If you’ve clicked on this article, you’re probably curious about the mysterious world of web application hacking, particularly when it comes to file upload attacks. Well, you’re in for a treat. Let’s dive in, shall we?
Web applications have become a vital part of our daily lives. I mean, think about it – from posting our favorite snaps on social media to managing our bank accounts, we use them all the time. But here’s the thing: while these applications provide us with a ton of convenience, they also come with their share of vulnerabilities. One of the most overlooked, yet potentially harmful, vulnerabilities revolves around file uploads.
Now, I get it. Uploading a file might seem like a pretty straightforward process. You click a button, choose your file, and bam, it’s uploaded. But behind the scenes, there’s a lot more going on. If not handled securely, this simple act of uploading a file can open the door to some pretty nasty attacks.
In this article, we’ll unravel the complexities of file upload attacks. From understanding the common vulnerabilities to diving deep into real-world examples, I promise it’s going to be an enlightening journey. So, grab your favorite beverage, get comfy, and let’s get started!
What Is File Upload Vulnerability?
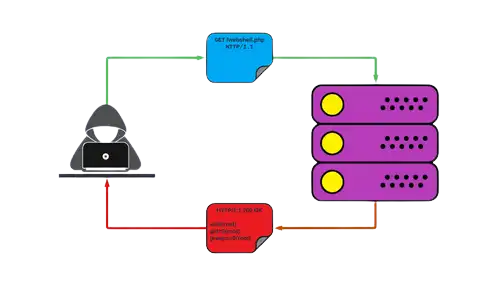
File Upload Vulnerability refers to a type of security flaw in a web application that allows an attacker to upload and execute malicious files on the server. This vulnerability arises when a web application permits users to upload files without implementing sufficient security controls to validate or sanitize the uploaded content.
When exploited, file upload vulnerabilities can provide attackers with a foothold on the server, leading to a variety of potential malicious activities, such as:
- Executing Malicious Code: By uploading files that contain harmful scripts or executables, attackers can run arbitrary code on the server, potentially taking full control of it.
- Hosting Malware or Phishing Pages: Attackers might use the compromised server to host malicious content, turning it into a distribution point for malware or a platform for phishing schemes.
- Data Theft or Manipulation: Once an attacker gains access to the server, they can potentially access, modify, or exfiltrate sensitive data.
- Denial of Service (DoS): Attackers could upload large files or numerous files in quick succession to overwhelm server resources, leading to service disruptions due to Ddos attacks.
- Privilege Escalation: In cases where improper permissions are set, an attacker might be able to escalate their privileges on the server, giving them even more control.
The root cause of file upload vulnerabilities often lies in inadequate validation and sanitization of the uploaded files. For example:
- Allowing any file type to be uploaded without restrictions.
- Failing to scan uploaded files for malware or malicious content.
- Storing uploaded files in web-accessible directories, making them easily accessible via URLs.
- Relying solely on client-side validation, which can be easily bypassed.
To mitigate file upload vulnerabilities, it’s essential to implement strict validation rules, use both client-side and server-side checks, scan all uploaded content for threats, and ensure proper server configurations and permissions.
How do file upload vulnerabilities arise?
File upload vulnerabilities arise due to a combination of factors related to design, development, configuration, and oversight. When web applications allow users to upload files without proper safeguards, they open the door to potential exploits. Here’s a breakdown of how these vulnerabilities come into existence:
- Lack of Input Validation:
- Not validating the type, size, content, or name of uploaded files.
- Relying solely on client-side validation, which can be easily bypassed or modified.
- Only checking file extensions or MIME types without delving deeper into the actual content of the file.
- Improper Configuration:
- Storing uploaded files in web-accessible directories, making them easily accessible via URLs.
- Configuring servers to execute files from upload directories, allowing potential malicious scripts to run.
- Not setting proper file and directory permissions, which can grant attackers more access than intended.
- Inadequate Security Measures:
- Failing to implement or regularly update antivirus and malware scanning for uploaded files.
