Hey there! Ever been curious about what happens behind the scenes when you click around on a website? Or more importantly, have you ever wondered about the ‘dark side’ of the web? By that, I mean, how might someone exploit a website to gain unauthorized access or carry out malicious activities? Well, that’s what we’re going to dive into today!
I’m going to introduce you to the world of WebApp Penetration Testing – a practice that helps us understand and find the weak points in web applications. We’ll be using a guide from the good folks at OWASP to help us understand the most common risks.
Now, you might be wondering, ‘what’s OWASP?’ Well, OWASP, short for Open Web Application Security Project, is an online community that produces articles, methodologies, documentation, tools, and technologies in the field of web application security. They’re pretty much the Jedi Knights of web security. One of their most notable contributions is the ‘OWASP Top 10’, which is a powerful awareness document for web application security that represents a broad consensus about the most critical security risks to web applications.
In this article, we’ll dissect the OWASP Top 10, understand what each one means, and I’ll show you how to apply this knowledge in penetration testing. We’ll walk through the set-up process, the testing, and even how to make sense of the results.
What is OWASP?
You bet! So, let’s talk about this group called OWASP. No, they’re not a secret society or a part of the Avengers, although what they do is pretty super!
The name OWASP stands for the Open Web Application Security Project. They are a non-profit organization that’s all about making the online world a safer place. Think of them like a digital neighborhood watch, but instead of patrolling streets, they patrol the web, finding weak spots in websites and web applications and telling the world how to fix them.
The cool thing about OWASP is that they are a community of security enthusiasts, professionals, and experts who have teamed up to combat the bad guys of the web. They’re like an open-source project, meaning that anyone can access their materials, contribute, and participate in their activities.
But, what makes OWASP a big deal? Well, they’ve put together something called the ‘OWASP Top 10’. It’s like a ‘most wanted’ list, but instead of criminals, it lists the top security risks that websites face. From injection attacks to broken authentication, the Top 10 is a rundown of the most serious and common problems that could make a website vulnerable to attacks.
In a nutshell, OWASP is like a guardian angel for web applications. Through their work, they provide essential knowledge and tools that help folks like us uncover vulnerabilities and make the web a safer place. Throughout this article, we’ll dive deep into their Top 10, so you can understand these threats, and more importantly, learn how to guard against them!
OWASP Top 10
Now that you’ve got an idea about who OWASP is, let’s talk about this infamous ‘Top 10’ list I mentioned. The OWASP Top 10 is more than just a playlist of greatest hits in the world of security risks. It’s actually a roadmap that guides us on the journey of understanding and mitigating the biggest security threats web applications face today.
Updated every few years, this list isn’t some wild guesswork. It’s created based on cold, hard data collected from various security organizations around the globe. Whether you’re a newbie dipping your toes into cyber security or a seasoned professional, the Top 10 is the compass you need to prioritize your defensive strategies.
The current edition of the OWASP Top 10 – as of the latest 2021 update – serves up some familiar threats along with a few new ones. I could list them out, but why not show you instead? Check out the image below to get a clear picture of the current rogues’ gallery of web application security risks.

Cool, right? Now, let’s buckle up and get ready to dive deep into each of these risks one by one. Understanding each threat will arm us with the knowledge to effectively counter them. Onward to safer web applications!”
Why Is OWASP Top 10 Used?
Okay, let’s talk about why we use the OWASP Top 10. I mean, sure, it sounds cool and all, but what’s the big deal? Why should we bother about it?
First off, the Top 10 isn’t just a random list. It’s like the “Billboard Hot 100” for security vulnerabilities— these are the top threats that web applications face today. So, if you’re in the business of keeping web applications safe (which, if you’re reading this, you probably are), it’s crucial to know what you’re up against.
Next, think of the OWASP Top 10 as your cheat sheet for understanding web app security. It’s like having the answers to a test before you even take it. Each vulnerability listed comes with detailed information about what it is, how it works, and most importantly, how you can prevent or mitigate it. It’s like having an instruction manual for defeating these cyber threats.
Also, the Top 10 isn’t just useful for cyber defenders like us. It’s a great tool for raising awareness about web application security, even for non-tech folks. Businesses can use the Top 10 to understand the risks they face and make informed decisions about where to invest in security.
Lastly, remember that the Top 10 is backed by data from security organizations worldwide, so it’s not based on speculation or theory. These are real threats causing real damage out there.
