Hello there! I’m excited to guide you through the wonderful world of Nmap. Now, you might be asking, “What is Nmap?” Well, it’s a super handy tool that’s widely used by system and network administrators, cybersecurity professionals, and even enthusiasts like you and me, to explore and audit networks.
Nmap, which stands for Network Mapper, is a free and open-source tool that allows us to discover devices on a network, find open ports, and determine what services and versions are running on those ports. It’s like a Swiss Army Knife for anyone wanting to get a deeper understanding of their network environment or explore the security of a system.
Why use Nmap, you ask? Well, its usefulness is pretty vast. It’s great for tasks such as network inventory, managing service upgrade schedules, monitoring host or service uptime, and even for penetration testing. It’s an all-around awesome tool to get a closer look at the digital landscape around us.
Throughout this tutorial, I’ll be showing you how to get started with Nmap, help you understand some of the basics, guide you through common and advanced scanning techniques, and even explain how to read and understand the output. I’ll also share some tips and tricks and important legal and ethical considerations you need to bear in mind when using Nmap.
So, ready to embark on this exciting journey? Let’s dive in!
Getting Started with Nmap

Alright, before we jump into the good stuff, let’s make sure your system is ready to roll with Nmap. It’s pretty versatile, so it doesn’t ask for much.
System Requirements
First thing, your device! Nmap works on a whole range of systems. So whether you’re a Windows fan, a lover of Linux, or an admirer of Apple’s MacOS, you’re in luck. It also runs on several other platforms like Solaris, FreeBSD, and even some flavors of IBM OS.
Now, about the system specs. Nmap is not a resource hog. It’s actually very light. Even your grandma’s old laptop could probably run it. So, as long as your machine can smoothly run your operating system, you should be good to go. But remember, if you plan to perform very large network scans, having more RAM could come in handy.
Storage? Again, Nmap’s got your back. You won’t need to clear out those vacation photos. The tool itself takes up minimal space, although if you’re going to store large scan results, make sure you’ve got some room to spare.
Internet connection? Of course, we need that. Especially when we’re scanning networks. But don’t worry, you don’t need lightning-fast speeds. Standard broadband connection would do just fine.
And finally, you need some curiosity and a hunger to learn! That’s the most important requirement. As long as you’ve got those, we’re ready to kick off our Nmap journey.
Installation on Various Platforms
Alright, now that we’ve got our system ready to roll, let’s move on to installing Nmap. I’ll guide you through the process for Windows, Linux, and MacOS. Don’t worry; it’s a pretty straightforward journey on all these platforms!
Windows
- Head over to the official Nmap download page (https://nmap.org/download.html). I’ll wait.
- Done? Cool! Now, you’ll see a bunch of links, but what you want is the one that says “Nmap Windows installer”. Click on it and let the download do its thing.
- Once the download is complete, just open up the file and follow the on-screen instructions. It’s as simple as installing any other program. When you get to the ‘Select Components’ section, make sure to check the box for ‘Npcap’ – it’s a nifty packet capture library that Nmap needs to run properly.
Linux
If you’re on a Linux system, installing Nmap can feel like a walk in the park. Most Linux distributions have Nmap in their package repositories, so you can use your package manager to install it. Here’s how:
- For Debian-based distros like Ubuntu, you can open a terminal and type in
sudo apt-get install nmap. It’ll ask for your password, so type that in, hit Enter, and let the magic happen. - If you’re a Fedora or CentOS user, the command is slightly different:
sudo dnf install nmap. - On Arch-based systems, you can use Pacman with
sudo pacman -S nmap.
MacOS
Mac users, you’re up! Your path is a bit different, but equally simple.
- First off, you’ll need to have Homebrew installed. It’s a package manager for MacOS, and it makes installing tools like Nmap a breeze. If you don’t have it yet, you can install it by pasting
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"in your terminal. - Once you’ve got Homebrew, installing Nmap is as easy as typing
brew install nmapinto your terminal and hitting Enter.
And that’s it, folks! Regardless of your operating system, you should now have Nmap up and running. Get ready, because we’re about to dive into the deep end of network exploration!