- Not using isolation or sandboxing techniques to handle and process uploaded files.
- Lack of Rate Limiting:
- Allowing users to upload an unlimited number of files in rapid succession, which can lead to DoS attacks or give attackers more opportunities to find a vulnerability.
- Overlooking Security in Design:
- Not considering security implications during the design phase of the application.
- Prioritizing user convenience or functionality over security.
- Incomplete or Outdated Documentation:
- Using third-party libraries, plugins, or modules for file uploads without fully understanding their security implications or configurations.
- Not staying updated with security advisories or patches for the tools in use.
- Insufficient Testing:
- Not conducting thorough security testing, including penetration testing, to identify potential vulnerabilities.
- Overlooking edge cases or not using a diverse range of test scenarios.
- Human Factor:
- Developers or administrators might make mistakes or overlook certain security aspects.
- A lack of continuous training or awareness about the latest threats and best practices.
- Not Keeping Up with Threat Landscape:
- The world of cybersecurity is ever-evolving. New vulnerabilities and attack vectors emerge regularly. Failing to stay informed and adapt can lead to new, unanticipated vulnerabilities.
In essence, file upload vulnerabilities arise due to a mix of technical oversights, human error, and the ever-adaptive nature of cyber threats. Proper design, development practices, regular updates, and continuous security assessments are vital in minimizing these vulnerabilities.
Common Vulnerabilities in File Upload Mechanisms

Alright, let’s get down to the nitty-gritty. When we talk about file uploads, it might seem like a pretty benign action, right? I mean, how could uploading a cute cat photo or a PDF document be harmful? But here’s the catch: it’s not always about what you’re uploading, but how the web application processes and stores it. If there’s a chink in the armor, attackers won’t hesitate to exploit it. Let’s delve into some of the most common vulnerabilities in file upload mechanisms:
#1. Inadequate File Type Validation
Let’s chat about a vulnerability that might seem simple on the surface but can pack quite a punch if overlooked: inadequate file type validation. You see, just like you wouldn’t want someone to bring a wild animal into your home (I’m looking at you, tiger enthusiasts!), web applications shouldn’t allow just any file type to be uploaded without thorough checks. So, why is this so important? And how can things go wrong? Let’s dive in.
Why File Type Validation Matters:
- Security: Some file types can execute code. For instance, while a
.jpgimage file is relatively safe, a.phpor.jsfile can run scripts that could potentially harm the server or the end-users. - Functionality: Let’s say you have a photo-sharing platform. If users start uploading Word documents, it won’t exactly fit the bill, right?
Common Mistakes in File Type Validation:
- Just Checking the File Extension: If an app is merely looking at the “.jpg” or “.png” at the end of a filename, we’ve got a problem. I could easily rename a malicious
.phpfile tocute-cat.jpg.phpand try to trick the system. Just because it has “.jpg” in the name doesn’t make it an image! - Relying Solely on MIME Types: MIME (Multipurpose Internet Mail Extensions) types tell browsers how to handle specific file types. But guess what? They can be faked. If a web app is only checking the MIME type sent by the browser, it’s setting itself up for potential trouble.
- Trusting User Input: If there’s one rule in cybersecurity, it’s “Never trust user input blindly.” If a file upload system trusts the metadata provided by the user without verification, it’s like trusting a stranger with your house keys. Not wise, my friend.
Consequences of Inadequate Validation:
- Malicious Code Execution: Attackers could upload files that run harmful scripts, leading to website defacement, data theft, or even taking over the server.
- System Misbehavior: Uploading incorrect file types can lead to application crashes or unintended behavior. It’s like trying to play a DVD in a toaster; it’s just not built for that.
Mitigation Strategies:
- Whitelist, Don’t Blacklist: Instead of trying to block known harmful file types (blacklisting), allow only specific, safe file types (whitelisting). It’s a proactive approach.
- Server-side Verification: Always verify the file type on the server-side, not just based on what the browser says. Think of it as double-checking a guest’s invitation before letting them into a party.