So, the OWASP Top 10 isn’t just a list— it’s a weapon, a guide, an instruction manual, a cheat sheet, and an awareness tool all rolled into one. It helps us keep web applications safe and the bad guys at bay. Now that’s what I call a big deal!
Ready to take a closer look? Let’s dive into each of these Top 10 vulnerabilities and see what makes them tick.
Deep Dive into the OWASP Top 10
Alright, it’s time to dive head-first into the deep end of the OWASP Top 10. Buckle up, because we’re about to meet some of the web’s most notorious vulnerabilities. I’ll give you a breakdown of each one, explaining what it is, how it can harm a web application, and how we can safeguard against it. Here we go:
1. Broken Access Control

Let’s talk about Broken Access Control. It’s like having a bouncer at a club who’s sleeping on the job. Anyone and everyone can waltz right into the VIP section without an invite.
Access control, in the world of web applications, is all about who can do what. It defines what data or functions a user can access and modify. For instance, an ordinary user might be allowed to view their own profile, but they shouldn’t be able to view other users’ profiles or, heaven forbid, delete them!
Now, when these rules aren’t properly enforced, we say that the access control is ‘broken’. This lets attackers run wild, doing things they have no business doing. They might access data they shouldn’t, modify data they shouldn’t, or even carry out administrative functions. Imagine someone gaining access to your account, changing your password, and locking you out. Not cool, right?
To prevent this kind of scenario, you need to make sure that your web application’s access control rules are tight. Restrict what each user and role can do, and enforce these restrictions consistently across your application.
In our journey through the OWASP Top 10, Broken Access Control is a biggie. It’s like a VIP pass into the underbelly of your web application, and you don’t want the wrong person getting their hands on it. So, make sure your bouncer is wide awake and only letting in the people who have an invite!
Next, we’ll delve into another vulnerability on our list. Let’s keep going!
2. Cryptographic Failures

Alright, let’s put on our detective hats and talk about Cryptographic Failures. This one’s all about secrets and how we protect them. It’s like those old spy movies where someone intercepts a secret message because it wasn’t properly coded.
So what does ‘cryptographic’ mean? It’s all about encoding information so only authorized parties can read it. Think of it as a secret language between two parties. Now, when a web application doesn’t properly use cryptography to protect data, it’s like a detective leaving his secret messages out in the open for anyone to see.
In the context of web applications, Cryptographic Failures can be disastrous. Imagine sending your credit card details over the internet, but instead of being securely encrypted, it’s sent in plain text. Any cyber crook eavesdropping on the connection could snatch up that info and go on a shopping spree.
Now, how do we avoid this? It’s all about using tried-and-true cryptographic practices. This includes using up-to-date protocols, strong keys, and ensuring data in transit and at rest is properly encrypted. And remember, it’s not just about using cryptography, it’s about using it correctly.
So, Cryptographic Failures is the second stop on our tour of the OWASP Top 10. It’s all about keeping those secrets, secret. Next up, we’ve got another big player in the web vulnerability world. Let’s keep the momentum going!
(Note: As of the last OWASP Top 10 list update in 2021, “Cryptographic Failures” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
3. Injection

Time to talk about Injection, my friend. This is like the sneaky pickpocket of web vulnerabilities, and unfortunately, it’s pretty common.
Imagine you’re having a conversation, and suddenly someone interrupts you to say something completely off-topic. It’s kind of annoying, right? Well, an Injection attack is sort of like that interruption, but with much more serious consequences.
In the digital world, injection happens when an attacker slips malicious data, or ‘input’, into a web application. This input then gets processed, or ‘interpreted’, by the application as part of a command or query. And boom, before you know it, the attacker is running the show. They can read your data, modify it, or even delete it. In some cases, they can take control of the whole system.
It’s like a burglar tricking the owner into opening the door, and then making themselves at home. Not a great scenario, huh?
But there’s good news. We can prevent Injection attacks. How? By treating all user input with suspicion. We need to thoroughly validate, filter, and sanitize anything and everything a user puts into our web application. This way, even if an attacker tries to sneak in some nasty code, our application won’t execute it.
So, that’s Injection in a nutshell. It’s the third stop on our OWASP Top 10 journey, and it’s one that demands our full attention. Let’s stay alert and keep moving!
4. Insecure Design

Next up on our OWASP tour is Insecure Design. Now, this one’s a bit like building a house with a beautiful front door, top-notch security systems, and then leaving a gaping hole in the back wall. Not exactly secure, is it?
Insecure Design isn’t about one specific flaw or error. Instead, it’s all about the bigger picture. It’s what happens when security is an afterthought, rather than a central part of the design and development process.