Understanding Nmap Basics

Alright, now that we’ve got Nmap installed, it’s time to cover some basic concepts. Trust me, this will make your life a whole lot easier when we start delving deeper. Buckle up, and let’s roll!
Understanding IP Addresses and Ports
Think of an IP address like your home address. It’s a unique label that identifies a device on a network. It’s how computers find each other to chat. There are two types of IP addresses: IPv4 (like 192.168.1.1) and IPv6 (a longer, more complicated one). For now, we’ll stick with IPv4 since it’s still the most common.
And ports? You can think of these like doors on a house. Each IP address (house) has thousands of ports (doors), and different services use different doors. For example, web servers typically use port 80 or 443. When we scan with Nmap, we’re basically knocking on these doors to see which ones are open.
The Role of TCP/IP in Nmap
TCP/IP is the backbone of the internet and stands for Transmission Control Protocol/Internet Protocol. It’s like the rules of the road for network traffic. Nmap uses these protocols to send different kinds of packets (think of packets like tiny digital messages) to target systems and interpret their responses. This gives us a lot of information about the network or system we’re scanning.
Basic Terminology
Here’s a quick breakdown of some terms you’ll hear a lot:
- Scan: This is when we use Nmap to probe a device or network. It’s like sending our digital scouts out to gather intel.
- Target: The device or network we’re scanning.
- Port: We already talked about this, but it’s good to hammer it home. These are like the doors or windows to a networked device.
- Packet: These are the tiny bits of information that get sent back and forth when we’re scanning.
- Payload: This is the actual information carried within a packet. Like the letter in an envelope.
- Script: A mini program we can use with Nmap to automate specific tasks. We’ll get more into this later!
And that’s it for the basics! Understanding these concepts is super important for making the most out of Nmap.
Common Nmap Scanning Techniques
Now we’re getting to the fun part! Scanning with Nmap. Remember, Nmap is like a Swiss Army knife, and each scanning technique is like a different tool in that knife. Each one has its own strengths and is better suited for certain situations. So let’s dive in and explore some of the most common ones.
TCP Connect Scan
This is the most basic type of scan and the default one when you’re running Nmap as a regular user (i.e., without superuser or ‘sudo’ privileges). In this scan, Nmap tries to establish a full TCP connection with each target port. It’s like ringing every doorbell at a house to see which ones get answered. You do this scan by typing nmap -sT <target>.
SYN Scan
Also known as the “half-open” scan, this is the default scan if you’re running Nmap as a superuser. Here, Nmap only sends the initial SYN packet of the TCP handshake, and if it gets a SYN/ACK packet back, it knows the port is open. It’s faster and less likely to be logged than the TCP Connect scan. This is done by typing nmap -sS <target>.
UDP Scan
This scan is used to check for open UDP ports, which are often used by services like DNS and DHCP. This is a slow scan because closed UDP ports don’t always respond with a packet. But if you’ve got the time, it can give you a more complete picture of a target’s open ports. You can initiate a UDP scan by typing nmap -sU <target>.
NULL, FIN, and Xmas Scans
These are more stealthy scans that can sometimes slip past less sophisticated firewalls and intrusion detection systems. They work by sending unusual packets and seeing how the target responds. Keep in mind, though, that they only work against systems that use unsophisticated TCP stack implementations. You can do these scans by typing nmap -sN <target>, nmap -sF <target>, and nmap -sX <target> respectively.
ACK Scan
This type of scan can be used to determine if a firewall is stateful or not – in other words, if it keeps track of connections over time. It won’t help you find open ports, but it can provide useful info about a target’s firewall. This is done by typing nmap -sA <target>.
So there you have it! Those are the basic scanning techniques you’ll use most often. Remember, each one has its own strengths and is suited to different situations.
Discover: JavaScript Enumeration: Uncovering Hidden Vulnerabilities in Web Applications
Nmap Scripting Engine (NSE)
Alright, we’re ready to kick things up a notch and delve into one of the coolest parts of Nmap – the Nmap Scripting Engine, or NSE for short. Imagine if your Swiss Army knife could suddenly transform into a whole toolbox. That’s what the NSE is for Nmap.
