’ve danced around the discovery and exploitation of Zero-Day Vulnerabilities, but what happens when things go south? When someone decides to throw a digital wrench in the system using a Zero-Day Vulnerability?
First up: the economic aftermath. Imagine waking up, sipping your morning coffee, and finding out your favorite online store just got hacked. Now, they’re not just losing your trust (and possibly your business); they’re shelling out big bucks for damage control. Repairing systems, compensating affected users, and ramping up security measures – it’s like fixing a dam while water’s pouring out. Companies can face losses in millions, and that’s no pocket change!
But it’s not just about the moolah. The security and privacy implications are massive. Personal data? Exposed. Sensitive company info? Leaked. Suddenly, that Zero-Day Vulnerability isn’t just a geeky term; it’s a real threat to people’s lives. Identity theft, fraud, and a whole host of cybercrimes can trace their roots back to these vulnerabilities.
And then, there’s the societal impact. Remember when a certain Zero-Day Vulnerability led to a major utility shutdown? Or when hospitals faced disruptions due to a cyberattack? Real people, real consequences. It’s like a domino effect; one piece falls, and the whole line goes down.
I know, I know, it sounds pretty grim. But being aware of the reach and ripple effect of exploiting a Zero-Day Vulnerability is crucial. It underscores just how intertwined our digital and physical worlds are.
Examples of zero-day attacks
Absolutely, zero-day attacks have been behind some of the most notorious and impactful cybersecurity incidents over the years. Let’s delve into a few notable examples:
- Stuxnet: Arguably one of the most famous zero-day attacks, Stuxnet was a sophisticated worm discovered in 2010. It targeted Iran’s nuclear facilities, specifically their centrifuges. The worm exploited not one, but four zero-day vulnerabilities in Windows. It’s believed that Stuxnet set back Iran’s nuclear program by several years.
- WannaCry: In 2017, the WannaCry ransomware attack wreaked havoc globally, affecting over 230,000 computers across 150 countries. This ransomware exploited a Microsoft Windows zero-day vulnerability known as “EternalBlue”, which had been leaked from the U.S. National Security Agency (NSA).
- Heartbleed: While not a traditional zero-day, Heartbleed was a severe vulnerability discovered in 2014 in the OpenSSL cryptographic software library. It allowed attackers to read memory in affected systems, potentially accessing sensitive data, including private keys for SSL/TLS.
- Petya and NotPetya: These are ransomware strains that surfaced around 2016 and 2017. NotPetya, particularly, was devastating, spreading rapidly using the same EternalBlue exploit that WannaCry used. Major global companies were affected, leading to hundreds of millions of dollars in losses.
- Operation Aurora: In 2010, a coordinated attack named “Operation Aurora” targeted multiple high-profile companies, including Google. The attackers exploited a zero-day vulnerability in Internet Explorer. The primary goal seemed to be to access accounts of human rights activists.
- Shellshock: Discovered in 2014, this vulnerability affected the Unix Bash shell, allowing attackers to execute arbitrary commands on targeted systems. Given its wide reach, this vulnerability had a severe impact rating.
- Jailbreaks: On a different note, some iOS jailbreaks have leveraged zero-day vulnerabilities to provide users with unauthorized access to their device’s operating system.
These examples underscore the importance and potential impact of zero-day vulnerabilities. They can be leveraged for espionage, financial gain, or sometimes simply to cause chaos. They also highlight the crucial role of timely patches and proactive cybersecurity measures in preventing such breaches.
Defending Against Zero-Day Attacks
Okay, so the world of Zero-Day Vulnerabilities might sound like a digital minefield, but it’s not all doom and gloom. I promise! There are some real superhero moves we can pull to fend off these attacks, and I’m here to spill the secrets.
- Patch, Patch, Patch! You know those annoying software updates that always seem to pop up when you’re in the middle of something important? Yeah, those are golden. Developers are constantly working to patch known vulnerabilities. So, when an update rolls in, grab it. Think of it like upgrading your digital armor.
- Stay Alert with Intrusion Detection Systems (IDS) These are like the digital watchtowers of your network. They’re always on the lookout for suspicious activity, including signs of a Zero-Day Vulnerability being exploited. If they spot something fishy, they’ll sound the alarms.
- Get Ahead with Threat Intelligence Imagine having a crystal ball that could give you insights into potential threats. That’s what advanced threat intelligence does! It keeps an ear to the ground, catching whispers about potential vulnerabilities and helping you prepare.