- Use Multiple Validation Methods: Combine file extension checks, MIME type verification, and file content inspection for a more robust validation process.
#2. Lack of File Size Restrictions
Ever been to one of those buffets where there’s no limit on how much you can pile onto your plate? Sounds great, right? But what happens if everyone starts hoarding, and the kitchen runs out of food? Similarly, in the world of web applications, not having file size restrictions can lead to all sorts of chaos. So, grab a (virtual) seat, and let’s chat about why size definitely matters when it comes to file uploads.
Why Bother with File Size Restrictions?
- Performance: Larger files require more processing power and memory. If everyone started uploading massive files, it would slow down the server, affecting everyone’s experience.
- Storage Concerns: Servers aren’t bottomless pits. They have limited storage. Without restrictions, they can quickly get filled up, causing operational issues.
- Bandwidth: Transferring large files consumes more bandwidth. This could lead to increased costs for the host and slower download/upload speeds for users.
Potential Risks of Oversized File Uploads:
- Denial of Service (DoS): If attackers continuously upload gigantic files, they could exhaust server resources, making the application slow or entirely unresponsive. It’s like a traffic jam on the internet highway.
- Exploiting Memory Vulnerabilities: Large files could potentially exploit buffer overflow vulnerabilities, leading to malicious code execution or system crashes.
- Disrupting Application Functionality: If an application is not designed to handle or display large files, it could behave unpredictably or even crash.
Preventing the Oversize Chaos:
- Set Clear Limits: Clearly define the maximum file size for uploads. Whether it’s images, videos, or documents, having a predefined size limit can prevent many issues down the line.
- Client-side Checks: While they shouldn’t be the only line of defense, client-side checks can provide immediate feedback to users, letting them know if their file is too big before they even hit the upload button.
- Server-side Validation: Always, and I mean always, verify the file size on the server-side. This is your main gatekeeper to prevent oversized files from causing havoc.
- Monitor and Alert: Set up monitoring tools to alert administrators if there’s a sudden surge in large file uploads or if storage starts running low. It’s always good to be in the know!
#3. Improper File Handling and Storage
Alright, friends, let’s get into a topic that’s often overlooked but can lead to some serious headaches if not addressed: improper file handling and storage. Picture this: you’ve got a secret stash of chocolates, and instead of hiding it in a safe spot, you leave it on the kitchen counter. What do you think happens next? Chaos, right? Similarly, how web applications handle and store uploaded files can make all the difference between a secure environment and a hacker’s playground.
Why Proper File Handling and Storage is Crucial:
- Data Integrity: Ensuring that uploaded files remain unchanged and are retrievable in their original form is paramount.
- Privacy and Security: Some uploaded files may contain sensitive information. If they’re not stored securely, it could lead to data breaches.
Common Slip-Ups in File Handling and Storage:
- Storing Files in Web-Accessible Directories: If uploaded files are stored in directories that are directly accessible via the web, it’s like leaving your diary out in the open. Anyone can read (or misuse) it.
- Not Changing File Names: Using the original file names provided by users can lead to unintentional overwrites or even give clues to attackers about the file’s content or purpose.
- No Encryption: Storing sensitive files without encryption is like locking your house but leaving the key under the doormat. Anyone with a little know-how can access them.
- Lack of Proper Permissions: If every user or process on the server has permissions to read, write, or execute uploaded files, it’s a disaster waiting to happen.
The Fallout from Improper Handling:
- Data Leaks: Files containing personal or sensitive data could be accessed by unauthorized individuals.
- Malicious File Execution: If an attacker can upload a malicious file and knows where it’s stored, they might be able to execute it, compromising the server or harming users.
- Loss of Data: Improper handling can lead to unintentional file deletions or overwrites.
Tips for Proper File Handling and Storage:
- Use Randomized File Names: Rename files upon upload using a unique or randomized naming convention. This can prevent overwrites and make it harder for attackers to guess file paths.
- Store Outside the Web Root: Store uploaded files outside the publicly accessible web directory. This way, even if someone knows the file name, they can’t directly access it via a URL.