Imagine you’re creating a web application. You’ve got all these cool features and a super user-friendly interface. But if you’ve not baked security into your design from the start, you could be leaving your application wide open to a host of vulnerabilities. This might be things like not implementing proper user authentication, failing to encrypt sensitive data, or not including mechanisms to detect and respond to security incidents.
Insecure Design is a bit like an invitation to attackers. It says, “Hey, we didn’t think too much about security when building this, so come on in!” But don’t worry, we can fix this.
How? By adopting a ‘security by design’ approach. This means we incorporate security considerations right from the get-go, making it a core element of our application design and development process. It’s about proactively planning for security, rather than reactively plugging holes.
So, Insecure Design is the fourth stop on our OWASP Top 10 journey, and it’s a crucial one. By making security a central part of our design, we can build stronger, safer web applications. Let’s keep this security train rolling, shall we?
(Note: As of the last OWASP Top 10 list update in 2021, “Insecure Design” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
5. Security Misconfiguration

Alright, next on our OWASP Top 10 tour is Security Misconfiguration. This one’s a bit like buying the best security system for your home but forgetting to turn it on, or worse, not setting it up properly so that it leaves your back door wide open. Not exactly the best use of a security system, right?
In the world of web applications, Security Misconfiguration can happen in all sorts of ways. It could be that the application is running on a server with default settings (a big no-no, since attackers are well aware of these!). It could be that the application is using outdated software, or software with known vulnerabilities that haven’t been patched. Or it could be as simple as leaving detailed error messages switched on, giving attackers valuable information about your system.
The result? Well, an attacker could gain unauthorized access to your system, steal data, or even take control of the whole server. It’s like rolling out a red carpet for cyber crooks.
But don’t despair, because this is totally preventable. The key is to have a robust configuration process and to keep on top of it. Regularly update and patch software, change default settings, turn off unnecessary features, and make sure error messages don’t give away too much info.
So, that’s Security Misconfiguration. It’s the fifth pit stop on our OWASP Top 10 journey and it’s a reminder that even the best security measures are only as good as how they’re configured. Let’s tighten up those settings and keep marching forward!
6. Vulnerable and Outdated Components

Let’s talk about Vulnerable and Outdated Components. Imagine you’re driving a car with an old, leaky fuel tank. Sure, the car still runs, but it’s a disaster waiting to happen.
In the world of web applications, using vulnerable or outdated components is a similar story. You see, most web applications today aren’t built from scratch. They’re a mix of custom code and pre-built components like libraries, frameworks, and other software modules. Now, this isn’t necessarily a bad thing. These components can save time and effort, but there’s a catch – they need to be kept up-to-date and secure.
Here’s the deal: when a component is old or has known vulnerabilities, it’s like an open invitation to attackers. They can exploit these weaknesses to break into your web application or cause all sorts of mischief.
And let’s be clear: we’re not just talking about obscure, barely-used components here. Even some of the most popular components have known vulnerabilities. This makes updating and securing your components a top priority.
So how do we combat this? A few ways. One, regularly update all your components to their latest secure versions. Two, remove any components you’re not using – they’re just unnecessary risk. Three, be aware of the security implications and vulnerabilities of the components you use.
That’s it for Vulnerable and Outdated Components, our sixth pit stop on the OWASP Top 10 journey. This is a key reminder to keep our web applications up-to-date, because driving with a leaky fuel tank is a risk we don’t want to take.
(Note: As of the last OWASP Top 10 list update in 2021, “Vulnerable and Outdated Components” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
7. Identification and Authentication Failures

Alright, it’s time to dive into Identification and Authentication Failures. This one’s like a nightclub where the bouncer just waves everyone in, no ID check, no guest list, nothing. As you can imagine, that’s a recipe for trouble.
In the realm of web applications, identification and authentication are critical. They’re how we know who’s who. Identification is about ensuring a user is who they claim to be (like checking an ID card), while authentication is about verifying that claim (like checking the ID against a guest list).
When these processes fail, it’s a big problem. It’s like leaving the door wide open for anyone to stroll in and cause mayhem. Attackers can pretend to be legitimate users, gain unauthorized access to sensitive data, or perform actions they shouldn’t be able to.
Imagine someone gaining access to your personal account, reading your private messages, making purchases, or even deleting your account. Not fun, right?
So, how can we prevent this? By ensuring robust identification and authentication mechanisms. This could involve strong password policies, multi-factor authentication, and rigorous session management, among other things.