Understanding NSE
The NSE allows you to use scripts to automate a wide range of networking tasks. These scripts can do anything from advanced version detection to checking for known vulnerabilities, and even predicting what an operating system might be. Nmap comes with a ton of pre-written scripts (around 600 last time I checked), and they’re all ready to help you gather more information about your targets.
Using Basic Scripts
So, how do we use these scripts? It’s pretty straightforward. Once you’ve identified the script you want to use, you simply add --script=<script name> to your Nmap command.
For example, say you want to use the ‘http-title’ script, which fetches the title of the default web page of a target. You would run: nmap --script=http-title <target>. The result would give you not only the standard Nmap scan output, but also the title of the web page, if there’s one available.
Writing Custom Scripts
Now, here’s where things get really interesting. If the built-in scripts aren’t enough, you can write your own! NSE scripts are written in the Lua programming language. I won’t go into the details here – that’s a whole different tutorial – but with some basic programming knowledge, you can customize Nmap to do almost anything you want.
In summary, the NSE takes Nmap from being a powerful scanning tool to a versatile network exploration and security auditing powerhouse. As we continue this tutorial, we’ll be using the NSE more and more to gather detailed info about our targets. So stay tuned! There’s plenty more excitement ahead.
Advanced Nmap Techniques

Now that you’ve got a handle on the basics and have dipped your toes into the Nmap Scripting Engine, let’s dive into some advanced techniques. This is where we go from knocking on doors to peering through windows and checking out the floor plan. Ready? Let’s go!
OS Detection
One of the awesome things Nmap can do is predict the operating system of a target. It does this by looking at things like how the target responds to certain packets or the speed at which it responds. To perform OS detection, use the -O option like so: nmap -O <target>. Just remember, for this to work, you need to be running Nmap as a superuser.
Version Detection
Nmap can also try to determine what version of a service is running on an open port. This can be really useful for finding potential vulnerabilities that apply to specific versions. To perform version detection, use the -sV option: nmap -sV <target>.
Idle Scan
This is a more complex and stealthy technique where Nmap uses a “zombie” host to scan a target. The idea is to mask your IP address during the scan, which can be useful in certain penetration testing scenarios. The command for this is nmap -sI <zombie host IP> <target>.
Timing and Performance
Nmap allows you to control the timing and performance of your scans. This can help you balance speed, accuracy, and stealth. There are six timing templates you can use, from paranoid (-T0, very slow and stealthy) to insane (-T5, very fast but loud and likely to be noticed). So, if you need to scan quickly, you might use nmap -T4 <target>. But remember, the faster you go, the more likely you are to be detected and the higher the chance of errors.
Decoy Scanning
Another technique for hiding your tracks is to use decoy scanning. This involves spoofing other IP addresses along with your own to make it harder for the target to know who’s really scanning them. Use it like this: nmap -D <decoy1,decoy2,etc.> <target>.
And there you have it! A quick tour of some of Nmap’s advanced techniques. Remember, with great power comes great responsibility, so always make sure you have permission to scan any network or device.
Understanding Nmap Output
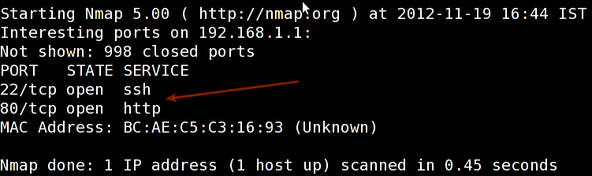
So, you’ve done a bunch of scans, sent out packets, poked around some ports – and now you’ve got a screen full of text. What now? Let’s take a deep breath and dive into understanding Nmap output.
Reading Basic Scan Output
When you run a basic scan, Nmap gives you an output that looks a little like this:
Starting Nmap at 2023-07-16 09:22 UTC
Nmap scan report for <target>
Host is up (0.00045s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
80/tcp open http
443/tcp open httpsHere’s how to read it:
- Starting Nmap at 2023-07-16 09:22 UTC: This is the timestamp of when you started the scan.
- Nmap scan report for : This tells you which target this report is for.