- Implement Encryption: For sensitive files, encryption is a must. This ensures that even if files are accessed, they can’t be read without the decryption key.
- Set Strict Permissions: Limit who can read, write, or execute files. Be stingy with granting permissions; it’s better to be safe than sorry.
#4. No Content Scanning
Imagine walking into an exclusive party without anyone checking your invitation, or worse, airport security letting passengers through without scanning their bags. Sounds risky, right? That’s precisely the situation when web applications allow file uploads without scanning their content. Let’s dive into why skipping this step is like inviting trouble to waltz right in.
The Importance of Content Scanning:
- Detect Malware: Not all files are what they appear to be. What seems like an innocent PDF or image might harbor malicious code waiting to spring into action.
- Prevent Data Loss: Scanning can help detect attempts to exfiltrate sensitive data hidden inside files.
The Perils of Skipping the Scan:
- Hidden Threats: Malware, viruses, and trojans can hide within seemingly benign files. Without scanning, these threats can enter systems undetected, like a wolf in sheep’s clothing.
- Phishing and Social Engineering: Attackers can embed malicious links or misleading information within documents, leading users down a dangerous path.
- Zero-Day Exploits: These are previously unknown vulnerabilities. Without continuous content scanning using updated threat databases, new threats can bypass defenses.
The Real-World Consequences:
- System Compromise: Malicious files can lead to system takeovers, giving attackers a foothold within the network.
- Data Breaches: Malware can exfiltrate sensitive data, leading to financial losses and reputational damage.
- Operational Disruption: Some malware aims to disrupt services, leading to downtimes and loss of business.
How to Ensure Proper Content Scanning:
- Integrate Antivirus Scanning: Use reputable antivirus solutions to scan every uploaded file. Make sure it’s set to update its definitions regularly.
- Deep Content Inspection: Go beyond surface-level scanning. Deep content inspection analyzes the actual content of a file to ensure it matches its declared type and doesn’t contain hidden threats.
- Use Heuristics: Instead of just looking for known malware signatures, heuristic analysis checks for suspicious behaviors or patterns, helping detect new or modified threats.
- Regular Updates: Threat landscapes evolve rapidly. Ensure that your scanning tools and their databases are frequently updated to catch the latest threats.
- Feedback Loop: Inform users if their uploaded files are flagged. This not only prevents potentially harmful uploads but also educates users about safe practices.
#5. Over-reliance on Client-side Validation
Alright, let’s tackle a topic that’s a bit like believing everything you read on the internet: over-reliance on client-side validation. Now, I’m not saying client-side validation is all bad. It’s like that friend who gives you a heads-up before you do something silly. But if that’s the only line of defense you’re relying on for file uploads, then, my friend, we’re in for some stormy weather. Let’s delve deeper into this.
The Allure of Client-side Validation:
- Instant Feedback: One of the best things about client-side validation is the immediate feedback it provides to users. No need to wait for server responses; if something’s amiss, users know right away.
- Reduced Server Load: By catching common mistakes on the client side, servers have less erroneous data to process, making them more efficient.
But Here’s Where Things Get Tricky:
- Easily Bypassed: Client-side validation usually relies on JavaScript running in the user’s browser. With a few tweaks or using browser developer tools, this validation can be disabled or modified. It’s like having a security system but leaving the control panel in plain sight.
- False Sense of Security: Over-relying on client-side checks can lead developers to become complacent, thinking they’ve got all their bases covered. This can lead to vulnerabilities being overlooked.
- Inconsistent User Environments: Different browsers, devices, or even browser versions can interpret client-side validation differently, leading to unpredictable results.
Potential Pitfalls of Skipping Server-side Checks:
- Malicious Data Entry: Without server-side validation, attackers can send harmful data or files directly to the server, bypassing any client-side checks.
- Data Corruption: If incorrect or unexpected data makes its way past client-side validation, it could lead to data corruption or application errors.