So, that’s Identification and Authentication Failures, the seventh checkpoint in our OWASP Top 10 journey. It’s a crucial reminder that knowing who’s who is paramount in securing our web applications. Let’s keep the momentum going!
(Note: As of the last OWASP Top 10 list update in 2021, “Identification and Authentication Failures” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
8.Software and Data Integrity Failures

Next up on our OWASP Top 10 tour is Software and Data Integrity Failures. This one’s like buying a book, only to realize some pages are torn out and others are out of order. You’re missing vital information, and it’s just not making sense.
In the digital world, integrity is all about ensuring data and software are accurate, complete, and reliable. It’s about making sure no unauthorized changes are made and that everything is in its right place.
When integrity fails in a web application, it’s like a twisted game of Telephone – the message at the end doesn’t match the message at the start. Attackers can modify data, corrupt software, or disrupt systems. This could result in incorrect data being displayed, transactions being manipulated, or even systems failing altogether.
Imagine an e-commerce site where an attacker can change the prices of items in their favor. Or a social media site where they can alter other users’ posts. Not cool, right?
So, how do we prevent this? Well, there are a few methods. We can implement robust access controls to prevent unauthorized changes. We can use checksums and hashes to verify data hasn’t been tampered with. And we can employ secure coding practices to protect our software from corruption.
That’s Software and Data Integrity Failures for you – our eighth stop on the OWASP Top 10 tour. It’s a vital reminder that to trust our data and software, we need to ensure their integrity. Now, let’s keep this show on the road!
(Note: As of the last OWASP Top 10 list update in 2021, “Software and Data Integrity Failures” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
9. Security Logging and Monitoring Failures

Ready for the ninth stop on our OWASP Top 10 tour? Let’s talk about Security Logging and Monitoring Failures. This one’s like owning a state-of-the-art home security system, but never bothering to check if it’s recording or ignoring the alerts it sends. Not exactly making the most of your security, right?
Security logging and monitoring are like the eyes and ears of your web application’s security system. They’re how you know what’s happening and when it’s happening. Logs record events in your application, and monitoring systems are there to alert you to anything unusual.
When logging and monitoring fail or aren’t used properly, it’s like putting on a blindfold and earplugs. You’re unaware of what’s going on. An attacker could be prancing around in your system, and you wouldn’t have a clue until it’s too late.
Now, let’s get this straight: good logging and monitoring won’t necessarily prevent an attack, but they can alert you when one is happening. That means you can respond quickly, limit the damage, and catch the culprit.
Preventing this issue involves setting up robust logging and monitoring practices. Ensure your logs capture critical information, store them securely (and remember, they can contain sensitive data too), and have a system in place to analyze them and alert you to suspicious activity.
So, there you have it: Security Logging and Monitoring Failures, our ninth pit stop on the OWASP Top 10 journey. It’s a solid reminder that knowing what’s happening in your web application is as crucial as securing it in the first place. Let’s keep those eyes and ears open and continue our journey!
(Note: As of the last OWASP Top 10 list update in 2021, “Security Logging and Monitoring Failures” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
10. Server-Side Request Forgery (SSRF)
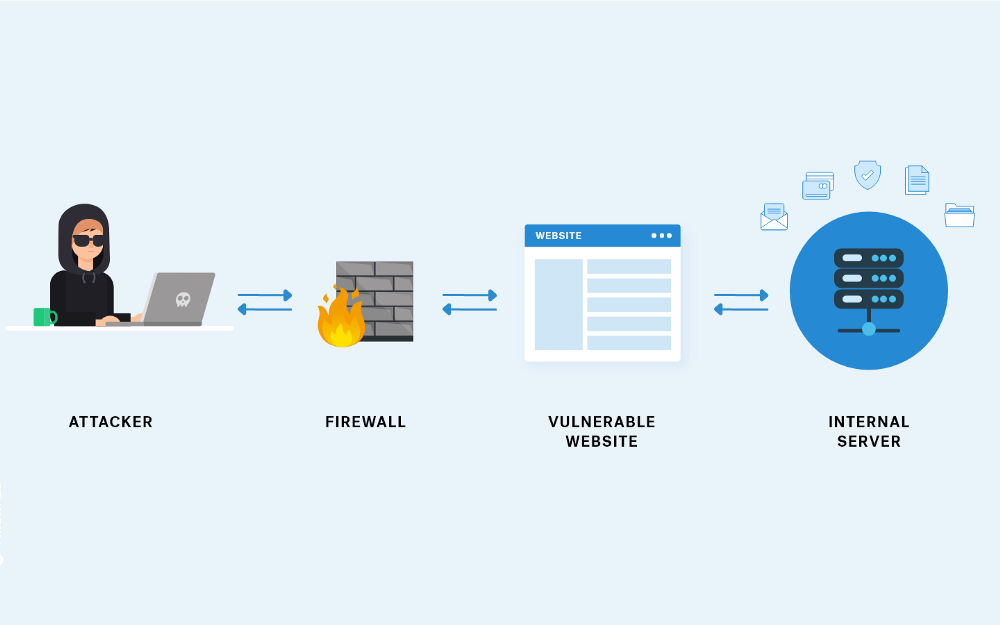
Last but certainly not least on our OWASP Top 10 tour is Server-Side Request Forgery, commonly known as SSRF. It’s like a sneaky imposter pretending to be a trusted insider, tricking the guards to let them into the castle. It’s crafty, and it can be really damaging.