- Host is up (0.00045s latency): This means the target is online and responding, and it took 0.00045 seconds for it to respond.
- Not shown: 999 closed ports: This is telling you how many ports were scanned but didn’t respond, meaning they’re probably closed.
- PORT STATE SERVICE: This is the beginning of the list of open ports and what services they’re likely running.
- 80/tcp open http: This is telling you that port 80 is open and it’s likely running an HTTP service (i.e., a web server).
Understanding More Complex Output
Some scans, especially those using Nmap Scripting Engine (NSE), might give you more complex output. But don’t worry! It’s just giving you more detailed information. Each script will generate its own kind of output, and you can usually find documentation on how to read it in the script’s description or in the Nmap Scripting Engine documentation.
Errors and Warnings
Occasionally, Nmap might run into problems during a scan. If it does, it’ll let you know with error and warning messages. These can be caused by all sorts of things, like network interruptions, firewalls blocking scans, or just invalid command syntax. If you see an error, don’t panic – just read the message carefully and it’ll usually give you a clue about what went wrong.
And that’s the basics of reading Nmap output! Remember, practice makes perfect, so don’t be afraid to run scans and dive into the results.
Tips and Tricks for Effective Use of Nmap
Alright, you’ve made it this far and you’re ready for the home stretch. Now that we’ve covered all the basics, let’s talk about some tips and tricks to get the most out of Nmap. This isn’t just a toolbox, after all. It’s a toolbox with secret compartments!
Combining Options
One of the most powerful features of Nmap is the ability to combine different options and scans in a single command. For example, you could perform an OS detection and version detection scan at the same time with nmap -O -sV <target>. This not only saves you time, but can also give you a more comprehensive view of your target.
Pinging a Range of IP Addresses
Need to see which hosts are up in a specific IP range? No problem. Nmap can handle that. You can ping a range of IP addresses by using the -sn option (which just does a ping scan and nothing else) and specifying your IP range. For example, nmap -sn 192.168.1.1-100 would ping all the IPs between 192.168.1.1 and 192.168.1.100.
Scanning Multiple Targets at Once
Nmap can scan multiple targets in a single command. You can do this by separating the targets with a space: nmap <target1> <target2>. This is great if you need to scan a group of specific hosts.
Using -v for More Verbose Output
If you find yourself wanting more information about what Nmap is doing during a scan, use the -v option. This makes Nmap more talkative and gives you extra details about the scan progress, packet details, and more.
Deciphering a Network with -sP
If you’ve just been dropped into a network and have no idea what’s on it, the -sP option is your best friend. It tells Nmap to ping every IP on a subnet to see if it’s up, and then give you a summary. For example, nmap -sP 192.168.1.0/24 would give you a list of all hosts up on the 192.168.1.x subnet.
Saving Output to a File
You can also save your scan results to a file for later analysis using the -oN option. For example, nmap -oN output.txt <target> will save the scan results to a file named ‘output.txt’.
And there you go! These tips and tricks should help you use Nmap more effectively. Remember, Nmap is a powerful tool, so always use it responsibly.