- Security Vulnerabilities: Many security vulnerabilities, like SQL injection or cross-site scripting, arise from not validating or sanitizing user input on the server side.
Balancing the Scales:
- Use Both: Think of client-side validation as the first checkpoint and server-side validation as the final, more thorough inspection. Both have their roles to play.
- Sanitize and Validate: On the server side, always sanitize and validate input, ensuring it’s free from malicious content and meets expected formats.
- Stay Updated: Threats evolve, and so should validation methods. Regularly review and update validation rules on both the client and server sides.
#6. Missing Rate Limiting on Uploads
Imagine going to your favorite ice cream parlor, and they tell you there’s no limit to the number of scoops you can have. Sounds like a dream, doesn’t it? But let’s face it, too much of a good thing can be… well, not so good. Similarly, in the digital realm, not having rate limiting on file uploads can turn a web application’s sweet user experience into a sticky mess. Let’s churn through this topic, shall we?
Why Rate Limiting is a Big Deal:
- Resource Management: Every uploaded file consumes server resources, both in terms of storage and processing. A flood of uploads can quickly exhaust these resources.
- Preventing Abuse: Without rate limits, malicious actors can flood the server with uploads, either to crash it or to find vulnerabilities.
Dangers of the Unlimited Upload Highway:
- Denial of Service (DoS): By bombarding the server with rapid or large file uploads, attackers can overload its capacity, causing slowdowns or complete unavailability.
- Brute Force Attacks: Without rate limiting, attackers can repeatedly upload files to find vulnerabilities or bypass security measures.
- Increased Costs: More uploads mean more data transfer and storage, potentially leading to higher operational costs.
Real-World Impact:
- Service Interruption: A successful DoS attack can disrupt service, affecting all users and potentially leading to loss of business or reputation.
- Data Breaches: Rapid, unchecked uploads can be a vector for injecting malicious files, leading to potential data breaches or system compromises.
Strategies to Implement Rate Limiting:
- Per-User Limits: Set a maximum number of uploads allowed per user within a specific timeframe. This ensures no single user can overwhelm the system.
- Size Restrictions: Apart from the total number of uploads, also limit the cumulative size of uploaded files within a given period.
- IP-based Rate Limiting: If a surge of uploads is coming from a single IP address, it could be a sign of malicious activity. Setting IP-based limits can help curb this.
- Feedback Mechanism: Inform users when they’re approaching or have exceeded their upload limits. This not only prevents unexpected rejections but also educates users about fair usage.
- Dynamic Adjustments: In times of high traffic or potential threats, dynamically adjust rate limits to ensure the system remains stable and secure.
Potential Impact of File Upload Attacks

Stepping into the world of web application security, it’s essential to understand not just the vulnerabilities but also the potential fallout if they’re exploited. Think of file upload attacks as the proverbial Trojan horse: they might seem harmless on the surface, but the damage they can unleash is immense. Let’s unpack the potential impacts of these sneaky attacks.
Why Worry About File Upload Attacks?
- Wide Access: File upload features are common in web applications, from profile picture updates on social media to document submissions on corporate platforms.
- Varied Attack Vectors: From simple image uploads to complex document management systems, the attack surface is broad and varied.
The Domino Effect of a Successful Attack:
- Remote Code Execution (RCE): One of the most severe impacts. If an attacker can upload and execute malicious scripts, they can potentially take control of the server. It’s like handing over the keys to your kingdom.
- System Takeover: Beyond just executing code, attackers might gain elevated privileges, giving them the power to modify, delete, or access sensitive data, or even take over the entire system.
- Data Theft or Manipulation: Once inside, malicious actors can steal user data, financial information, or intellectual property. Alternatively, they might alter data, causing chaos and misinformation.
- Malware Distribution: The compromised server can be used as a launchpad to distribute malware to users, spreading the infection further and wider.
- Website Defacement: A more visible impact. Attackers might change the website’s appearance or content, damaging the organization’s reputation.
- Distributed Denial of Service (DDoS): The server can be hijacked to become part of a botnet, launching DDoS attacks on other targets.