In a nutshell, SSRF is an attack where an attacker tricks the server into making requests that it shouldn’t. It might not sound too bad, but think about it this way: the server often has access to resources and systems that ordinary users or outside attackers don’t. By exploiting SSRF, an attacker can gain access to these resources.
Imagine a malicious actor using your server to send requests to an internal network, accessing sensitive data or interacting with internal services. Yeah, it’s as bad as it sounds.
The good news is, we’re not helpless against SSRF. Prevention strategies include input validation (make sure the server only makes legitimate requests), limiting server permissions (so even if an SSRF attack happens, it can’t do too much harm), and using allowlists for outbound connections (so the server can only connect to approved services).
So there we have it, Server-Side Request Forgery, the final stop on our OWASP Top 10 journey. It’s a powerful reminder of how even the server – the heart of our web application – can be manipulated if we’re not careful.
(Note: As of the last OWASP Top 10 list update in 2021, “Server-Side Request Forgery (SSRF)” is not specifically listed as one of the top 10 vulnerabilities. The above explanation, however, gives an understanding of what such a failure would entail.)
Setting Up for Penetration Testing
Alright, my friend, we’ve spent a lot of time talking about the dark side – all the nasty things that can go wrong with web application security. But now it’s time to flip the script and get proactive. That’s right, we’re diving into the exciting world of penetration testing!
Picture yourself as a kind of digital Sherlock Holmes. Your mission, should you choose to accept it, is to find and exploit vulnerabilities in a web application before the bad guys do. This isn’t about causing harm, though. Quite the opposite. It’s about shining a light on weaknesses so they can be patched up. This is what we call penetration testing, or ‘pen testing’ for short.
Setting up for pen testing isn’t just about downloading a bunch of tools and going wild. Oh no, there’s an art and science to this. It involves careful planning, methodical execution, and thorough documentation. Not to mention ethical considerations and legal boundaries.
Before you get started, you’ll need to define the scope of your testing. This means knowing exactly what you’ll be testing and what’s off-limits. The last thing you want is to accidentally take down a critical system or infringe on someone’s privacy.
Next up, you’ll need to gather your tools. There’s a vast array of pen testing tools out there, ranging from automated scanners to intricate manual testing tools. Some of the big names you’ll likely come across are OWASP ZAP, Burp Suite, and Metasploit, but the best toolkit depends on your exact needs and the nature of the application you’re testing.
But remember, these tools are just that – tools. They’re not a magic bullet. Successful pen testing requires a curious mindset, a deep understanding of how web applications work, and a good grasp of the OWASP Top 10 risks we’ve just covered.
Finally, and importantly, you should have permission to conduct your testing. Remember, unauthorized pen testing is illegal and unethical.
Alright, that’s our quick intro to setting up for pen testing. Buckle up, because our digital Sherlock Holmes journey is just beginning! In the next sections, we’ll delve deeper into the process and techniques of pen testing, guided by our trusty OWASP Top 10. Stay tuned!
Conducting Penetration Testing Based on OWASP Top 10
Alright, we’ve set the stage, prepared our tools, and donned our digital detective hat. Now, it’s showtime – let’s talk about conducting penetration testing based on the OWASP Top 10.
Think of the OWASP Top 10 as your roadmap. These are the most common security risks out there, and they’re a great starting point for your investigation. But remember, pen testing isn’t just about checking off a list. It’s about understanding how an application works, finding its weak spots, and figuring out how an attacker might exploit them.
First things first, you’ll want to explore the application. Get to know its ins and outs. How does it behave? What technologies does it use? What functionality does it offer? This is often called reconnaissance or ‘recon’ for short.