- Regular System Backups It’s like having a time machine. If things go south and a Zero-Day Vulnerability wreaks havoc, having recent backups means you can roll back the clock and restore your systems.
- Employee Education Remember, we’re all in this together! Hosting regular cybersecurity training sessions can turn everyone in your organization into a cyber-sentry. The more eyes on the lookout, the better.
So there you have it! While the world of Zero-Day Vulnerabilities can seem daunting, with the right tools and a vigilant mindset, we can give those cyber attackers a run for their money.
Conclusion
So, what’s the big takeaway from our dive into Zero-Day Vulnerabilities? Well, it’s this: Our digital world is a dynamic, constantly shifting landscape. Zero-Day Vulnerabilities are like hidden trapdoors that can be stumbled upon by anyone from well-intentioned researchers to crafty cybercriminals.
We’ve explored the ins and outs of these vulnerabilities, from their discovery and exploitation to the defenses we can mount against them. We’ve seen the real-world impacts, the targets, and some historical examples that remind us just how powerful these hidden weaknesses can be.
But remember, it’s not all digital doom and gloom! As quickly as new vulnerabilities appear, there’s a legion of cybersecurity heroes working tirelessly to patch, protect, and defend. Whether it’s companies bolstering their defenses or everyday users simply keeping their software up to date, we all have a part to play.
Zero-Day Vulnerabilities might sound like something out of a science fiction thriller, but they’re a very real aspect of our interconnected world. They remind us that vigilance, awareness, and a proactive approach are key to navigating our digital lives.
Stay safe out there, dear reader. Keep those systems patched, stay aware, and remember, the digital realm is an ever-changing adventure, full of both challenges and opportunities. Here’s to staying one step ahead! 🌐
P.S. Want to keep exploring the world of cybersecurity? You might enjoy our previous article on “Ports and Protocols: An In-Depth Exploration for Ethical Hacking in Networking.” Happy reading!
FAQ
1. What Is a Zero-Day Vulnerability?
A Zero-Day Vulnerability is a flaw or weakness in software, hardware, or firmware that’s unknown to those who would be interested in fixing it. Since the vulnerability is not known, there’s no official fix or patch for it, making it a ripe target for exploitation.
2. How Are Zero-Day Vulnerabilities Discovered?
They can be discovered by researchers, hackers, or even accidental users. Sometimes they’re found through meticulous analysis and testing, and other times, they’re stumbled upon by chance.
3. Who Are the Typical Targets for Zero-Day Exploits?
Targets can range from large corporations, governments, and military organizations to financial institutions, healthcare providers, and even individual users.
4. How Can I Protect Myself Against Zero-Day Attacks?
Regular software updates, using intrusion detection systems, regular system backups, and being vigilant about cybersecurity can help. Educating yourself and your team about potential threats is also key.
5. Are Zero-Day Attacks Common?
While not extremely common, Zero-Day attacks do occur and can have significant impacts. They are highly prized by attackers since there’s no immediate defense against them.
6. What Happens Once a Zero-Day Vulnerability Is Discovered?
Once a responsible party discovers it, they often notify the software provider discreetly. The provider then works on a patch or fix to close the vulnerability. Sometimes, though, vulnerabilities are sold or exploited before they are patched.
7. Can Zero-Day Vulnerabilities Be Prevented?
It’s nearly impossible to prevent all Zero-Day Vulnerabilities since new software can always contain unforeseen flaws. However, using secure coding practices and thorough testing can minimize risks.
8. What Are Some Famous Examples of Zero-Day Attacks?
Examples include the Stuxnet worm, WannaCry ransomware, Heartbleed vulnerability in OpenSSL, and Operation Aurora.
9. Is It Legal to Sell or Buy Information About Zero-Day Vulnerabilities?
This is a complex area. While there are legitimate markets for buying and selling vulnerabilities for research and defense purposes, there’s also a black market where such information is traded for malicious purposes.
10. Why Are They Called “Zero-Day” Vulnerabilities?
The term “Zero-Day” refers to the fact that developers have “zero days” to fix the problem once the vulnerability becomes known to the public or an attacker.
These answers hopefully shed more light on the fascinating and sometimes alarming world of Zero-Day Vulnerabilities. Stay curious and stay safe!

2 Comments
hello
nice try