- Cryptojacking: Attackers might deploy scripts that use server resources to mine cryptocurrency, slowing down services and increasing operational costs.
Broader Implications:
- Reputational Damage: News of a breach can erode trust among users or clients. Rebuilding this trust can be time-consuming and costly.
- Financial Losses: From direct theft of funds to loss of business due to service interruptions, the monetary impact can be significant.
- Regulatory and Legal Consequences: Data breaches can lead to fines or legal actions, especially if personal data is compromised.
A Silver Lining:
Understanding the potential impacts isn’t meant to scare but to prepare. By being aware of the threats, organizations can better strategize their defenses and minimize risks.
In a nutshell, while file upload features offer immense convenience and functionality, they come with their set of risks. Being aware of the potential impacts of attacks is the first step in building robust defenses. So, as we journey deeper into the world of web security, let’s keep these implications in mind and strive for a safer, more secure digital landscape!
Defending Against File Upload Attacks
Alright, now that we’ve delved into the murky waters of file upload attacks and their potential impacts, it’s time to gear up and fortify our defenses. Think of it as building a digital fortress, with layers of walls, moats, and watchtowers to keep those pesky attackers at bay. Ready to get started? Let’s dive into the strategies and best practices to defend against file upload attacks.
The Cornerstones of a Strong Defense:
- Whitelisting Allowed File Types: It’s always better to define what’s allowed rather than trying to block all the bad stuff. Specify which file types users can upload and reject everything else. It’s like having a guest list for an exclusive party.
- Implement Strong File Naming Policies: Rename files upon upload using a unique or randomized naming convention. This prevents attackers from easily accessing or executing the files.
- Scanning Uploaded Files for Malware: Every file, without exception, should be scanned for malicious content. Think of it as a security checkpoint, ensuring no hidden threats get through.
- Using Isolation and Sandboxing Techniques: Store and process uploaded files in isolated environments. This way, even if a file turns out to be malicious, its potential to cause harm is limited.
- Setting Proper Permissions and File Handling Procedures: Be stingy with granting permissions. Not every process or user needs to access, modify, or execute uploaded files.
Additional Layers of Protection:
- Server-side Validation: Always validate file size, type, and content on the server side. Remember, client-side validation can be easily bypassed.
- Rate Limiting: Implement restrictions on the number and size of files a user can upload within a specific timeframe. This helps prevent flooding and potential DoS attacks.
- Use Content Delivery Networks (CDNs): CDNs can help offload the task of serving files, adding an additional layer of security and reducing the direct exposure of your primary server.
- Implement CAPTCHAs: While not foolproof, CAPTCHAs can deter automated file upload attacks, forcing attackers to manually submit files.
- Monitoring and Alerts: Keep an eye on file upload activities. Set up alerts for unusual behaviors, such as multiple failed upload attempts, large file sizes, or rapid succession uploads.
Educate and Inform:
- User Education: Inform users about safe file upload practices. Sometimes, the weakest link isn’t the technology but the people using it.
- Transparent Feedback: Provide clear feedback when a file is rejected. This not only helps users understand the issue but also reinforces trust in the platform’s security measures.
Regularly Update and Review:
Cyber threats are an ever-evolving landscape. Regularly review and update security measures, keeping abreast of the latest vulnerabilities and attack methods.
To wrap it up, defending against file upload attacks is like playing a high-stakes game of chess. It requires foresight, strategy, and continuous adaptation. By implementing robust defenses and staying vigilant, we can ensure that our web applications remain safe havens in the vast digital landscape. Let’s keep those digital drawbridges up and stay one step ahead of the attackers!
Tools and Techniques for Testing File Upload Security
Ensuring that your file upload features are secure requires a combination of tools and techniques. By employing the following, you can assess, identify, and mitigate potential vulnerabilities associated with file uploads:
1. Automated Vulnerability Scanners:
- OWASP ZAP (Zed Attack Proxy): An open-source security tool that helps find security vulnerabilities in web applications.