Nmap commands
| Category | Command | Description |
|---|---|---|
| Basic Commands | ||
nmap <target> | Scan a single target | |
nmap <target1, target2, etc.> | Scan multiple targets | |
nmap -iL <list.txt> | Scan targets from a text file | |
nmap -p <port> <target> | Scan specific ports | |
| Discovery Commands | ||
nmap -sn <target> | Ping scan – no port scan | |
nmap -Pn <target> | No ping – assume the host is up | |
nmap -PR <target> | ARP ping scan (local networks) | |
nmap -n <target> | No DNS resolution | |
| Scan Techniques | ||
nmap -sT <target> | TCP connect scan | |
nmap -sS <target> | SYN scan | |
nmap -sU <target> | UDP scan | |
nmap -sA <target> | ACK scan | |
nmap -sN <target> | NULL scan | |
nmap -sF <target> | FIN scan | |
nmap -sX <target> | Xmas scan | |
nmap -sI <zombie host> <target> | Idle (zombie) scan | |
| Host Discovery | ||
nmap -PS <target> | TCP SYN ping | |
nmap -PA <target> | TCP ACK ping | |
nmap -PU <target> | UDP ping | |
nmap -PY <target> | SCTP INIT ping | |
| Service and OS Detection | ||
nmap -sV <target> | Service version detection | |
nmap -O <target> | OS detection | |
nmap -A <target> | OS and service detection | |
| Scripting Engine | ||
nmap --script <script> <target> | Run a specific script | |
nmap --script "default or (safe and discovery)" <target> | Run multiple scripts | |
| Output Options | ||
nmap -oN <filename> <target> | Save normal output to file | |
nmap -oX <filename> <target> | Save XML output to file | |
nmap -oG <filename> <target> | Save grepable output to file | |
| Timing and Performance | ||
nmap -T<0-5> <target> | Set timing template (higher is faster) | |
nmap --min-rate <number> <target> | Send a specific number of packets per second | |
nmap --max-retries <number> <target> | Set maximum number of port scan probe retries |
This table is by no means exhaustive, but it should cover most of the main commands and techniques you’ll use with Nmap. For a complete list of options and how to use them, refer to the official Nmap documentation.
Frequently Asked Questions (FAQs) About Nmap
1. Q: Is Nmap legal?
A: Yes, Nmap itself is legal software. However, how you use it can be illegal. Always make sure you have explicit permission to scan any network or device.
2. Q: Can Nmap hack systems?
A: No, Nmap is not a hacking tool. It’s a network scanner that can provide information about a network and its devices. However, the information it provides could be used in a hacking attempt. Again, always use Nmap responsibly.
3. Q: Can Nmap scans be detected?
A: Yes, they can. Network intrusion detection systems, firewalls, and even some software can potentially detect Nmap scans and flag them as suspicious activity.
4. Q: Does Nmap work on all operating systems?
A: Nmap works on many operating systems, including Windows, Mac OS, and many types of Linux. It also has a graphical user interface (GUI) called Zenmap that you can use if you prefer a visual interface.
5. Q: What is the Nmap Scripting Engine (NSE)?
A: The Nmap Scripting Engine (NSE) allows users to write scripts to automate a wide variety of networking tasks. These scripts are written in the Lua programming language.
6. Q: How can I learn Nmap?
A: There are many resources available to learn Nmap. The Nmap website itself has a lot of documentation, and there are also books, online tutorials, and even video courses available.
7. Q: What do I do if Nmap returns an error?
A: First, read the error message. It will usually give you a clue about what went wrong. If you’re still stuck, try searching for the error message online. There’s a good chance someone else has encountered it and found a solution.
8. Q: Why is Nmap slow?
A: There can be many reasons why an Nmap scan is slow. It could be due to network congestion, a slow target device, or firewall filtering. If you need to speed up your scans, try adjusting the timing options (-T<0-5>) or using faster scanning techniques like SYN scans (-sS).
9. Q: Can I use Nmap to scan for specific vulnerabilities?
A: Yes, you can. Nmap’s Scripting Engine (NSE) includes many scripts that can check for specific vulnerabilities.
10. Q: Can I use Nmap to monitor my own network?
A: Absolutely! Nmap is a great tool for monitoring your own network. You can use it to discover devices, check for open ports, see what services are running, and much more.
Conclusion
So, there we have it! A complete overview of Nmap – the go-to tool for network scanning. From its installation and basic usage, all the way to understanding its output and advanced scanning techniques, we’ve walked through everything you need to get started.
Remember, Nmap is more than just a single-function tool. It’s a versatile, powerful, and expandable network scanner that can help you discover what’s happening in your network environment. You can use it to uncover open ports, identify running services, or even detect vulnerabilities.
But the key to mastering Nmap lies in practice and exploration. The more you use it, the more comfortable you’ll become with its different features and functions. And don’t forget to refer back to this tutorial, or the extensive documentation available on the Nmap website, whenever you’re unsure about something.
Keep in mind, while Nmap is a great tool for securing and understanding your network, it also reminds us of the importance of ethical conduct. Always ensure you have the necessary permissions before scanning any network.
Keep exploring, keep learning, and remember – happy scanning!