Now, with the OWASP Top 10 in mind, you’ll start probing for weaknesses. For example, you might test for injection vulnerabilities by trying to insert malicious input into data fields. Or you might try to manipulate access controls to see if you can view or change data you shouldn’t be able to.
Remember, each risk in the OWASP Top 10 is associated with a number of potential vulnerabilities. You’ll need to think creatively about how to test for each one. It’s a bit like a puzzle – and sometimes, you’ll need to think like an attacker to solve it.
Now, let’s say you’ve found a potential vulnerability. Don’t stop there. Try to exploit it. Can you use it to gain unauthorized access, expose sensitive data, or disrupt the application’s operation? The goal here isn’t to cause harm, but to understand the potential impact of the vulnerability.
Through all this, you should be keeping detailed records. Document your methods, your findings, any vulnerabilities you uncover, and their potential impact. This will be crucial for reporting your findings and suggesting mitigations later on.
Alright, that’s a high-level look at conducting penetration testing based on the OWASP Top 10. But remember, this is just the beginning. Pen testing is a deep field, and there’s always more to learn. So keep exploring, keep testing, and keep learning. Good luck, detective!
OWASP Top 10 Limitations
Now, let’s take a moment to talk about the limitations of the OWASP Top 10. Like any tool or framework, it’s not without its quirks. So, here are a few things to keep in mind:
- Not an exhaustive list: The OWASP Top 10 is a fantastic starting point for understanding common web application vulnerabilities. However, it doesn’t cover every possible vulnerability out there. It’s more like a highlight reel rather than an exhaustive encyclopedia.
- Lacks specificity: The Top 10 provides a general overview of each vulnerability, but it doesn’t dive deep into specific attack techniques or variations. It’s more about raising awareness and pointing you in the right direction for further research.
- Varied applicability: The vulnerabilities listed in the Top 10 may not be equally applicable to all web applications. The risk profile of each application is unique, and certain vulnerabilities may be more or less relevant depending on the specific context.
- Not a substitute for thorough testing: The Top 10 should be seen as a starting point, not the endpoint, for security testing. It’s crucial to conduct comprehensive and customized assessments tailored to your specific application and environment.
- Limited frequency of updates: The OWASP Top 10 is typically updated every few years, which means it may not always reflect the most current threats and vulnerabilities in the ever-evolving world of web application security. Staying updated with the latest security trends and incorporating them into your testing practices is essential.
Despite these limitations, the OWASP Top 10 remains an invaluable resource for understanding and prioritizing web application security risks. It helps raise awareness, guides security initiatives, and provides a common language for discussions in the industry.
So, while it’s important to acknowledge its limitations, it’s equally important to utilize the OWASP Top 10 as a foundational tool while complementing it with additional research, testing techniques, and emerging security best practices. Stay curious and keep pushing the boundaries of your web application security knowledge!
Conclusion
In conclusion, the OWASP Top 10 is an essential resource for web application security. It serves as a roadmap, guiding us through the most critical security risks and vulnerabilities that we need to be aware of and protect against. By understanding these risks and learning how to mitigate them, we can strengthen the security of our web applications and keep them safe from malicious attacks.
Throughout this article, we’ve explored each of the OWASP Top 10 vulnerabilities, from Injection to Server-Side Request Forgery (SSRF). We’ve seen how these vulnerabilities can jeopardize the confidentiality, integrity, and availability of our applications and learned strategies to defend against them.
However, it’s crucial to remember that the OWASP Top 10 is not a one-size-fits-all solution. It’s a starting point, a foundation, but it doesn’t cover all possible vulnerabilities or address every unique scenario. To ensure comprehensive security, we must supplement our knowledge with continuous learning, customized testing, and staying up-to-date with emerging security trends.
Penetration testing, based on the OWASP Top 10, allows us to proactively identify vulnerabilities and strengthen our defenses. By adopting a curious mindset, utilizing appropriate tools, and following ethical guidelines, we can uncover weaknesses before attackers do, giving us the opportunity to patch and protect.
While the OWASP Top 10 has its limitations, such as not being exhaustive or always up-to-date, it remains a valuable resource and a shared language for the web application security community. It serves as a reminder of the importance of prioritizing security and staying vigilant in an ever-changing threat landscape.
So, armed with the knowledge gained from the OWASP Top 10, let’s continue to explore, innovate, and build web applications that prioritize security. Together, we can create a safer online environment for users and defend against the ever-evolving threats that lurk in the digital realm.