- Burp Suite: A popular tool for web security testing. Its Pro version includes automated scanning capabilities that can identify file upload vulnerabilities.
- Nikto: A web server scanner that detects vulnerabilities, including issues with file uploads.
2. Manual Testing Tools:
- Tamper Data or Browser Developer Tools: These allow you to intercept and modify HTTP/HTTPS requests, enabling you to test how the server handles unexpected or malicious input.
- cURL: A command-line tool that can be used to send files to the server, allowing you to test different parameters and payloads.
- Netcat: Useful for creating raw TCP or UDP packets to test server responses.
3. File Manipulation Techniques:
- Extension Manipulation: Change the file extension to see if the application blindly accepts any file type (e.g., uploading
malicious.php.jpgto see if the server processes it as a PHP file). - MIME Type Manipulation: Modify the MIME type of the file in the HTTP headers to test how the application validates it.
- Magic Number Manipulation: Some systems check the “magic numbers” at the start of files to determine their type. By changing these, you can potentially bypass filters.
- Content Manipulation: Embed malicious content, like scripts or shellcode, within accepted file types (e.g., adding a script within an image’s metadata).
4. Specialized Payloads and Lists:
- Payload Repositories: Websites or repositories like
PayloadsAllTheThingson GitHub provide a plethora of payloads tailored for file upload vulnerabilities.
5. Test for Directory Traversal:
Check if you can manipulate file paths during upload, potentially allowing you to upload files to unintended directories.
6. Test for Rate Limiting:
Use tools or scripts to send a large number of files in quick succession to see if the application can handle it and if there are rate limits in place.
7. Infrastructure Analysis:
- Directory Listing: Check if the directory where files are uploaded has directory listing enabled. This could expose all uploaded files to anyone.
- Permissions: Analyze file and folder permissions to ensure that uploaded files don’t have excessive privileges, such as being executable.
8. Security Misconfiguration:
Check if security headers, CORS policies, or other configurations can be abused in the context of file uploads.
9. Additional Testing Techniques:
- Third-party Libraries and Plugins: If the application uses third-party components for file uploads, research known vulnerabilities or misconfigurations associated with them.
- Check for Data Leakage: After uploading, check if any internal server details, errors, or paths are leaked, which can give insights to an attacker.
10. Continuous Monitoring and Logging:
Implement monitoring solutions to keep an eye on upload directories and traffic. Unusual spikes or patterns can be indicative of an attack.
11. Stay Updated:
Regularly check platforms like the National Vulnerability Database (NVD) or security forums to stay informed about new vulnerabilities or techniques related to file uploads.
12. External Services:
Consider using cloud services like VirusTotal to scan uploaded files for known malware signatures.
By employing a combination of these tools and techniques and regularly auditing your systems, you can ensure that your file upload features remain a strength, not a vulnerability. Remember, security is a continuous process, not a one-time task!
Conclusion
In the expansive realm of web application security, file upload vulnerabilities stand out as a critical area of concern. These vulnerabilities, often arising from oversights in design, configuration, and validation, can serve as entry points for attackers, potentially leading to devastating consequences like data breaches, system compromises, and reputational damage.
However, the digital landscape isn’t all doom and gloom. By understanding the intricacies of file upload attacks, the potential impacts, and the strategies to defend against them, organizations can fortify their defenses, ensuring that their web applications remain secure and trustworthy. Tools and techniques, both automated and manual, play a pivotal role in identifying, testing, and mitigating these vulnerabilities.
But beyond tools and techniques, it’s the mindset that counts. A proactive, informed, and continuous approach to security, combined with a commitment to user safety, is the hallmark of a robust digital platform. As we navigate the ever-evolving world of cyber threats, let’s remember that vigilance, knowledge, and action are our best allies.
In the end, the digital world, much like the physical one, has its challenges and risks. But with the right knowledge, tools, and practices, we can ensure that our online spaces are just as safe, if not safer, than our offline ones.
Stay safe, stay informed, and keep those digital drawbridges up!
1 Comment
Well explained